How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 29 maio 2024
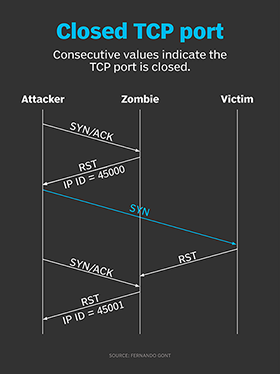
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.

What Is an Idle Scan? (with pictures)

NMAP by Shrikant Antre & Shobhit Gautam
SPLOIT: How to Make a Python Port Scanner « Null Byte :: WonderHowTo

PDF) TCP Idle Scanning using network printers

Port Scan Attack】Definition, Examples, and Prevention

Hacking techniques
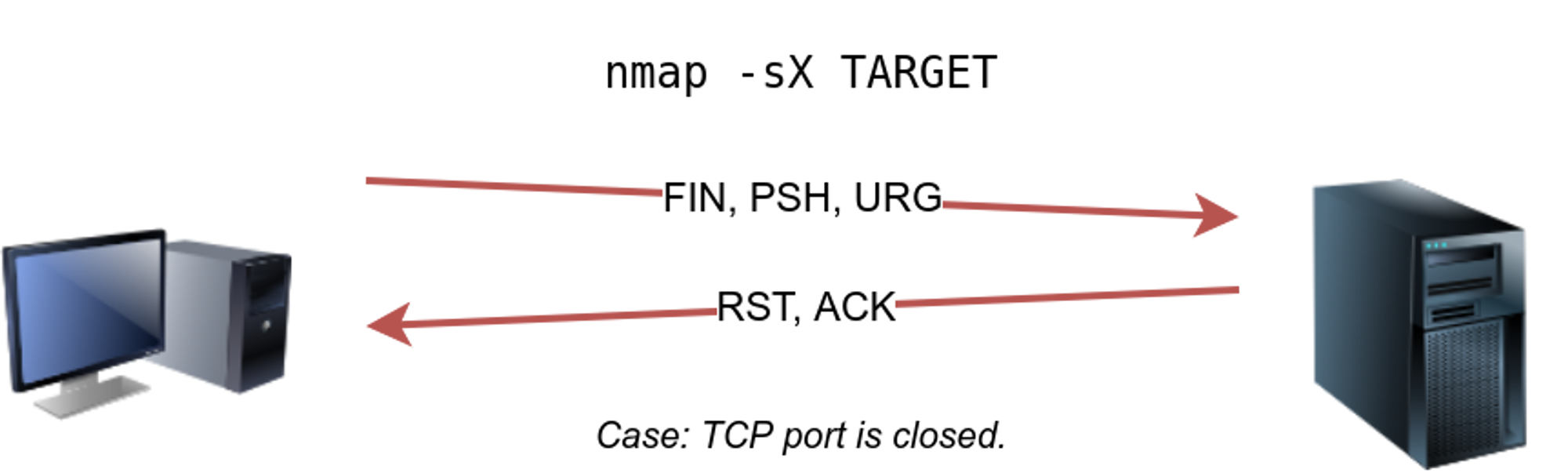
The Ultimate Guide to Port Scanning using Nmap
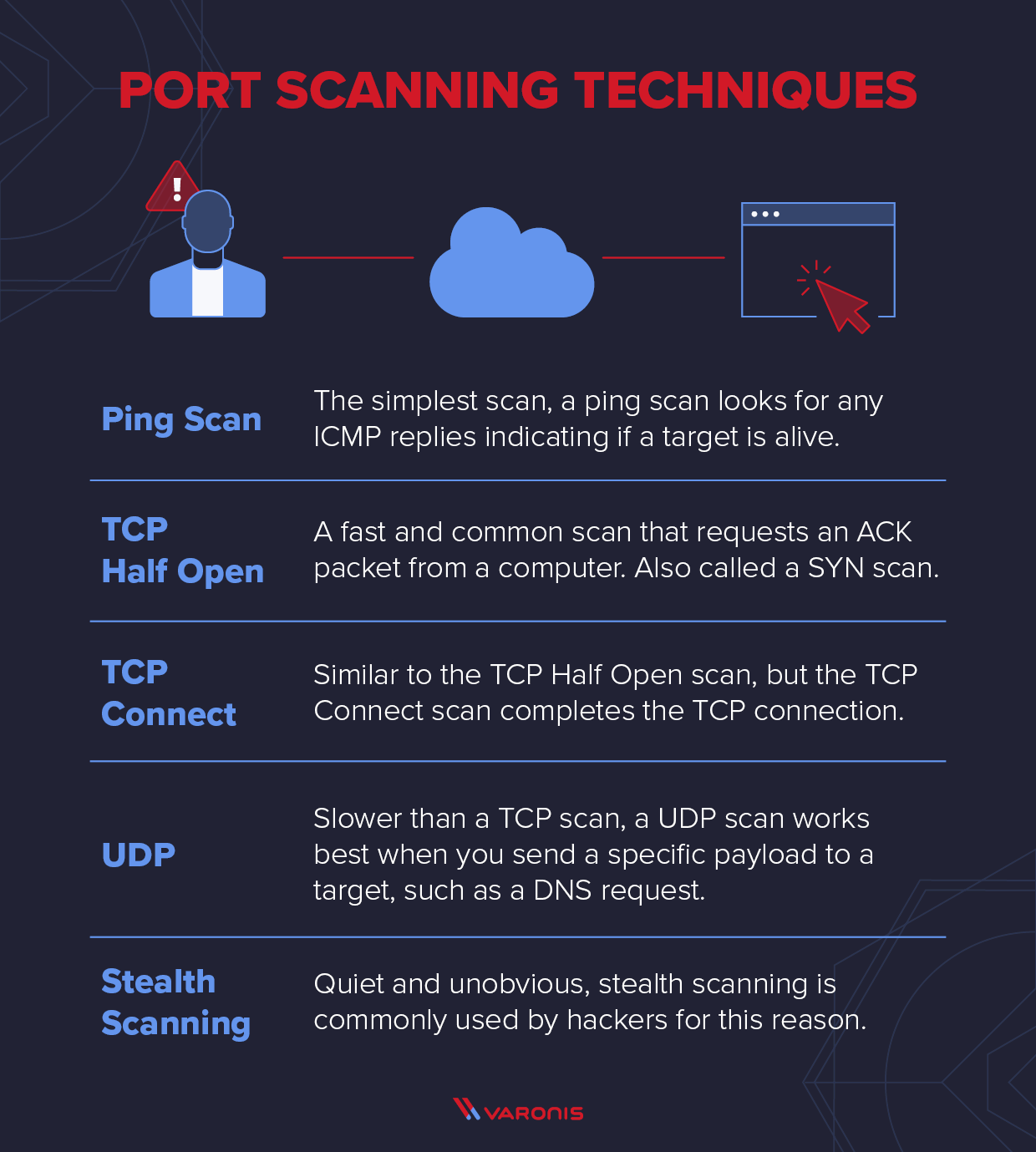
What is a Port Scanner and How Does it Work?
