Malware analysis Malicious activity
Por um escritor misterioso
Last updated 01 outubro 2024
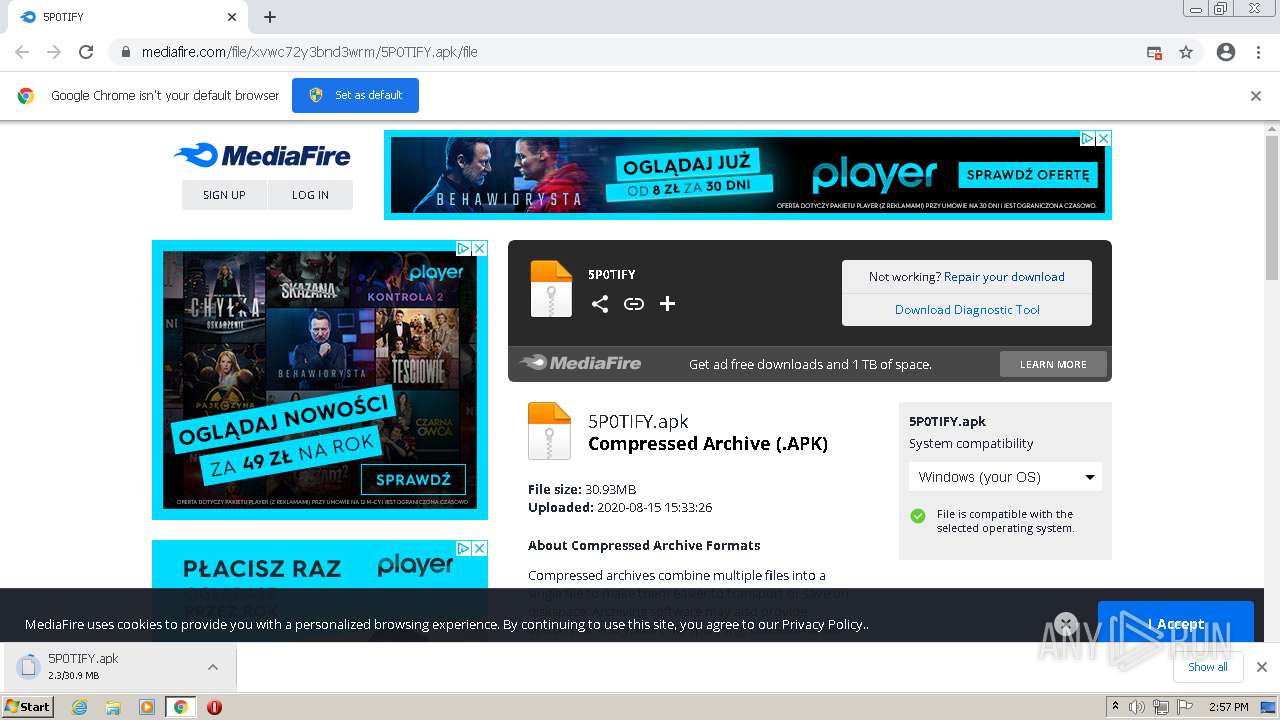

