Advanced Apple Debugging & Reverse Engineering, Chapter 31
Por um escritor misterioso
Last updated 30 maio 2024

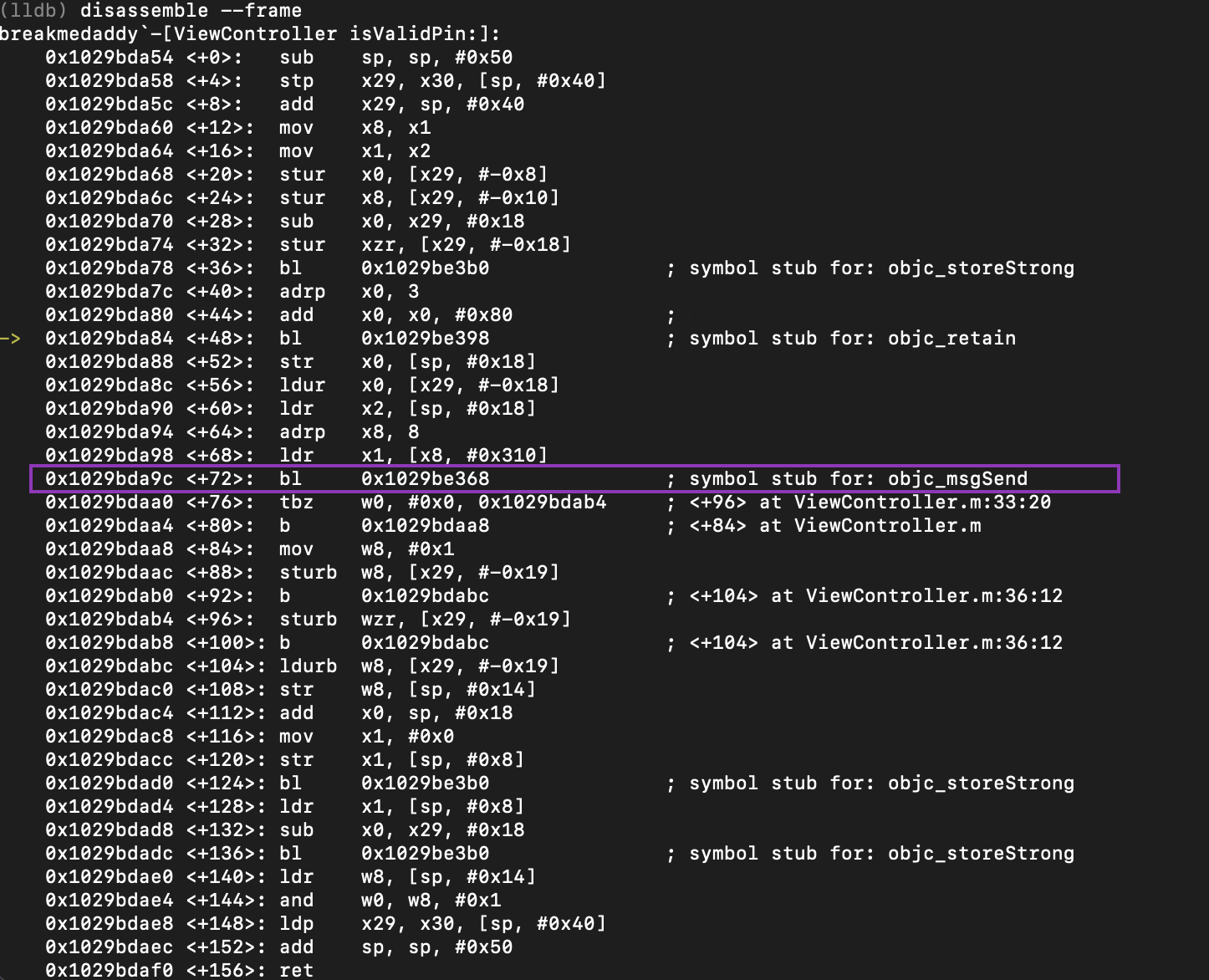
In this chapter, you'll use DTrace to hook objc_msgSend's entry probe and pull out the class name along with the Objective-C selector for that class. By the end of this chapter, you'll have LLDB generating a DTrace script which only generates tracing info for code implemented within the main executable that calls objc_msgSend.
How to Reverse Engineer and Patch an iOS Application for Beginners: Part I
Reverse Engineering: Binary Security, by Totally_Not_A_Haxxer
Reverse Engineering: Binary Security, by Totally_Not_A_Haxxer