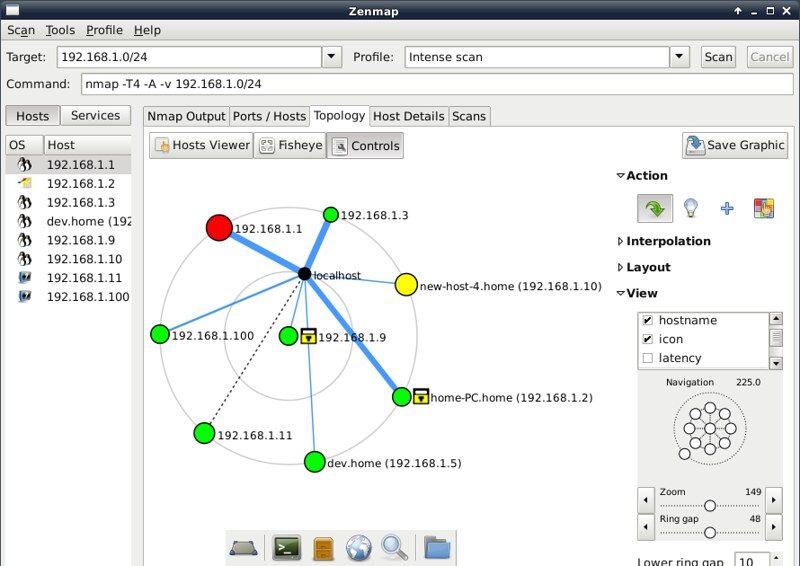
Port Scanning based Attacks

A Complete Guide to Nmap, Nmap Tutorial
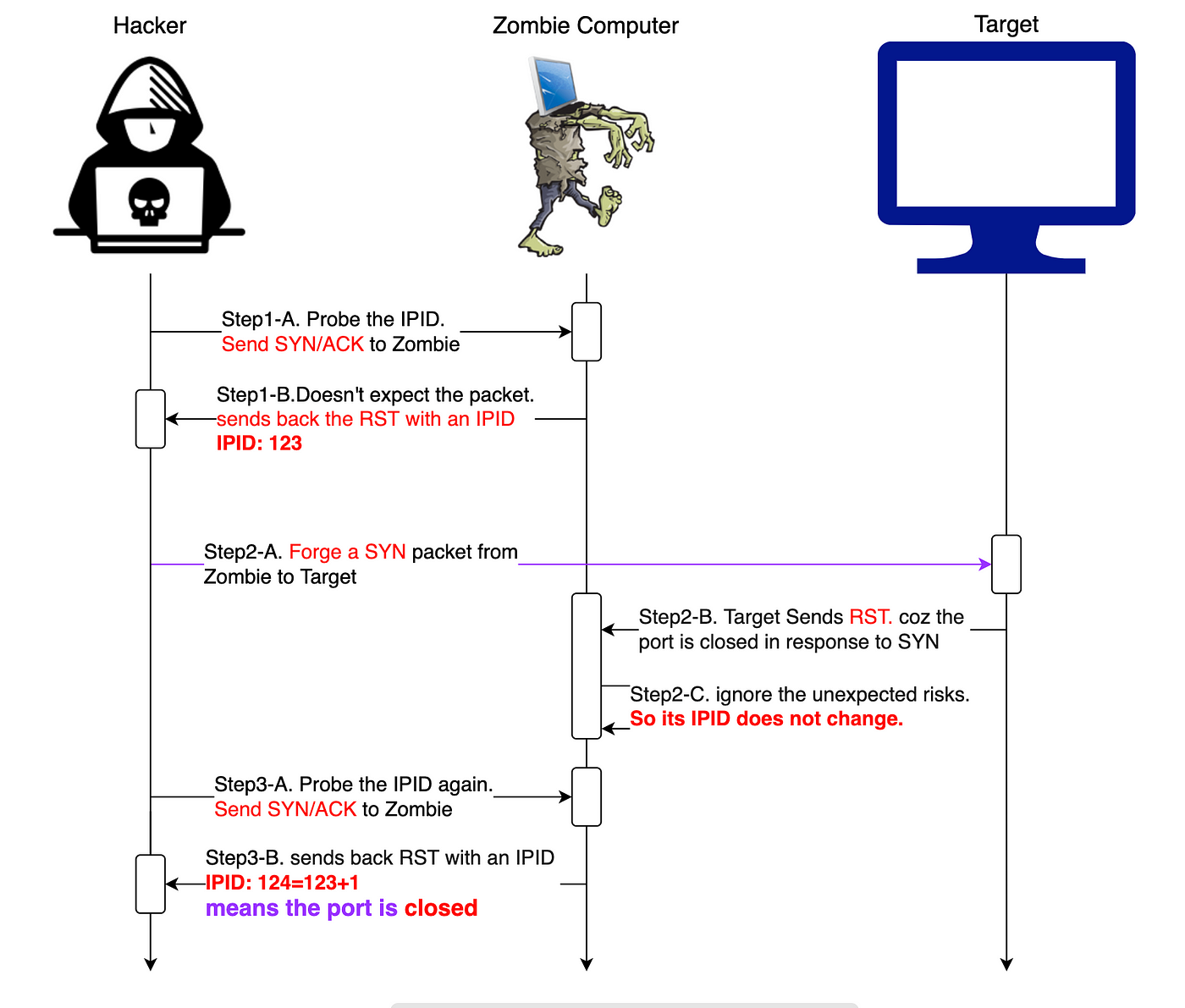
Zombie/Idle scan working principle, by NGU
Recomendado para você
-
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack29 maio 2024
-
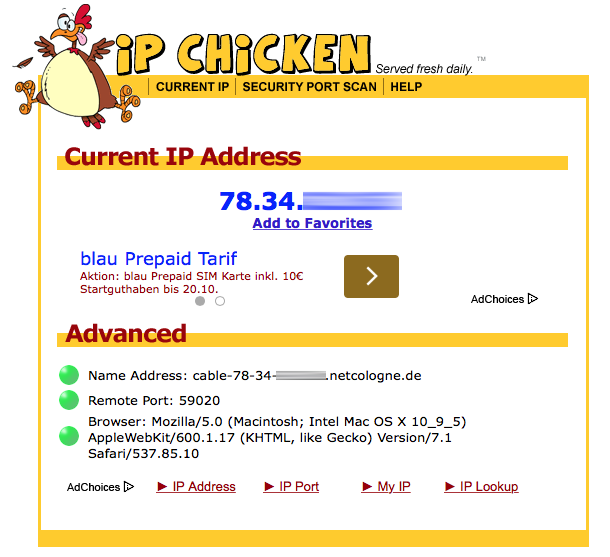 Read own IP address and check anonymization29 maio 2024
Read own IP address and check anonymization29 maio 2024 -
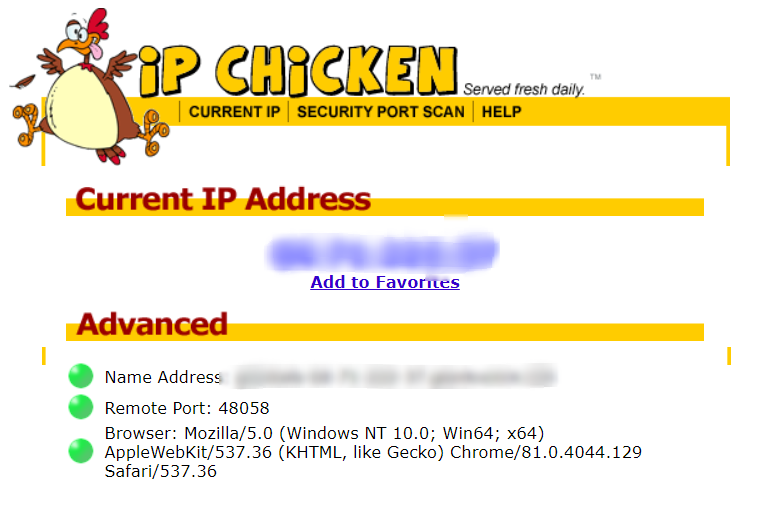 8 Sites That Show Your IP Address –29 maio 2024
8 Sites That Show Your IP Address –29 maio 2024 -
 Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community29 maio 2024
Xfinity won't add as sourceNot In Subscription - TV Everywhere - Channels Community29 maio 2024 -
 Port Scanner - an overview29 maio 2024
Port Scanner - an overview29 maio 2024 -
 Port Scan in Ethical Hacking - GeeksforGeeks29 maio 2024
Port Scan in Ethical Hacking - GeeksforGeeks29 maio 2024 -
Gogo's T-Mobile sponsored in-flight wifi? Free? On a PC?!29 maio 2024
-
Help Center29 maio 2024
-