Detail procedure of malware analysis

Malware analysis Program_Install_and_Uninstall Malicious activity
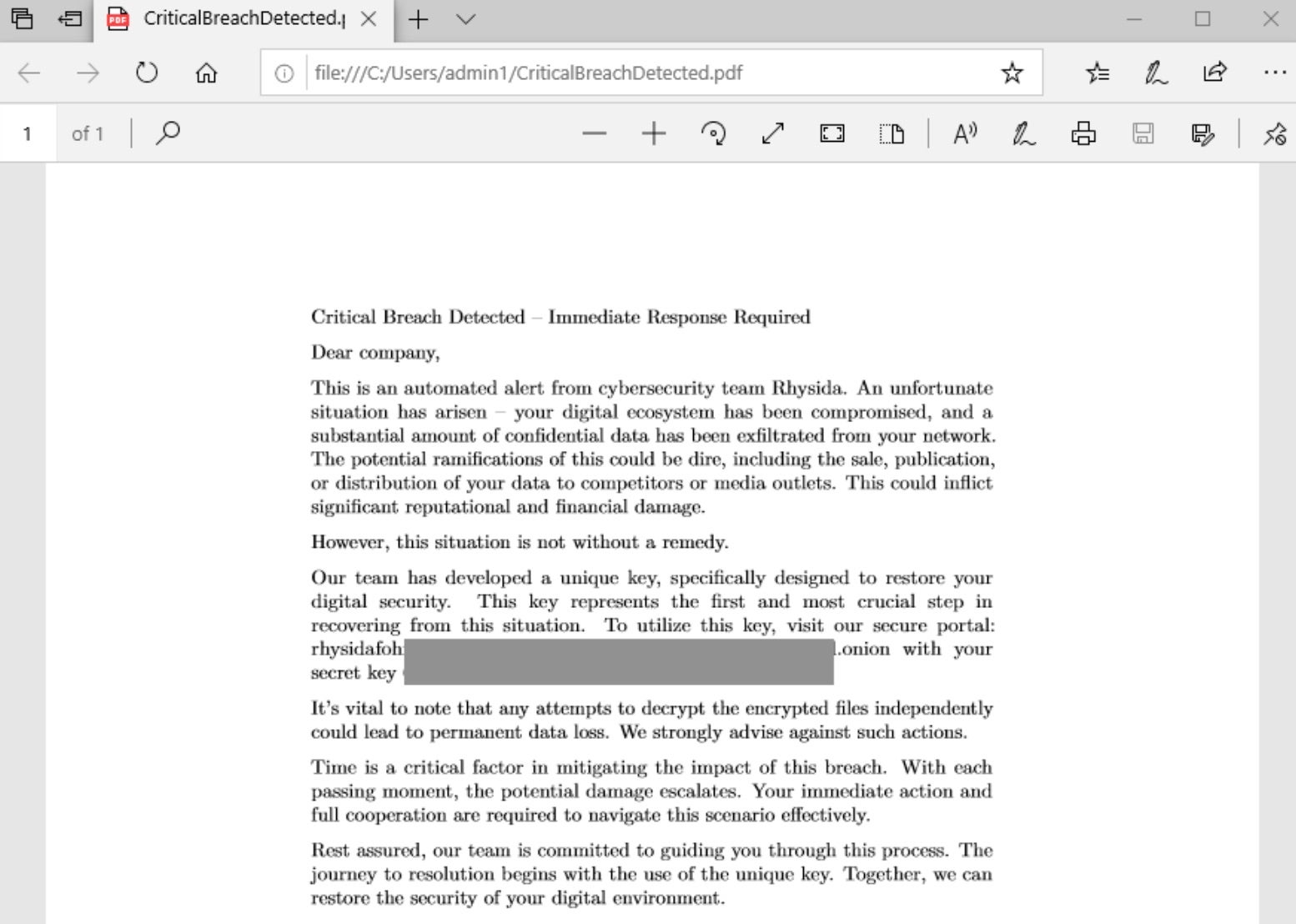
Rhysida - SentinelOne

