Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities
Por um escritor misterioso
Last updated 11 junho 2024
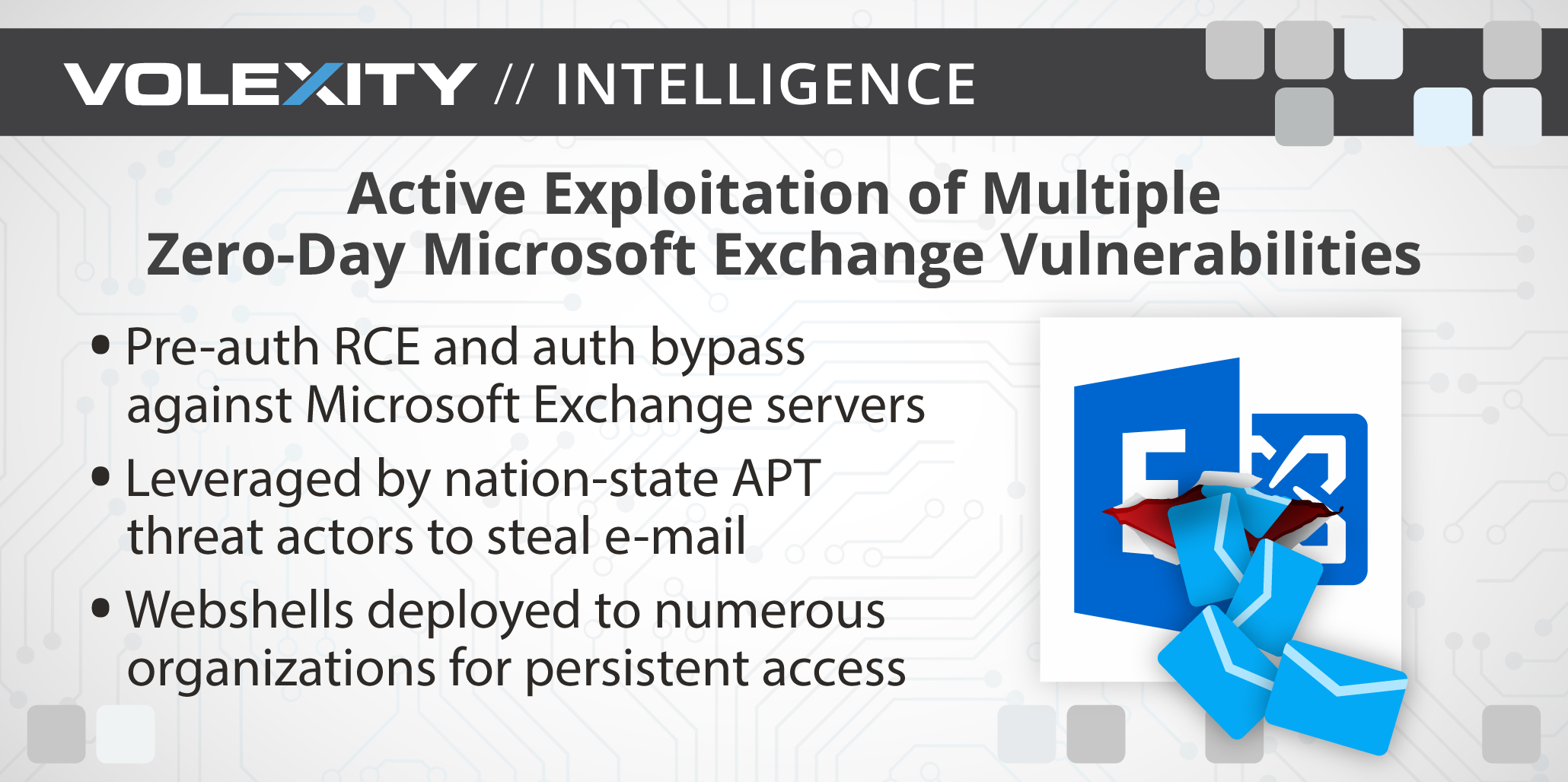
[UPDATE] March 8, 2021 – Since original publication of this blog, Volexity has now observed that cyber espionage operations using the SSRF vulnerability CVE-2021-26855 started occurring on January 3, 2021, three days earlier than initially posted. Volexity is seeing active in-the-wild exploitation of multiple Microsoft Exchange vulnerabilities used to steal e-mail and compromise networks. These attacks appear to have started as early as January 6, 2021. In January 2021, through its Network Security Monitoring service, Volexity detected anomalous activity from two of its customers' Microsoft Exchange servers. Volexity