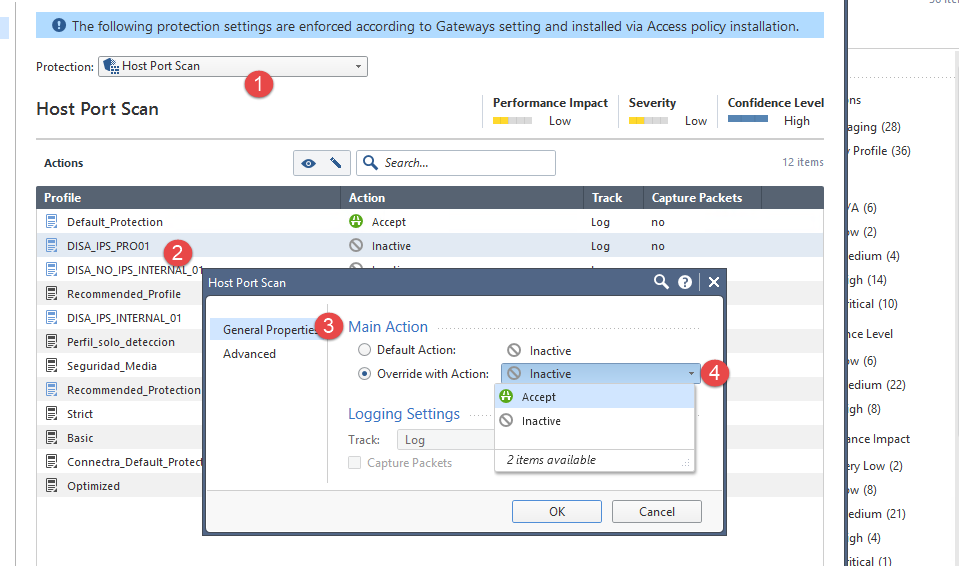 How can I avoid Host Port scan? - Check Point CheckMates29 maio 2024
How can I avoid Host Port scan? - Check Point CheckMates29 maio 2024 -
 LIVE from Radiance Apr. 21, 2023 - The Panama Canal - Canal au Niveau de la Mer - Page 14 - Royal Caribbean International - Cruise Critic Community29 maio 2024
LIVE from Radiance Apr. 21, 2023 - The Panama Canal - Canal au Niveau de la Mer - Page 14 - Royal Caribbean International - Cruise Critic Community29 maio 2024
você pode gostar
-
 Tomb Raider 2018 is coming to Netflix on December 16th! : r/TombRaider29 maio 2024
Tomb Raider 2018 is coming to Netflix on December 16th! : r/TombRaider29 maio 2024 -
 Jogadores de Fall Guys criticam modelo free-to-play: está menos divertido – Tecnoblog29 maio 2024
Jogadores de Fall Guys criticam modelo free-to-play: está menos divertido – Tecnoblog29 maio 2024 -
 L'Antartide è uno dei luoghi più freddi e inospitali della terra, vera patria della neve e del gelo, con temperature che possono essere inferiori a 50 gradi sotto lo zero e condizioni29 maio 2024
