Complete UAF exploit - UD Capture
Por um escritor misterioso
Last updated 29 maio 2024

Chrome 0-day exploit CVE-2019-13720 used in Operation WizardOpium
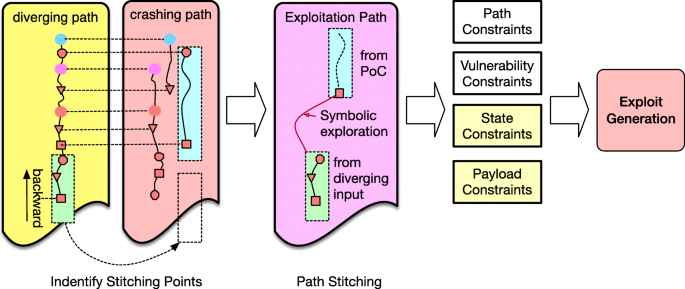
From proof-of-concept to exploitable, Cybersecurity
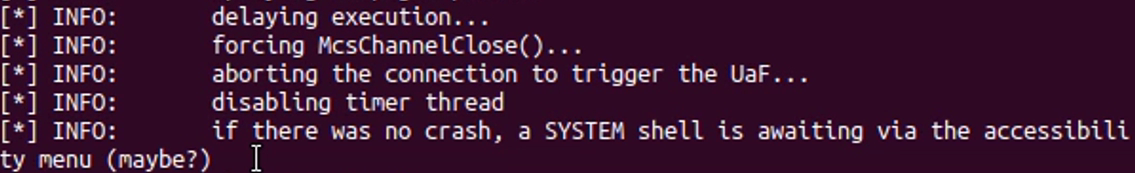
BlueKeep PoC demonstrates risk of Remote Desktop exploit – Sophos News
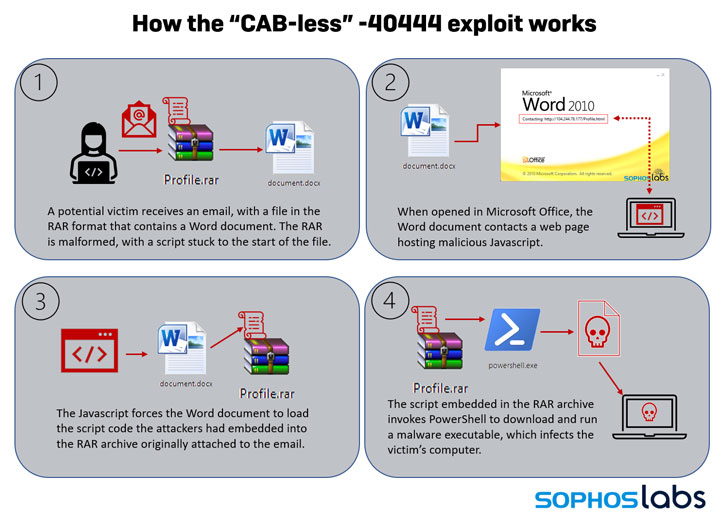
New Exploit Lets Malware Attackers Bypass Patch for Critical
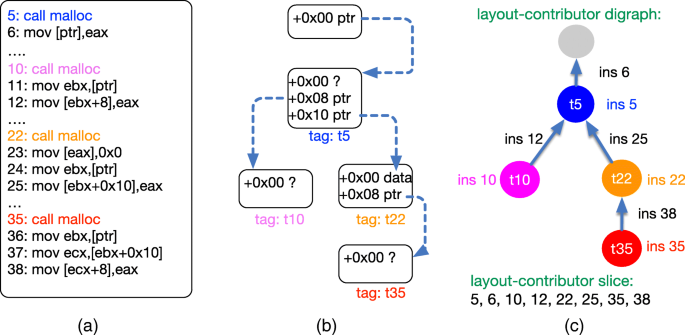
From proof-of-concept to exploitable, Cybersecurity
A Survey of Detection Methods for Software Use-After-Free
Heap tricks never get old - Insomni'hack teaser 2022
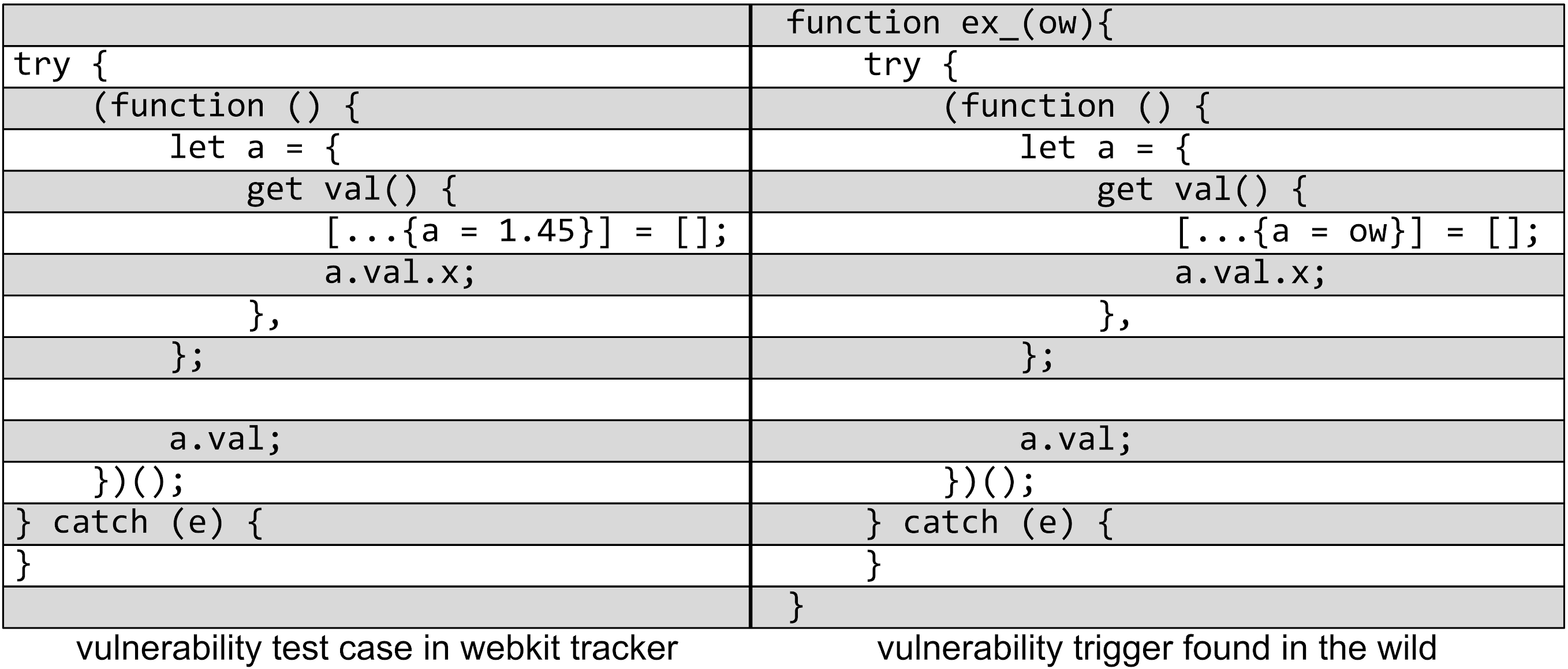
Project Zero: JSC Exploits
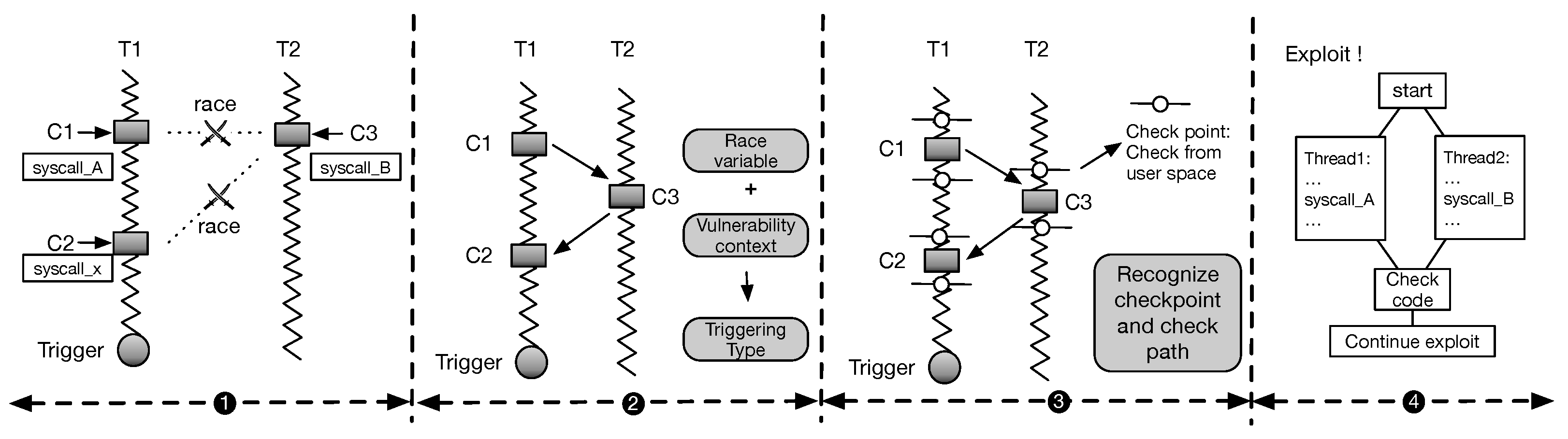
Applied Sciences, Free Full-Text
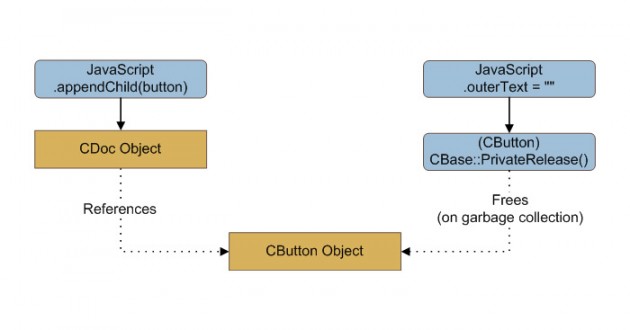
Use-after-frees: That pointer may be pointing to something bad

Reverse Engineering Coin Hunt World's Binary Protocol
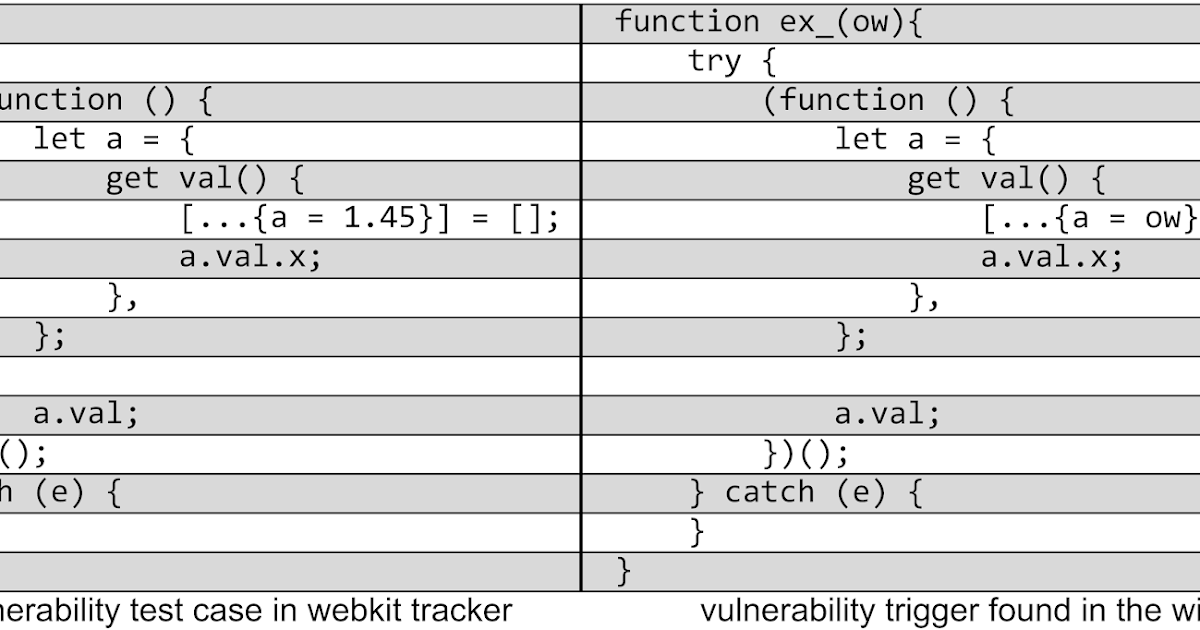
Project Zero: JSC Exploits

PDF) Authenticator Rebinding Attack of the UAF Protocol on Mobile
The big heap adventure. Mastering heap exploitation techniques on