identified a large amount of data being sent to IP addresses it believed were not tied to legitimate users. A closer inspection of the IIS logs from the Exchange servers revealed rather alarming results. The logs showed inbound POST requests to valid files associated with images, JavaScript, cascading style sheets, and fonts used by Outlook Web Access (OWA). It was initially suspected the […]
Hunting down Microsoft Exchange 0-day

Defending Exchange servers under attack
Hunting down Microsoft Exchange 0-day
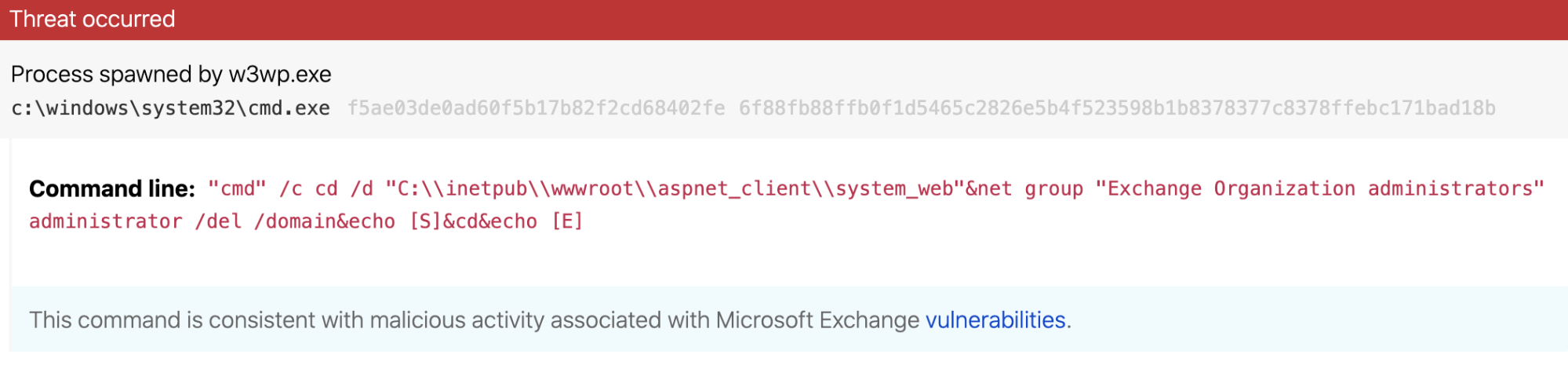
Microsoft Exchange exploitation: how to detect, mitigate, and stay calm

Detecting Microsoft Exchange Vulnerabilities - 0 + 8 Days Later…
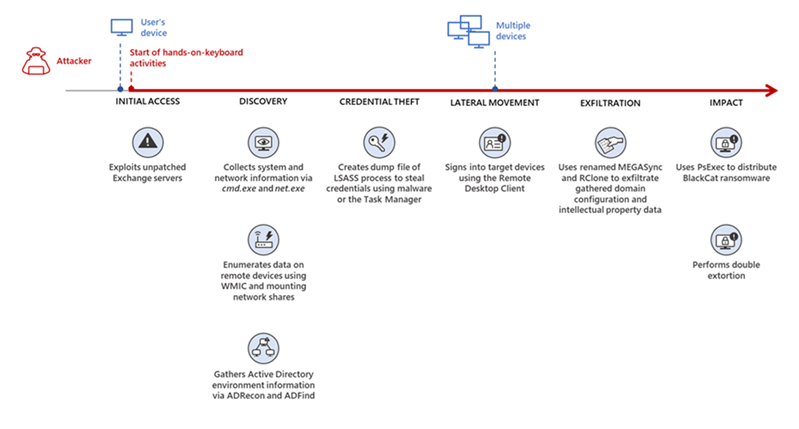
Microsoft Exchange Archives - Security Affairs