L'Antartide è uno dei luoghi più freddi e inospitali della terra, vera patria della neve e del gelo, con temperature che possono essere inferiori a 50 gradi sotto lo zero e condizioni29 maio 2024 -
 Love Is Blind' Is Ludicrous, But So Is Marriage29 maio 2024
Love Is Blind' Is Ludicrous, But So Is Marriage29 maio 2024 -
Man-made disaster! 😭😂 #fyp #fypシ #foryou #anime #animeedit #animerec29 maio 2024
-
 Velozes e Furiosos 9' ganha novo teaser (com muita ação e velocidade)29 maio 2024
Velozes e Furiosos 9' ganha novo teaser (com muita ação e velocidade)29 maio 2024 -
 Excursionistas vs Cañuelas H2H stats - SoccerPunter29 maio 2024
Excursionistas vs Cañuelas H2H stats - SoccerPunter29 maio 2024 -
 Guia de Arcos de Fairy Tail parte 129 maio 2024
Guia de Arcos de Fairy Tail parte 129 maio 2024 -
 Quick Puff Pastry - Cookidoo® – the official Thermomix® recipe29 maio 2024
Quick Puff Pastry - Cookidoo® – the official Thermomix® recipe29 maio 2024 -
Mikakunin de Shinkoukei Episode 03, By Anime Series29 maio 2024


