Malware analysis Malicious activity
Por um escritor misterioso
Last updated 04 junho 2024

Cybersecurity Search Engine

Cybersecurity Search Engine

Rising threats: Cybercriminals unleash 411,000 malicious files

Malware analysis index.html Malicious activity

Malware Analysis Framework v1.0

Malware Analysis: Steps & Examples - CrowdStrike

What Is Malware Analysis? Definition, Types, Stages, and Best

Malware Analysis: Steps & Examples - CrowdStrike
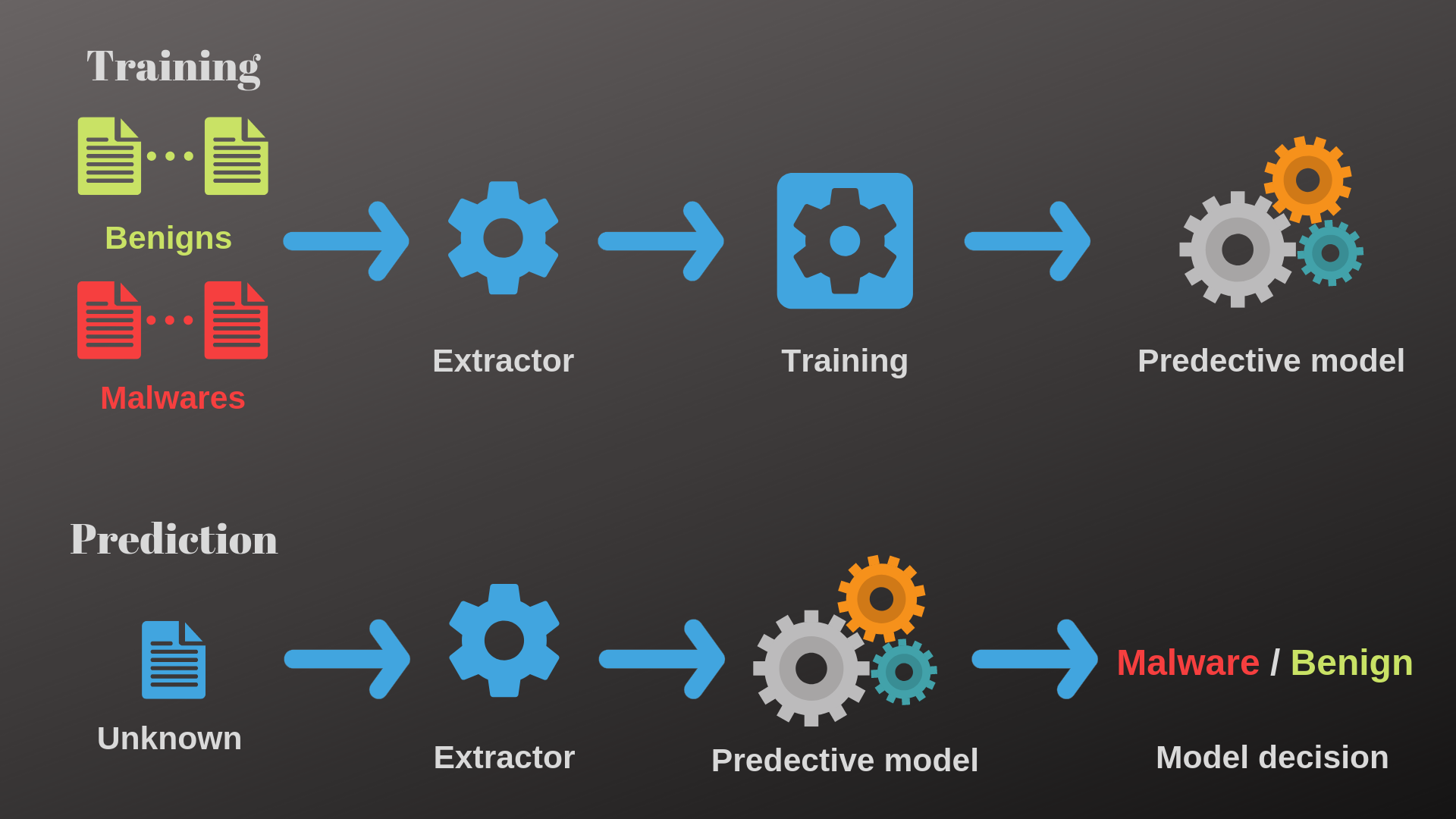
Feature Extraction and Detection of Malwares Using Machine
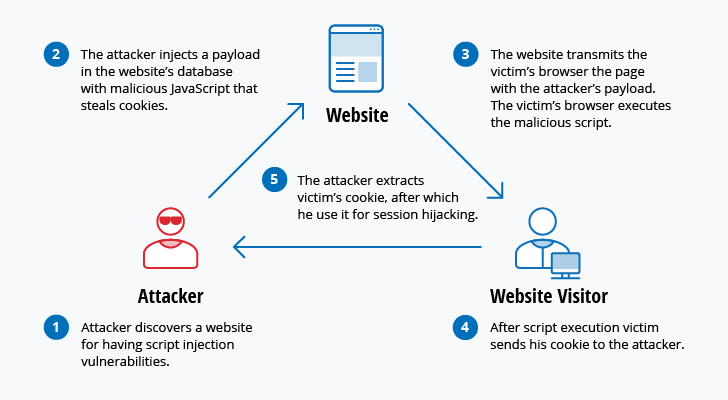
The 12 Most Common Types of Cybersecurity Attacks Today