Malware Analysis: Steps & Examples - CrowdStrike

Endpoint Detection and Response, Free - What is EDR Security?
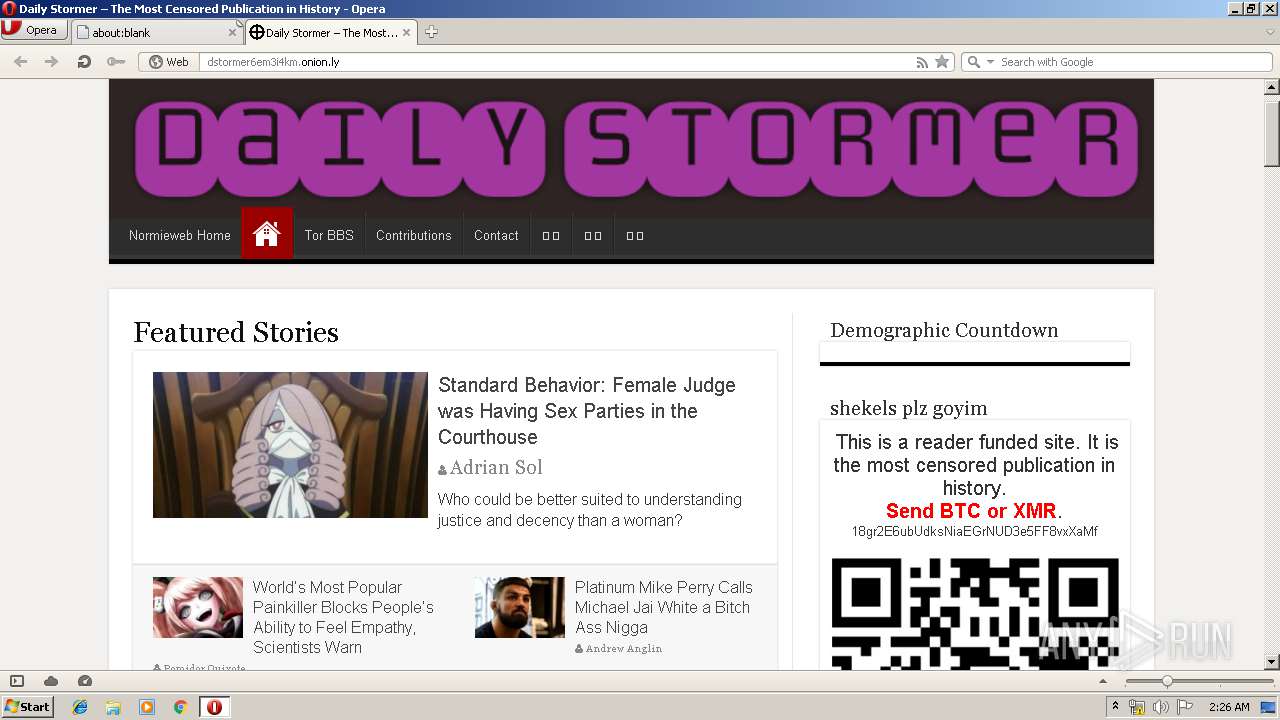
Malware analysis Malicious activity

Malware Analysis Benefits Incident Response

What is Malware? Definition, Types, Prevention - TechTarget
TryHackMe Hacktivities

Robust Malware Detection Models: Learning From Adversarial Attacks and Defenses - Forensic Focus

Dynamic malware analysis [34]