Estimating the Bit Security of Pairing-Friendly Curves
Recomendado para você
-
 KING LEGACY Script Pastebin 2022 UPDATE 3.5 AUTO FARM29 maio 2024
KING LEGACY Script Pastebin 2022 UPDATE 3.5 AUTO FARM29 maio 2024 -
![King Legacy [AUTOFARM/ESP/TP] Scripts](https://rbxscript.com/images/_2AQ1pnn32u-image.png) King Legacy [AUTOFARM/ESP/TP] Scripts29 maio 2024
King Legacy [AUTOFARM/ESP/TP] Scripts29 maio 2024 -
![UPDATE 4.7.1💧] KING LEGACY Script - Auto Farm Lv, Auto Sea King](https://i.ytimg.com/vi/e6Ah0bMX-QA/sddefault.jpg) UPDATE 4.7.1💧] KING LEGACY Script - Auto Farm Lv, Auto Sea King29 maio 2024
UPDATE 4.7.1💧] KING LEGACY Script - Auto Farm Lv, Auto Sea King29 maio 2024 -
 Full DC Comics Solicitations For February 2022 - Not Just Batman29 maio 2024
Full DC Comics Solicitations For February 2022 - Not Just Batman29 maio 2024 -
 SCRIPT KING LEGACY !!! AUTO FARM ,AUTO RAID!!MOBILE FLUXUS E HYDROGEN!!29 maio 2024
SCRIPT KING LEGACY !!! AUTO FARM ,AUTO RAID!!MOBILE FLUXUS E HYDROGEN!!29 maio 2024 -
 KING LEGACY – ScriptPastebin29 maio 2024
KING LEGACY – ScriptPastebin29 maio 2024 -
 News and Media29 maio 2024
News and Media29 maio 2024 -
 The Hardy Boys by Edward Stratemeyer: A Children's Book Series Overvie – TheBookBundler29 maio 2024