Endpoint Detection and Response, Free - What is EDR Security?

Malware analysis file Malicious activity
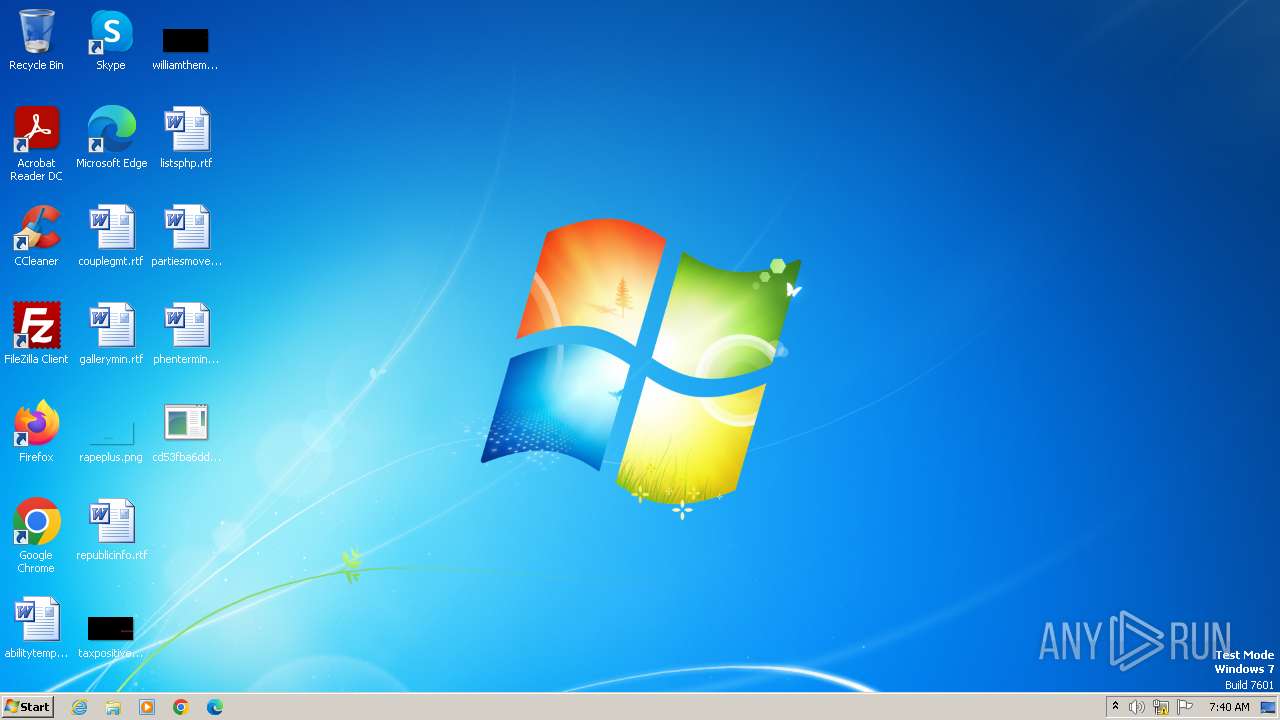
Malware analysis