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
Recomendado para você
-
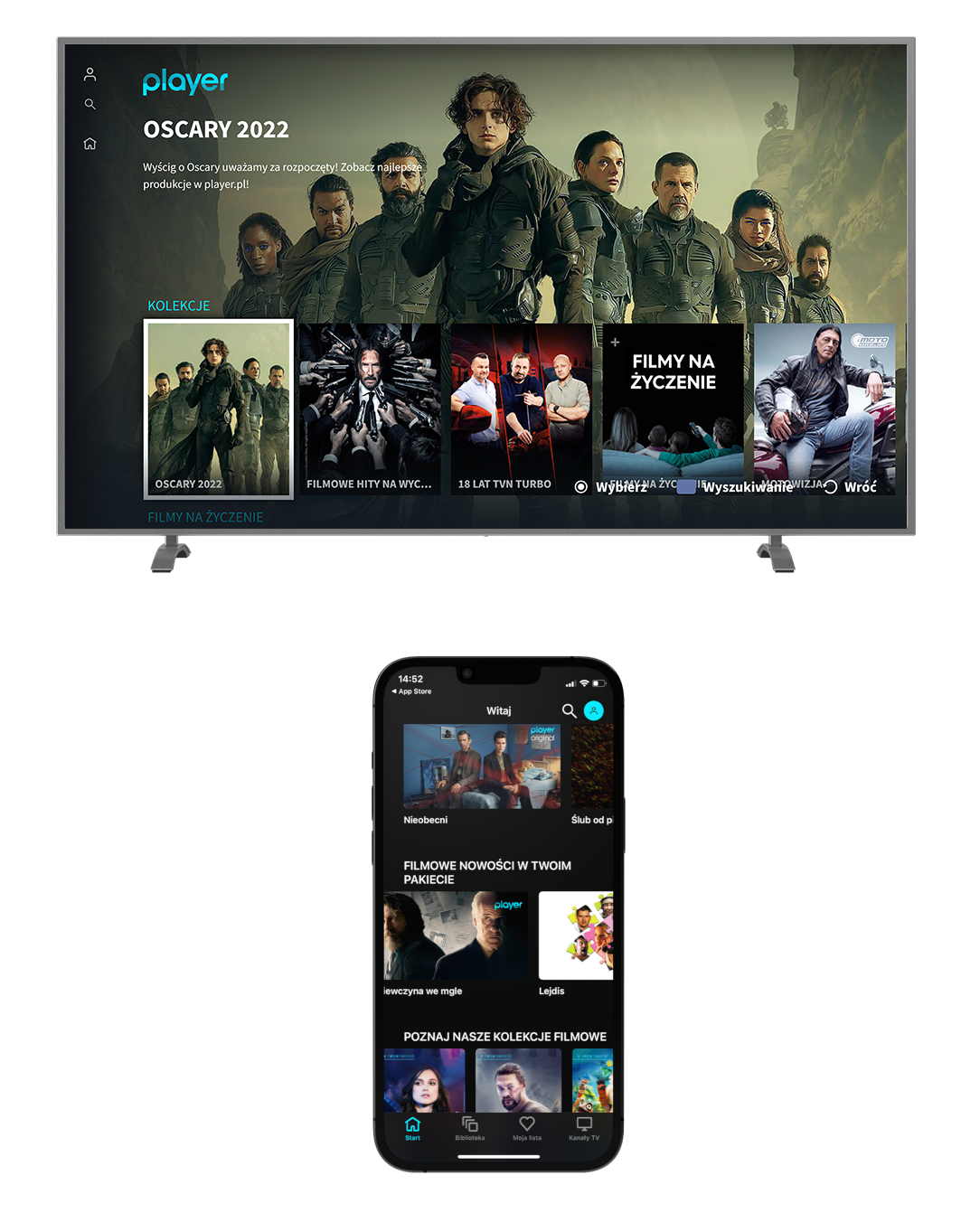
 Lista nowości w Player.pl – dodano 50 tytułów! 02.06.202101 outubro 2024
Lista nowości w Player.pl – dodano 50 tytułów! 02.06.202101 outubro 2024 -
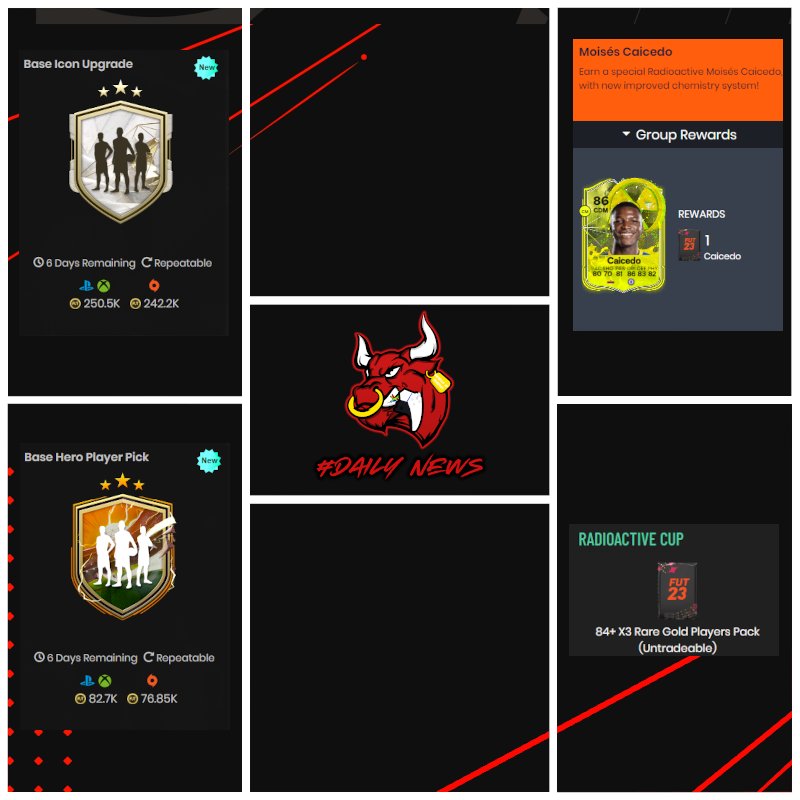 Rebels Of Trading (@RebelsOfTrading) / X01 outubro 2024
Rebels Of Trading (@RebelsOfTrading) / X01 outubro 2024 -
BoB & Maax Event Team01 outubro 2024
-
Wkrótce na Playerze - wrześniowe nowości - PC World - Testy i Ceny01 outubro 2024
-
 Redge Media Video solutions and products used by millions of01 outubro 2024
Redge Media Video solutions and products used by millions of01 outubro 2024 -
 EMKA: Sponsorowanie01 outubro 2024
EMKA: Sponsorowanie01 outubro 2024 -
![NAMM'18: Fender i akustyczne nowości [VIDEO]](https://www.infogitara.pl/img/artykuly/958w/fender-malibu-newporter-redondopm-2e-pm-4ce-paramount-california-player-california-special-california-classic-49725.webp?1682109256) NAMM'18: Fender i akustyczne nowości [VIDEO]01 outubro 2024
NAMM'18: Fender i akustyczne nowości [VIDEO]01 outubro 2024 -
 Serialowe nowości Playera na wiosnę. „Herkules”, „Tajemnica zawodowa”, „Nieobecni” i „Kontrola”01 outubro 2024
Serialowe nowości Playera na wiosnę. „Herkules”, „Tajemnica zawodowa”, „Nieobecni” i „Kontrola”01 outubro 2024 -
 Chyba nie doceniałem Player.pl – mają niezłą bibliotekę filmów, ale nie jest tak różowo01 outubro 2024