The Hardy Boys by Edward Stratemeyer: A Children's Book Series Overvie – TheBookBundler29 maio 2024 -
 Calaméo - ESRAmagazine Issue 213 July 202229 maio 2024
Calaméo - ESRAmagazine Issue 213 July 202229 maio 2024 -
![King Legacy Script [AUTO FARM - AUTO SEA BEAST - AUTO ALL - OP SCRIPT] *pastebin*](https://i.ytimg.com/vi/mmIk0qC4fug/hq720.jpg?sqp=-oaymwEhCK4FEIIDSFryq4qpAxMIARUAAAAAGAElAADIQj0AgKJD&rs=AOn4CLDHgwD-dtlgAhTX5WotBPezKMDTTw) King Legacy Script [AUTO FARM - AUTO SEA BEAST - AUTO ALL - OP SCRIPT] *pastebin*29 maio 2024
King Legacy Script [AUTO FARM - AUTO SEA BEAST - AUTO ALL - OP SCRIPT] *pastebin*29 maio 2024
você pode gostar
-
 Oakley Vault, 800 Highway 400 S Dawsonville, GA Men's and Women's Sunglasses, Goggles, & Apparel29 maio 2024
Oakley Vault, 800 Highway 400 S Dawsonville, GA Men's and Women's Sunglasses, Goggles, & Apparel29 maio 2024 -
/hotmart/checkout_custom/1069f9a7-b87f-4a6e-a1cb-7577050499b4/ia6fme3f.jpg) Apostila Fábrica de Bolos Caseiros29 maio 2024
Apostila Fábrica de Bolos Caseiros29 maio 2024 -
 Wesker vs Krauser by WolfShadow14081990 on DeviantArt29 maio 2024
Wesker vs Krauser by WolfShadow14081990 on DeviantArt29 maio 2024 -
