Hack Like a Pro: Abusing DNS for Reconnaissance « Null Byte :: WonderHowTo
Por um escritor misterioso
Last updated 20 junho 2024
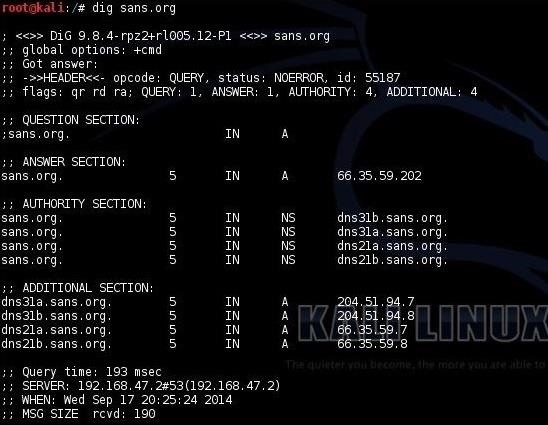
Hack Like a Pro: Linux Basics for the Aspiring Hacker, Part 17

Study of Directory Traversal Attack and Tools Used for Attack by

Hack Like a Pro: Abusing DNS for Reconnaissance « Null Byte

Recon « Null Byte :: WonderHowTo

D-Link, IoT Devices Under Attack By Tor-Based Gafgyt Variant

ELearnSecurity EWPT Notes, PDF, Http Cookie
HACKER SUMMER CAMP 2023 GUIDES — Part One: Surviving Las Vegas

DNS hacking (beginner to advanced)
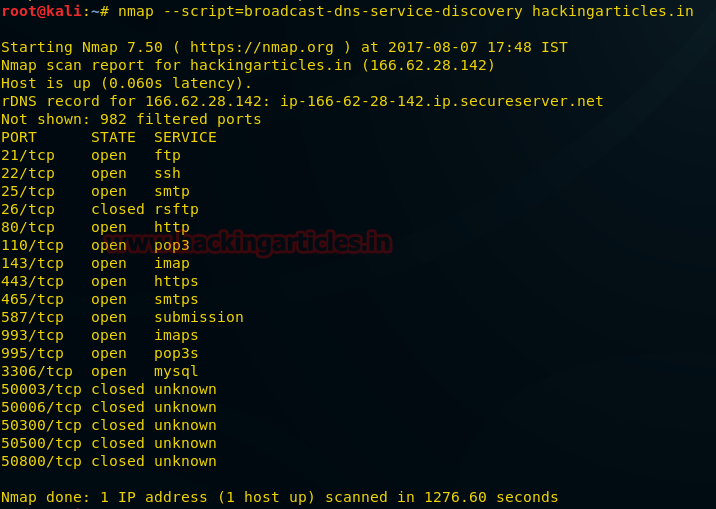
4 Ways to DNS Enumeration - Hacking Articles
Recomendado para você
-
-min.png?locale=en) DigDig.IO X-Ray20 junho 2024
DigDig.IO X-Ray20 junho 2024 -
 Digdig.io Crazy Gameplay - JEHRO The Best of The game.!20 junho 2024
Digdig.io Crazy Gameplay - JEHRO The Best of The game.!20 junho 2024 -
 Hack~ Don't Dig Down (SNES) · RetroAchievements20 junho 2024
Hack~ Don't Dig Down (SNES) · RetroAchievements20 junho 2024 -
 Power Dig APK Download for Android Free20 junho 2024
Power Dig APK Download for Android Free20 junho 2024 -
 Cybersecurity method learns from hackers by tricking them20 junho 2024
Cybersecurity method learns from hackers by tricking them20 junho 2024 -
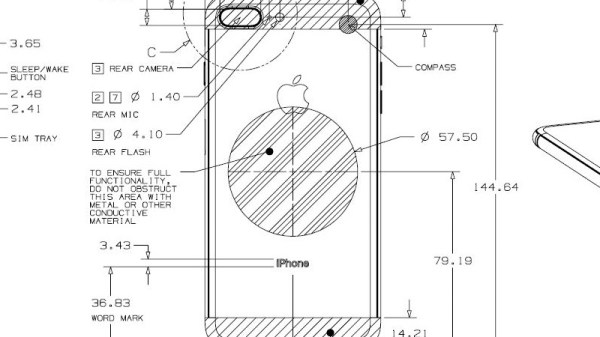 Qi Hack Hackaday20 junho 2024
Qi Hack Hackaday20 junho 2024 -
 Season Passes20 junho 2024
Season Passes20 junho 2024 -
 Top 55 Similar websites like m28.studio and alternatives20 junho 2024
Top 55 Similar websites like m28.studio and alternatives20 junho 2024 -
 Three Marketing Hacks For Indie Game Developers – DiG-iT! Games20 junho 2024
Three Marketing Hacks For Indie Game Developers – DiG-iT! Games20 junho 2024 -
Dig It.20 junho 2024
você pode gostar
-
 Jogos Xbox 360 ( novos Mídia Fisica) - Videogames - Cidade20 junho 2024
Jogos Xbox 360 ( novos Mídia Fisica) - Videogames - Cidade20 junho 2024 -
 Netflix: conheça André Lamoglia, brasileiro na 5ª temporada de Elite20 junho 2024
Netflix: conheça André Lamoglia, brasileiro na 5ª temporada de Elite20 junho 2024 -
neon genesis evangelion script|TikTok Search20 junho 2024
-
 Bhagwad Gita Blog : Life is a Chess Game20 junho 2024
Bhagwad Gita Blog : Life is a Chess Game20 junho 2024 -
WillD - FANART Somali - Somali to mori no kamisama ❤️❤️❤️20 junho 2024
-
 Jaqueta Casaco Sharingan Kakashi Hatake Nuvem Akatsuki: Naruto Preto Anime Mangá - MKP - Toyshow Tudo de Marvel DC Netflix Geek Funko Pop Colecionáveis20 junho 2024
Jaqueta Casaco Sharingan Kakashi Hatake Nuvem Akatsuki: Naruto Preto Anime Mangá - MKP - Toyshow Tudo de Marvel DC Netflix Geek Funko Pop Colecionáveis20 junho 2024 -
 Fãs brasileiros criam game de Pokémon20 junho 2024
Fãs brasileiros criam game de Pokémon20 junho 2024 -
 Yennefer of Vengerberg figurine - Inspire Uplift20 junho 2024
Yennefer of Vengerberg figurine - Inspire Uplift20 junho 2024 -
 Fruits Basket 2019 Characters Anime Sticker Set GE-5583820 junho 2024
Fruits Basket 2019 Characters Anime Sticker Set GE-5583820 junho 2024 -
 Portugal joga em Leiria na Liga das Nações feminina20 junho 2024
Portugal joga em Leiria na Liga das Nações feminina20 junho 2024


