Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 08 julho 2024
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Iranian hacker claims he acted alone in stealing digital SSL certificates, Hacking

Ethical Hacking Learning Path — A Complete Roadmap, by crawsecurity

Hackers breached Greece's top-level domain registrar

Zvukový „vodoznak“ – konec pirátství?

Ethical Hacking - Project C - QuickStart Cybersecurity Bootcamp

Tips for Investigating Cybercrime Infrastructure

Best platforms to learn ethical hacking! - Intigriti

tl;dr sec] #169 - Top 10 Web Hacking Techniques of 2022, Finding Malicious Dependencies, Fearless CORS
Is Foundational Knowledge (Networking, Coding, Linux) Really That Important When Learning to Hack?
Hack This Site: Realistic Web Mission — Level 13
Ronin Hack: North Korea's Lazarus Behind $540 Million Axe Infinity Breach

Hacking Tutorial - Ethical Hacking Tutorial - Wikitechy

Hackbun

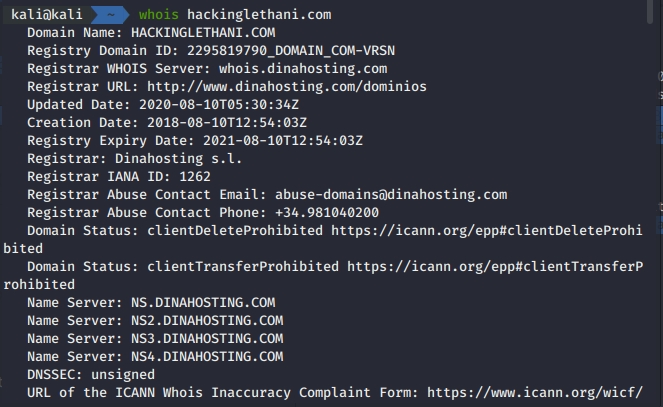
Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)