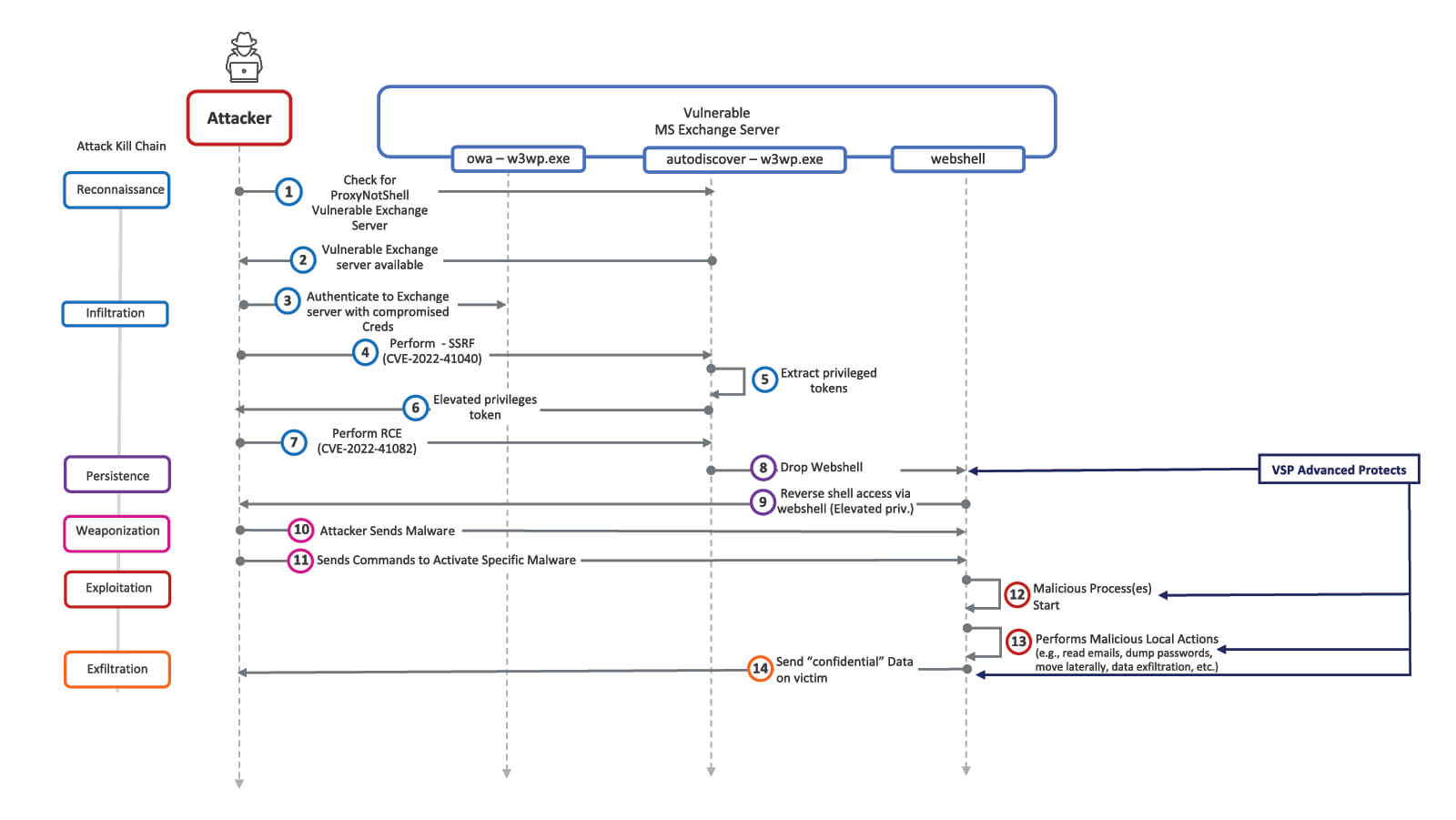
ProxyNotShell: A Zero-Day Microsoft Exchange Exploit
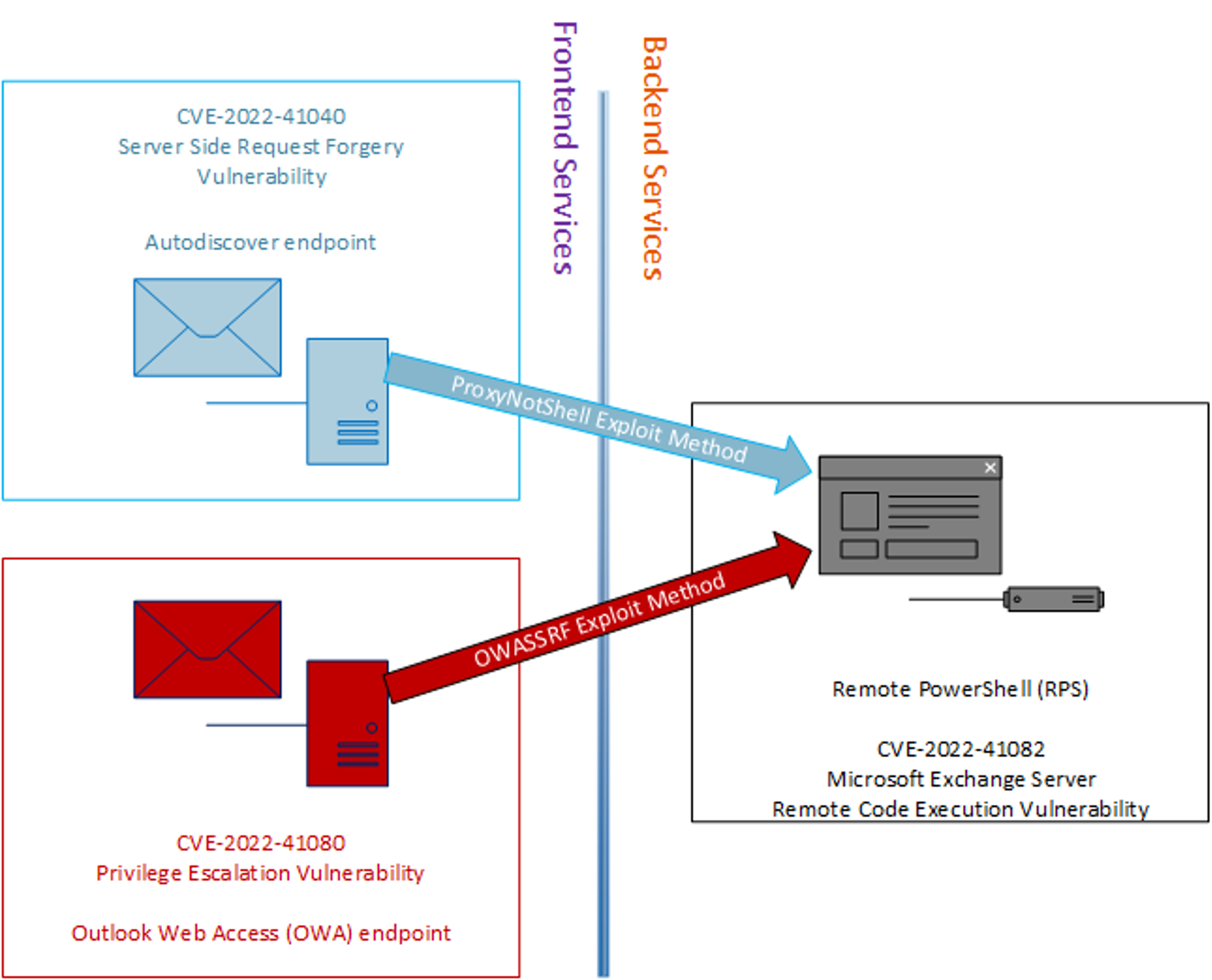
OWASSRF: CrowdStrike Identifies New Method for Bypassing ProxyNotShell Mitigations
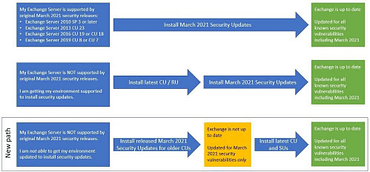
Microsoft Exchange 0-Day Vulnerabilities Mitigation Guide
Tactics, Techniques, and Procedures (TTPs) Used by HAFNIUM to Target Microsoft Exchange Servers

4 Zero-Day Bug in Microsoft Exchange Let Attackers
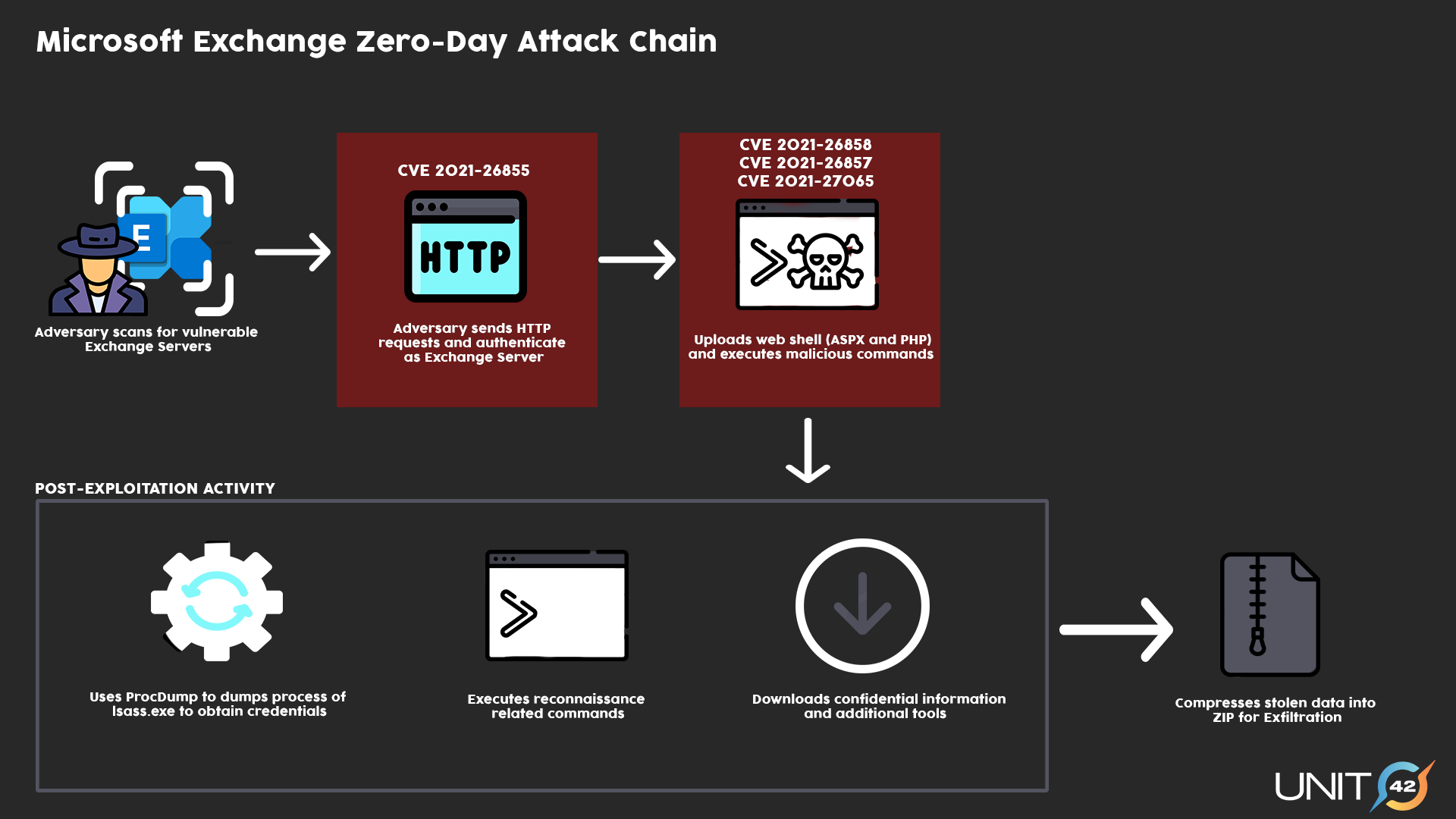
Threat Assessment: Active Exploitation of Four Zero-Day Vulnerabilities in Microsoft Exchange Server

Operation Exchange Marauder - SOC Prime
Collected Links For Hafnium – March 2021 Exchange Security Issue - 250 Hello
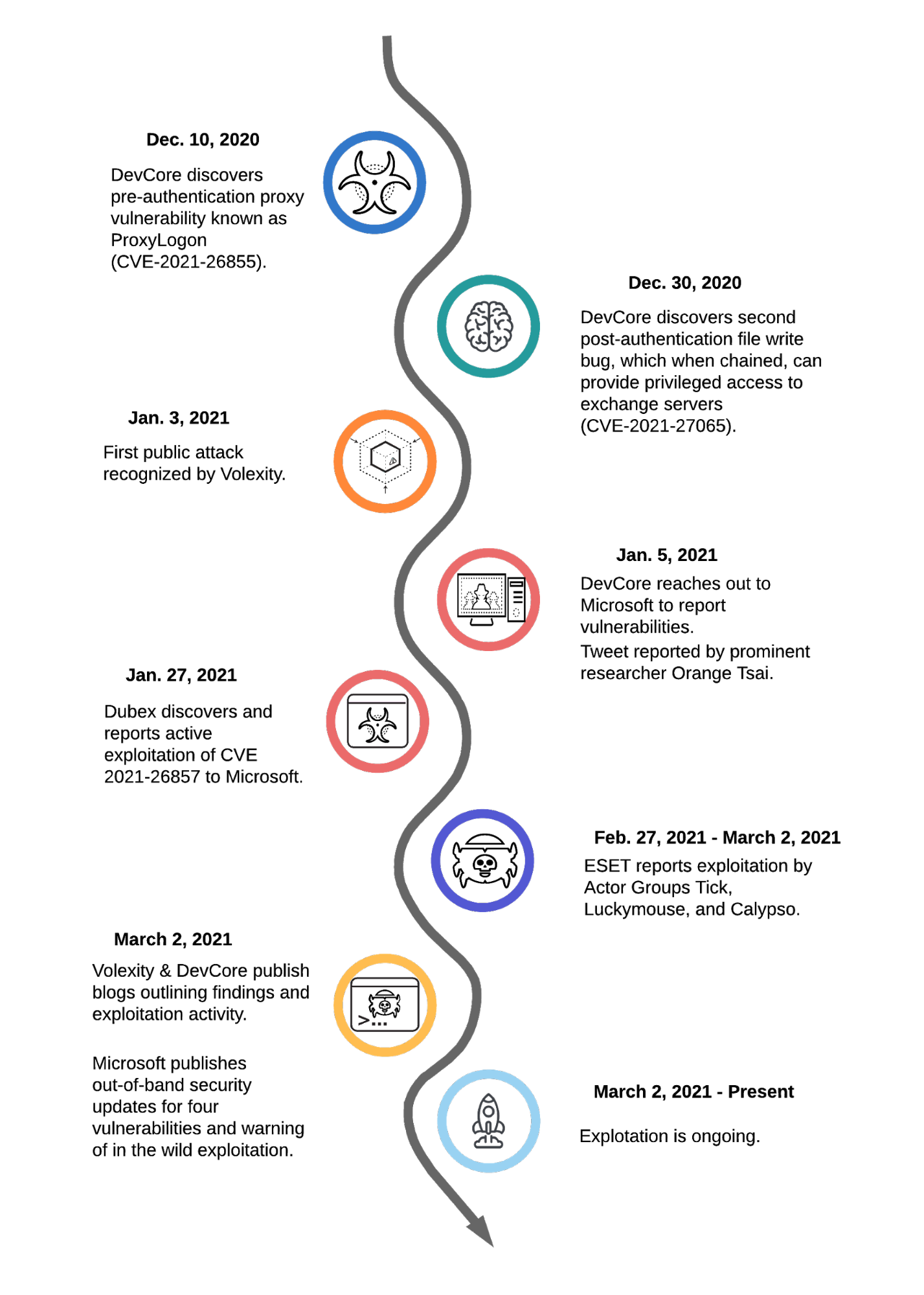
