Indirect Command Execution – Penetration Testing Lab
Por um escritor misterioso
Last updated 05 junho 2024

The windows ecosystem provides multiple binaries that could be used by adversaries to execute arbitrary commands that will evade detection especially in environments that are monitoring binaries such as "cmd.exe". In certain occasions the techniques described below could be used to bypass application whitelisting products if rules are not configured properly (whitelist by path or…

How to Prevent SQL Injection Attacks?
Electronics, Free Full-Text

TryHackMe Hacktivities
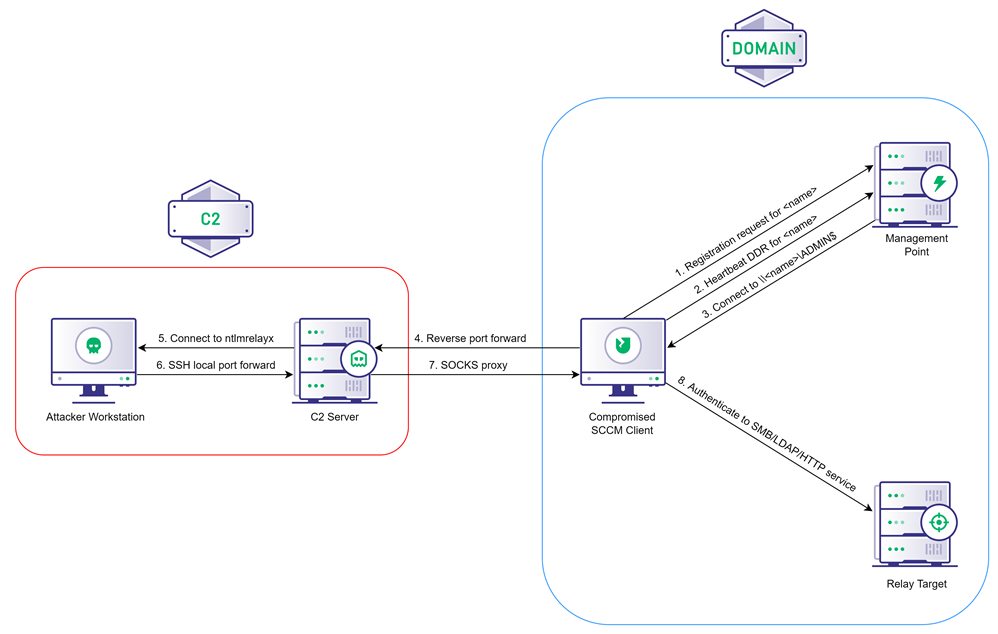
Coercing NTLM Authentication from SCCM, by Chris Thompson

OWASP LLM02: Insecure Output Handling
What is Application Security Architecture?

Indirect Command Execution

How Much Does Red Team Penetration Testing Cost In 2023?
Kali Linux Penetration Testing Tutorial: How to Use Kali Linux

File Inclusion Vulnerabilities: What are they and how do they work?