Mobile AppSec Appdome Mobile Security Suite - Safe Android & iOS app
Reverse Engineering x64 for Beginners - Windows - Checkmate

Hacking the Xbox
Used Book in Good Condition Highlight, take notes, and search in the book

Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation

LLDB's Runtime Manipulation: A Guide to Advance Debugging and Optimization
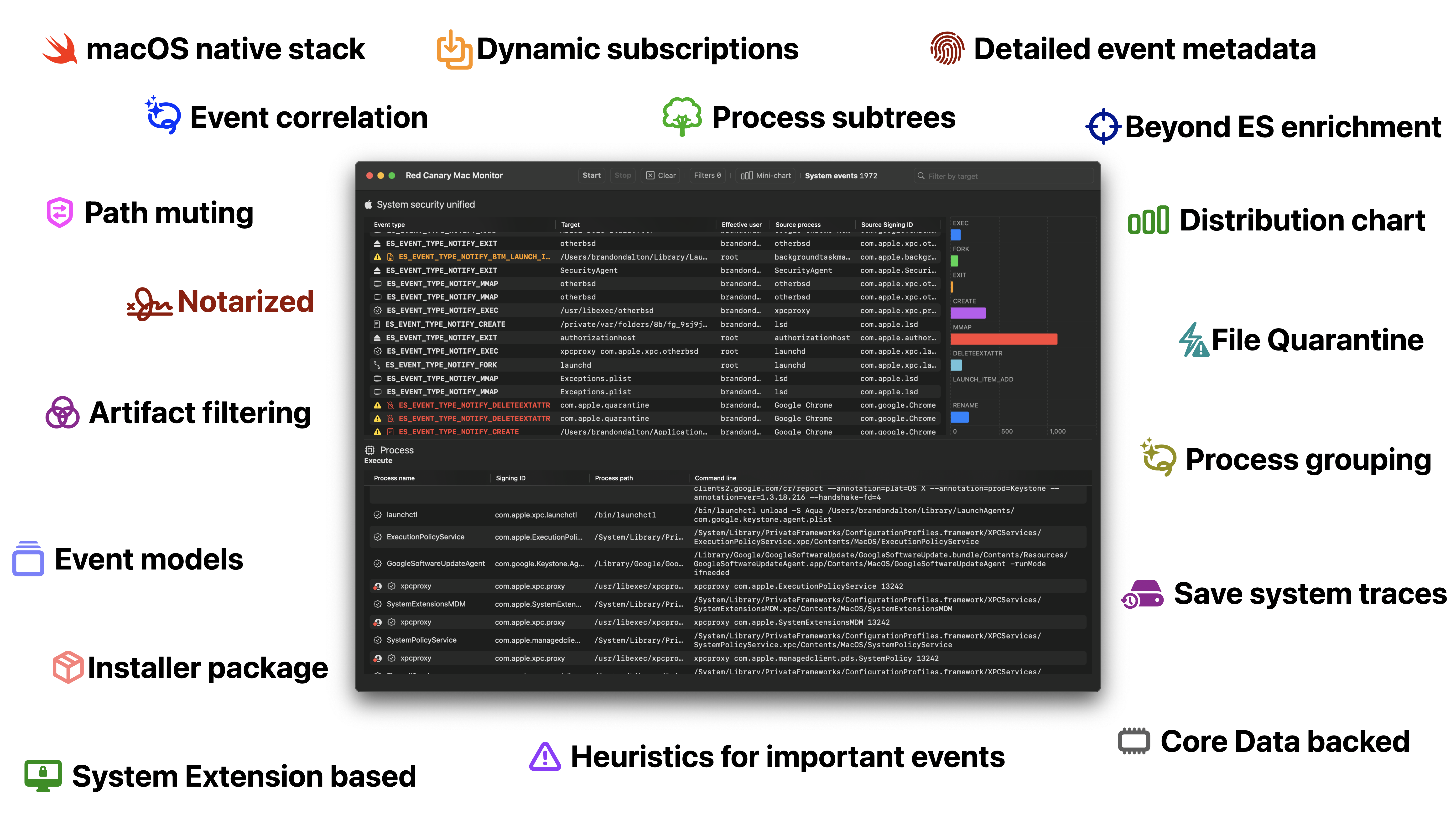
Red Canary Mac Monitor - An Advanced, Stand-Alone System Monitoring Tool Tailor-Made For macOS Security Research
iOS Reverse Engineering - Debugging and Tracing with LLDB
Recomendado para você
-
como canjear en rbx gum|Búsqueda de TikTok30 maio 2024
-
 New rbx.gum promocode june 6,202230 maio 2024
New rbx.gum promocode june 6,202230 maio 2024 -
como ver los codigos de rbx gum en discord|Búsqueda de TikTok30 maio 2024
-
 crisairys gacha gachafer (cgachafer) - Profile30 maio 2024
crisairys gacha gachafer (cgachafer) - Profile30 maio 2024 -
roblox-api · GitHub Topics · GitHub30 maio 2024
-
Discuss Everything About Bubble Gum Simulator Wiki30 maio 2024
-
 Discuss Everything About Bubble Gum Simulator Wiki30 maio 2024
Discuss Everything About Bubble Gum Simulator Wiki30 maio 2024 -
Discuss Everything About Bubble Gum Simulator Wiki30 maio 2024
-
coinEZ/cryptocurrencies.json at main · Purukitto/coinEZ · GitHub30 maio 2024
-
Fer99930 maio 2024
você pode gostar
-
 kukie on X: imagine if FIRST STAGE starters get soul burst #LoomianLegacy #loomianlegacyart #robloxart / X30 maio 2024