Chyba nie doceniałem Player.pl – mają niezłą bibliotekę filmów, ale nie jest tak różowo01 outubro 2024 -
Player Sierpień 2023 – filmy, seriale i programy. Imponująca lista01 outubro 2024
você pode gostar
-
Seeing our favorite people at Pro tire best place for service!01 outubro 2024
-
 Upcoming Chinese Anime: Brainless Witch (Wu Nao Monü) / Agate01 outubro 2024
Upcoming Chinese Anime: Brainless Witch (Wu Nao Monü) / Agate01 outubro 2024 -
Steaua-Barcelona 2-0 [1986]#fy #fyp #fypシ #foryou #foryourpage #trend TikTok01 outubro 2024
-
Shoujo - Brasil - Um temático clichê de fantasia Bela e a fera aos órfãs de Mahoutsukai que gostam de todo esse ambiente fantasioso com desenvolvimento bom dos personagens, já deixa Niehime01 outubro 2024
-
 Can You Make It Virgin?, Twitter / X01 outubro 2024
Can You Make It Virgin?, Twitter / X01 outubro 2024 -
Baixar Jogos Gratis Para Celular01 outubro 2024
-
 Here's The Exact Time The 'Call Of Duty: Modern Warfare III01 outubro 2024
Here's The Exact Time The 'Call Of Duty: Modern Warfare III01 outubro 2024 -
 cute animals Trending Gifs01 outubro 2024
cute animals Trending Gifs01 outubro 2024 -
 Quiz de futebol01 outubro 2024
Quiz de futebol01 outubro 2024 -
 Jetpack Mammoth Thruster V2 GTA V for GTA San Andreas01 outubro 2024
Jetpack Mammoth Thruster V2 GTA V for GTA San Andreas01 outubro 2024



![Steaua-Barcelona 2-0 [1986]#fy #fyp #fypシ #foryou #foryourpage #trend TikTok](https://www.tiktok.com/api/img/?itemId=7150993052377664774&location=0&aid=1988)