N. Korean Hackers Distribute Trojanized CyberLink Software in Supply Chain Attack
Recomendado para você
-
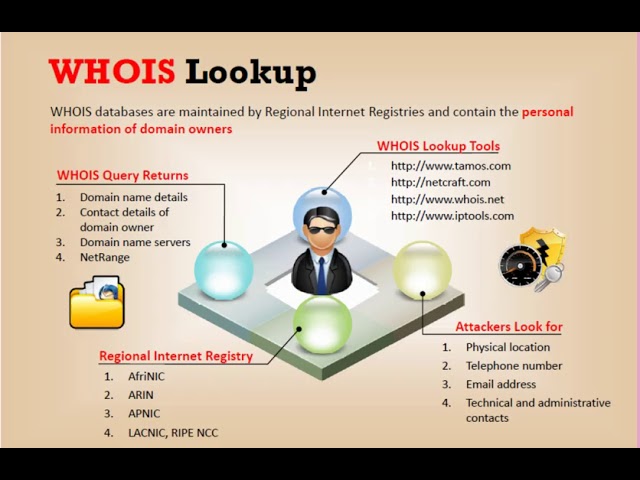 What is the WHOIS lookup08 julho 2024
What is the WHOIS lookup08 julho 2024 -
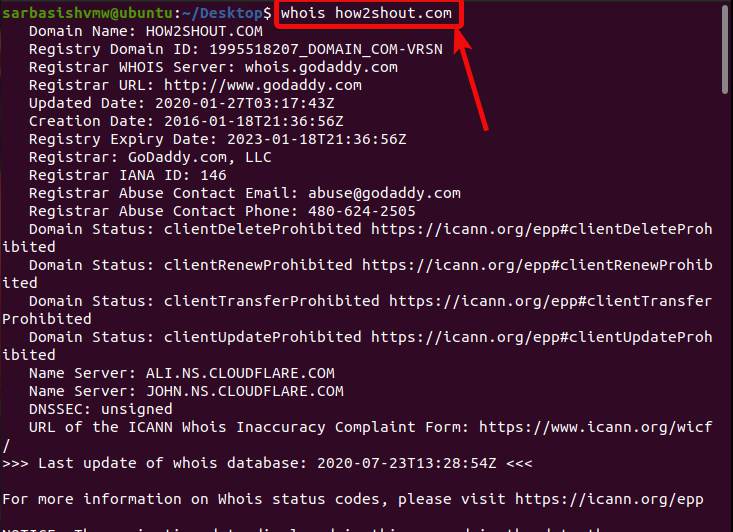 How to use the Whois command on Linux to see domain information on08 julho 2024
How to use the Whois command on Linux to see domain information on08 julho 2024 -
 What Is Whois Lookup And How Can It Help You? - Monsterhost08 julho 2024
What Is Whois Lookup And How Can It Help You? - Monsterhost08 julho 2024 -
 WHOIS Looking at Your Information? Try a Private Domain Registration08 julho 2024
WHOIS Looking at Your Information? Try a Private Domain Registration08 julho 2024 -
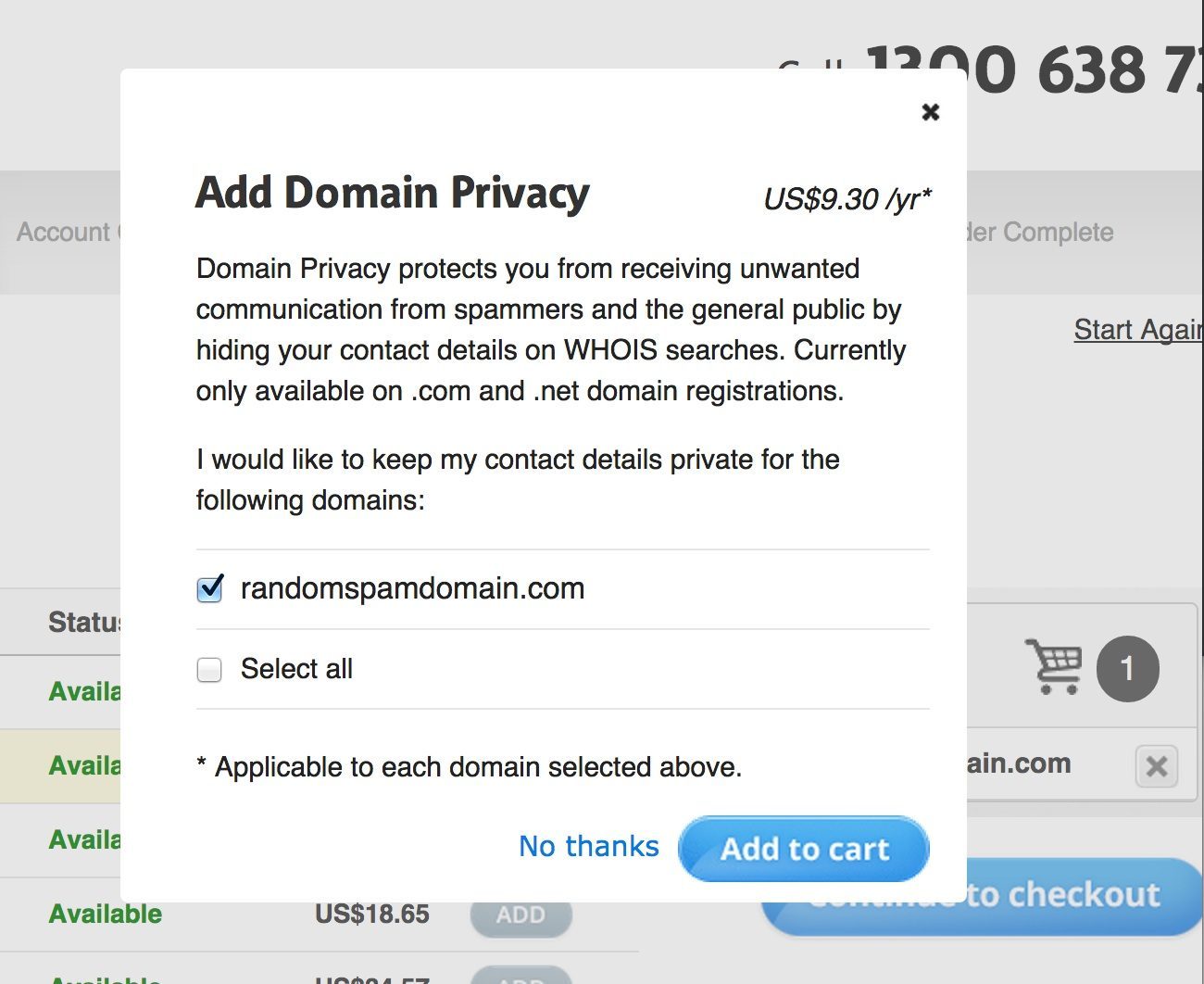 WHOIS Email, Email Address WHOIS08 julho 2024
WHOIS Email, Email Address WHOIS08 julho 2024 -
 WHOIS: Retrieve information on a domain name08 julho 2024
WHOIS: Retrieve information on a domain name08 julho 2024 -
 What is: WHOIS Lookup08 julho 2024
What is: WHOIS Lookup08 julho 2024 -
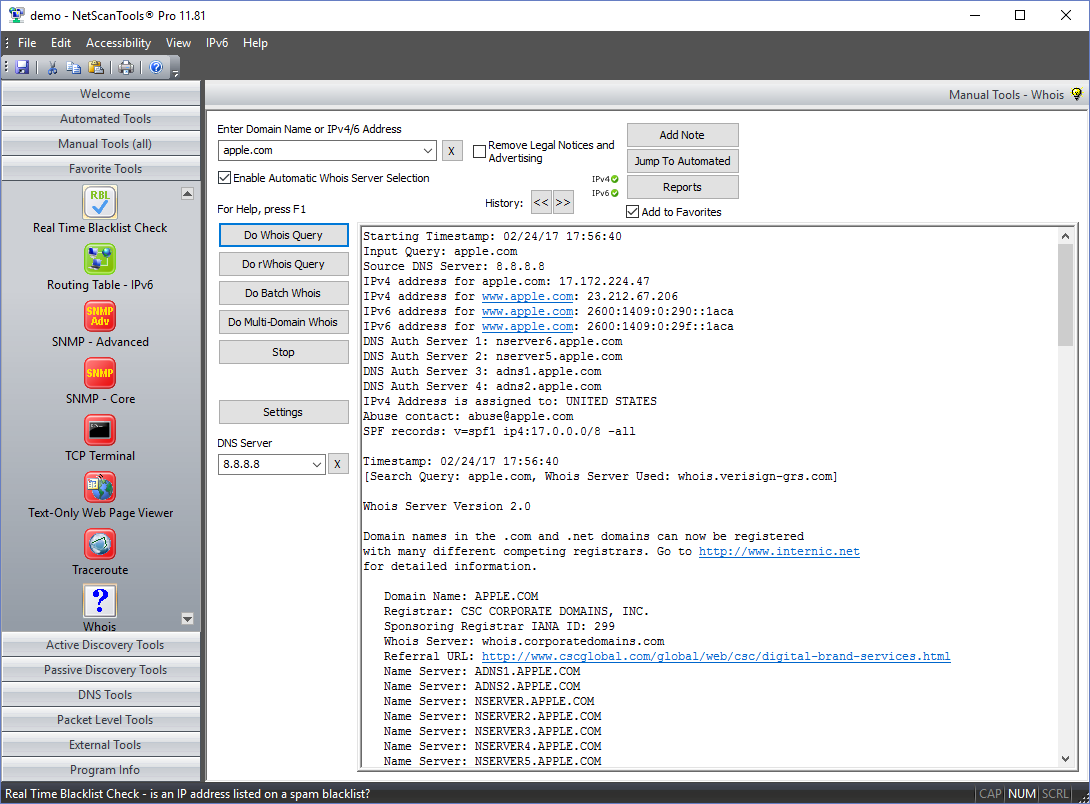 Whois Tool in NetScanTools Pro08 julho 2024