Microsoft Exchange Server Attack Timeline: Discoveries and Mitigations
Recomendado para você
-
Steam Community :: Screenshot :: Counter-Strike: Condition Zero11 junho 2024
-
 I played Counter Strike Condition Zero in 2023 #111 junho 2024
I played Counter Strike Condition Zero in 2023 #111 junho 2024 -
Microsoft Azure Marketplace11 junho 2024
-
 Back Cover image - Counter-Strike: Condition Zero - ModDB11 junho 2024
Back Cover image - Counter-Strike: Condition Zero - ModDB11 junho 2024 -
 CS:CZ Servers, CS:CZ Servers List - December 202311 junho 2024
CS:CZ Servers, CS:CZ Servers List - December 202311 junho 2024 -
 CS 1.6 to CZ:DS Graphical Overhaul mod for Counter-Strike - ModDB11 junho 2024
CS 1.6 to CZ:DS Graphical Overhaul mod for Counter-Strike - ModDB11 junho 2024 -
 1337 Board v7 file - Counter-Strike: Condition Zero - Mod DB11 junho 2024
1337 Board v7 file - Counter-Strike: Condition Zero - Mod DB11 junho 2024 -
 Counter-strike 1.6/condition zero Find servers button not11 junho 2024
Counter-strike 1.6/condition zero Find servers button not11 junho 2024 -
You Look Like My Next Girlfriend11 junho 2024
-
 Counter-Strike Xbox Background and Theme [Counter-Strike11 junho 2024
Counter-Strike Xbox Background and Theme [Counter-Strike11 junho 2024
você pode gostar
-
prompthunt: 2099 flcl fighter in streetwear, portriat, dynamic pose, with samurai hat, in japan ,smokey nagata, rx7 japanese sport car, cyberpunk style11 junho 2024
-
 Yarntown Makes Bloodborne A 16-Bit PC Game - GameSpot11 junho 2024
Yarntown Makes Bloodborne A 16-Bit PC Game - GameSpot11 junho 2024 -