kukie on X: imagine if FIRST STAGE starters get soul burst #LoomianLegacy #loomianlegacyart #robloxart / X30 maio 2024 -
 STANDING THERE MENACINGLY by Rian Sound Effect - Meme Button - Tuna30 maio 2024
STANDING THERE MENACINGLY by Rian Sound Effect - Meme Button - Tuna30 maio 2024 -
 Cartoon Network é líder de audiência entre crianças no primeiro semestre de 202030 maio 2024
Cartoon Network é líder de audiência entre crianças no primeiro semestre de 202030 maio 2024 -
 Zeldapedia, The Legend Of Zelda Wiki - Zelda Four Swords Zelda30 maio 2024
Zeldapedia, The Legend Of Zelda Wiki - Zelda Four Swords Zelda30 maio 2024 -
 Download Gogeta Download HD HQ PNG Image30 maio 2024
Download Gogeta Download HD HQ PNG Image30 maio 2024 -
 Xadrez básico como a campeã dos Estados Unidos volume 2 :: Jogue como Elena Donaldson-Akhmilovskaya (Portuguese Edition)30 maio 2024
Xadrez básico como a campeã dos Estados Unidos volume 2 :: Jogue como Elena Donaldson-Akhmilovskaya (Portuguese Edition)30 maio 2024 -
 LGBT+ canon do dia on X: O personagem LGBT canon bônus do dia é30 maio 2024
LGBT+ canon do dia on X: O personagem LGBT canon bônus do dia é30 maio 2024 -
 Frontiers Gamification into the design of the e-3D online course30 maio 2024
Frontiers Gamification into the design of the e-3D online course30 maio 2024 -
 Doa Minum Air Zam-zam, Dibaca Agar Mendapat Berkah30 maio 2024
Doa Minum Air Zam-zam, Dibaca Agar Mendapat Berkah30 maio 2024 -
 EsPCEx 2010 - Matemática - Questão 0930 maio 2024
EsPCEx 2010 - Matemática - Questão 0930 maio 2024