Whois Tool in NetScanTools Pro08 julho 2024 -
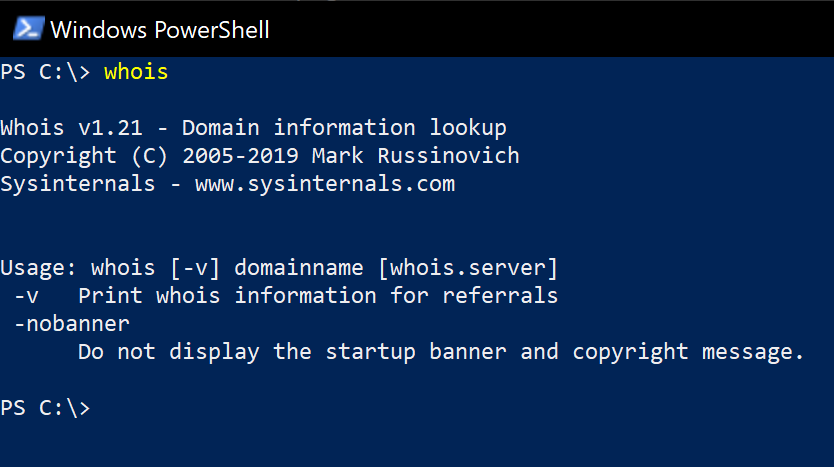 Chocolatey Software Whois - Windows Sysinternals 1.2108 julho 2024
Chocolatey Software Whois - Windows Sysinternals 1.2108 julho 2024 -
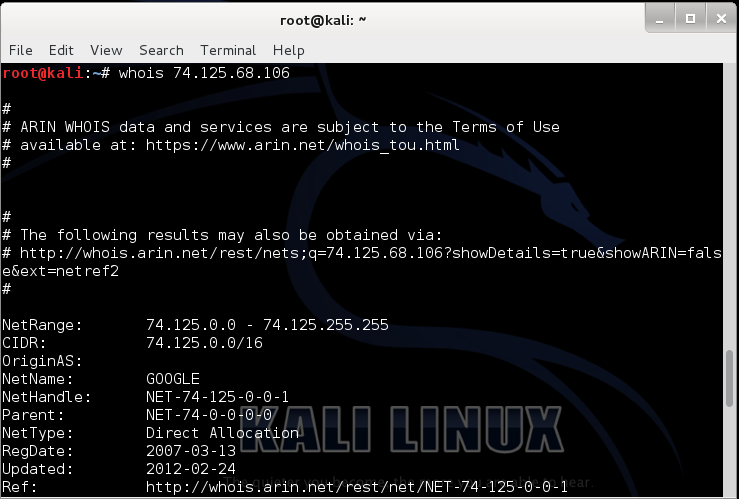 Understanding the Power of Whois Command in Kali Linux08 julho 2024
Understanding the Power of Whois Command in Kali Linux08 julho 2024
você pode gostar
-
 Xenoko on X: Your Racing Simulator. I imagined a logo and a cover art for Assetto Corsa 2, which sould release next year! Xbox and PlayStation versions in replies ⬇️ #AssettoCorsa #VGPUnite08 julho 2024
Xenoko on X: Your Racing Simulator. I imagined a logo and a cover art for Assetto Corsa 2, which sould release next year! Xbox and PlayStation versions in replies ⬇️ #AssettoCorsa #VGPUnite08 julho 2024 -
 Guia Completo: Como Instalar a Tradução PT-BR em Warhammer 40K Rogue Trader por Mutar!08 julho 2024
Guia Completo: Como Instalar a Tradução PT-BR em Warhammer 40K Rogue Trader por Mutar!08 julho 2024 -
 Clicker Heroes Available Everywhere!08 julho 2024
Clicker Heroes Available Everywhere!08 julho 2024 -