 mobile android iOS apk download for free-TapTap11 junho 2024
mobile android iOS apk download for free-TapTap11 junho 2024 -
 Which Votann League to Choose in Warhammer 40K? Leagues of Votann Lore and Gamplay!11 junho 2024
Which Votann League to Choose in Warhammer 40K? Leagues of Votann Lore and Gamplay!11 junho 2024 -
 Ben 10: Alien Swarm - Nanomech by dlee1293847 on DeviantArt11 junho 2024
Ben 10: Alien Swarm - Nanomech by dlee1293847 on DeviantArt11 junho 2024 -
 One Piece Anime Heroes Roronoa Zoro Action Figure11 junho 2024
One Piece Anime Heroes Roronoa Zoro Action Figure11 junho 2024 -
 Banco de imagens : Papai Noel, personagem fictício, véspera de Natal, Grupo esportivo, Canídeos, evento, Banco de fotos, tradição, feriado, traje, Fawn, pele, árvore de Natal, Enfeite de natal 4000x6000 - ArielAngelPhotography11 junho 2024
Banco de imagens : Papai Noel, personagem fictício, véspera de Natal, Grupo esportivo, Canídeos, evento, Banco de fotos, tradição, feriado, traje, Fawn, pele, árvore de Natal, Enfeite de natal 4000x6000 - ArielAngelPhotography11 junho 2024 -
 Multiplayer para Minecraft PE - Servidores - Baixar APK para Android11 junho 2024
Multiplayer para Minecraft PE - Servidores - Baixar APK para Android11 junho 2024 -
 Android용 How To Draw Anime Step by Step For Beginners APK 다운로드11 junho 2024
Android용 How To Draw Anime Step by Step For Beginners APK 다운로드11 junho 2024 -
 ARAGUATINS: Morre aos 81 anos a comerciante Dona Júlia Aguiar11 junho 2024
ARAGUATINS: Morre aos 81 anos a comerciante Dona Júlia Aguiar11 junho 2024