 Gaming Organization 100 Thieves Signs Stars 2Hype – The Hollywood Reporter29 maio 2024
Gaming Organization 100 Thieves Signs Stars 2Hype – The Hollywood Reporter29 maio 2024 -
 Naruto anime dos desenhos animados chaveiro naruto sasuke sakura ningji kakashi saco personalidade pingente novo casal ornamento periférico presente29 maio 2024
Naruto anime dos desenhos animados chaveiro naruto sasuke sakura ningji kakashi saco personalidade pingente novo casal ornamento periférico presente29 maio 2024 -
 Mini Game Sup com Controle para 2 Jogadores 400 Jogos Cores29 maio 2024
Mini Game Sup com Controle para 2 Jogadores 400 Jogos Cores29 maio 2024 -
 The Witcher Gets Novel, Heads to PS329 maio 2024
The Witcher Gets Novel, Heads to PS329 maio 2024 -
 My Senpai is Annoying, Animanga Wiki29 maio 2024
My Senpai is Annoying, Animanga Wiki29 maio 2024 -
 Adventure time wiki, Adventure time, School adventure29 maio 2024
Adventure time wiki, Adventure time, School adventure29 maio 2024 -
 ONE PIECE - Doragon Doragon no Mi: Moderu Getsuryu by Yami-no-Takemaru on DeviantArt29 maio 2024
ONE PIECE - Doragon Doragon no Mi: Moderu Getsuryu by Yami-no-Takemaru on DeviantArt29 maio 2024