 asdasd by BedandBreakfast (B&B)! // Unstop (formerly Dare2Compete)08 julho 2024
asdasd by BedandBreakfast (B&B)! // Unstop (formerly Dare2Compete)08 julho 2024 -
format(webp)) Results for Tag - Crunchyroll News08 julho 2024
Results for Tag - Crunchyroll News08 julho 2024 -
 Top 3 games NFT para jogar com pouco dinheiro – Bitnoob08 julho 2024
Top 3 games NFT para jogar com pouco dinheiro – Bitnoob08 julho 2024 -
 Uno: Rules and a Brief History of the Quick-Thinking Classic08 julho 2024
Uno: Rules and a Brief History of the Quick-Thinking Classic08 julho 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/C/o/iy4e4KTgWdjKlZzb5sxA/2014-12-06-uncharted-4-imagem-divulgacao.jpg) Uncharted 4: A Thief's End mostra gráficos incríveis em novo vídeo08 julho 2024
Uncharted 4: A Thief's End mostra gráficos incríveis em novo vídeo08 julho 2024 -
 Novidades Associados - ABRAGAMES - ASSOCIAÇÃO BRASILEIRA DAS EMPRESAS DESENVOLVEDORAS DE JOGOS DIGITAIS08 julho 2024
Novidades Associados - ABRAGAMES - ASSOCIAÇÃO BRASILEIRA DAS EMPRESAS DESENVOLVEDORAS DE JOGOS DIGITAIS08 julho 2024 -
Mondaiji Tachi ga Isekai kara kuru Sou Desu Yo? Light Novel08 julho 2024