Indirect Command Execution – Penetration Testing Lab

Sensors, Free Full-Text

Global and regional governance of One Health and implications for global health security - The Lancet
Indirect Command Execution: Defense Evasion (T1202) - Hacking Articles
Recomendado para você
-
 Run Linux commands from cmd.exe prompt in Windows 1005 junho 2024
Run Linux commands from cmd.exe prompt in Windows 1005 junho 2024 -
 How to Run an EXE File at the Command Prompt in 8 Easy Steps05 junho 2024
How to Run an EXE File at the Command Prompt in 8 Easy Steps05 junho 2024 -
 Use the System File Checker tool to repair missing or corrupted05 junho 2024
Use the System File Checker tool to repair missing or corrupted05 junho 2024 -
 Free Remote Command Prompt Tool, Execute Commands Remotely, Remote Command Execution05 junho 2024
Free Remote Command Prompt Tool, Execute Commands Remotely, Remote Command Execution05 junho 2024 -
 windows 7 - CMD open new winodw when run php command - Super User05 junho 2024
windows 7 - CMD open new winodw when run php command - Super User05 junho 2024 -
 Executing Command Prompt commands in SSIS05 junho 2024
Executing Command Prompt commands in SSIS05 junho 2024 -
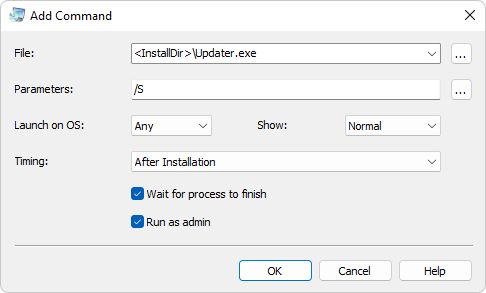 Execute Commands and Launch Tasks - Actual Installer Help05 junho 2024
Execute Commands and Launch Tasks - Actual Installer Help05 junho 2024 -
 Use PowerShell to execute an exe – 4sysops05 junho 2024
Use PowerShell to execute an exe – 4sysops05 junho 2024 -
 Command line switches for Outlook 365, 2021, 2019, 2016, 2013, and previous - HowTo-Outlook05 junho 2024
Command line switches for Outlook 365, 2021, 2019, 2016, 2013, and previous - HowTo-Outlook05 junho 2024 -
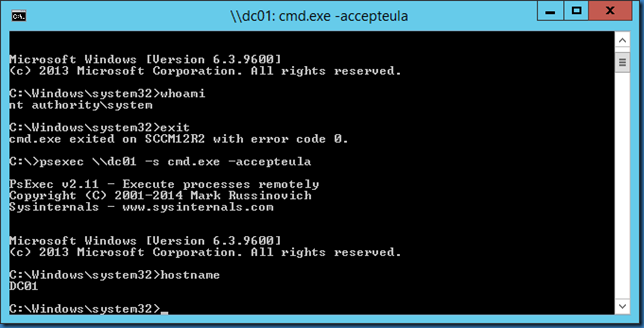 Run command in system context - Mindcore Techblog05 junho 2024
Run command in system context - Mindcore Techblog05 junho 2024
você pode gostar
-
 Marvel Legends Spider-Man: No Way Home Wave 2 Revealed/ Deluxe Green Goblin & Doctor Octopus05 junho 2024
Marvel Legends Spider-Man: No Way Home Wave 2 Revealed/ Deluxe Green Goblin & Doctor Octopus05 junho 2024 -
 Anybody wanna give a small godly like heart blade cookie blade05 junho 2024
Anybody wanna give a small godly like heart blade cookie blade05 junho 2024 -
 CWGST is currently doing a AMA on Instagram, here are important05 junho 2024
CWGST is currently doing a AMA on Instagram, here are important05 junho 2024 -
 Madamka🌿 • sapphic art on X: Hey, are you in need of a wlw #webtoon about witches, magic, fashion and furious flirting?🔮 My GL comic, Diamond Dive, is right here for ya05 junho 2024
Madamka🌿 • sapphic art on X: Hey, are you in need of a wlw #webtoon about witches, magic, fashion and furious flirting?🔮 My GL comic, Diamond Dive, is right here for ya05 junho 2024 -
 Free aesthetic Roblox t-shirts (screenshot ,crop and upload)Girls edition Part-2 @Mangoclush05 junho 2024
Free aesthetic Roblox t-shirts (screenshot ,crop and upload)Girls edition Part-2 @Mangoclush05 junho 2024 -
![Explained] Google Play Games Beta for PC: What is it, How to Download Android Games on PC - MySmartPrice](https://assets.mspimages.in/gear/wp-content/uploads/2023/07/Screenshot_2023-07-14-17-07-49-39_76eaced432273cd65da1ec13409568ff-674x1024.jpg) Explained] Google Play Games Beta for PC: What is it, How to Download Android Games on PC - MySmartPrice05 junho 2024
Explained] Google Play Games Beta for PC: What is it, How to Download Android Games on PC - MySmartPrice05 junho 2024 -
 22 ideias de Personagens carecas05 junho 2024
22 ideias de Personagens carecas05 junho 2024 -
 Among us toung kill contest 0 pixel art05 junho 2024
Among us toung kill contest 0 pixel art05 junho 2024 -
 Hitori no Shita: The Outcast Episódio 2 - Animes Online05 junho 2024
Hitori no Shita: The Outcast Episódio 2 - Animes Online05 junho 2024 -
 Tchia - Review de jogos05 junho 2024
Tchia - Review de jogos05 junho 2024