PROUD-MAL: static analysis-based progressive framework for deep

Info stealers and how to protect against them
Recomendado para você
-
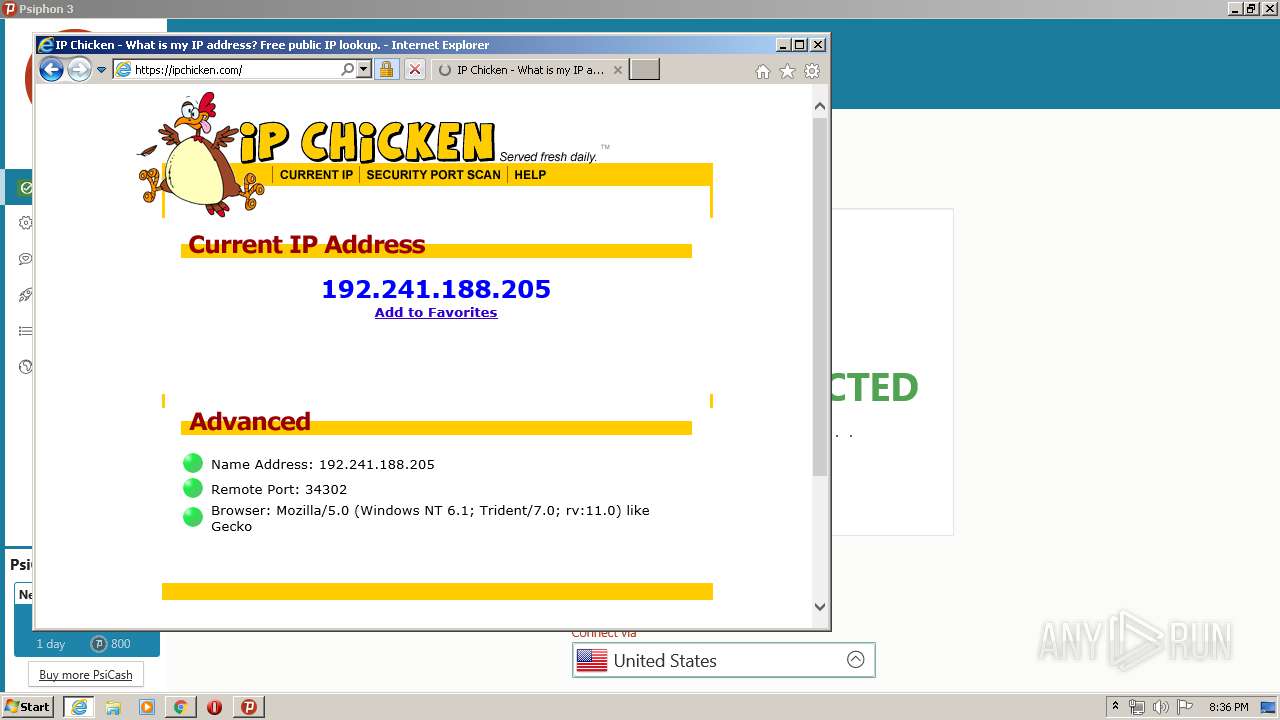
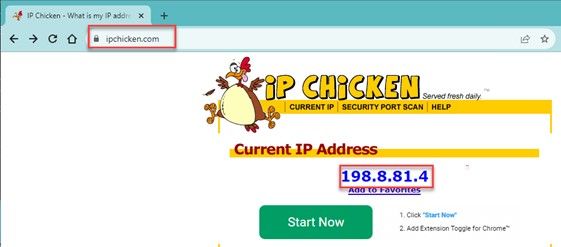
 IPChicken, Woo hoo! Lightspeed!, Richard De Guzman04 junho 2024
IPChicken, Woo hoo! Lightspeed!, Richard De Guzman04 junho 2024 -
 Away Viewing Fix - Dynamic URL Change, WiFi Baby, Compare Baby Monitors 201904 junho 2024
Away Viewing Fix - Dynamic URL Change, WiFi Baby, Compare Baby Monitors 201904 junho 2024 -
 How to Bypass Internet Censorship04 junho 2024
How to Bypass Internet Censorship04 junho 2024 -
 Configuring private V2Ray server for bypassing internet censorship (TLS configuration)04 junho 2024
Configuring private V2Ray server for bypassing internet censorship (TLS configuration)04 junho 2024 -
 Port Scan in Ethical Hacking - GeeksforGeeks04 junho 2024
Port Scan in Ethical Hacking - GeeksforGeeks04 junho 2024 -
 What is Tor Browser & How to Setup Tor04 junho 2024
What is Tor Browser & How to Setup Tor04 junho 2024 -
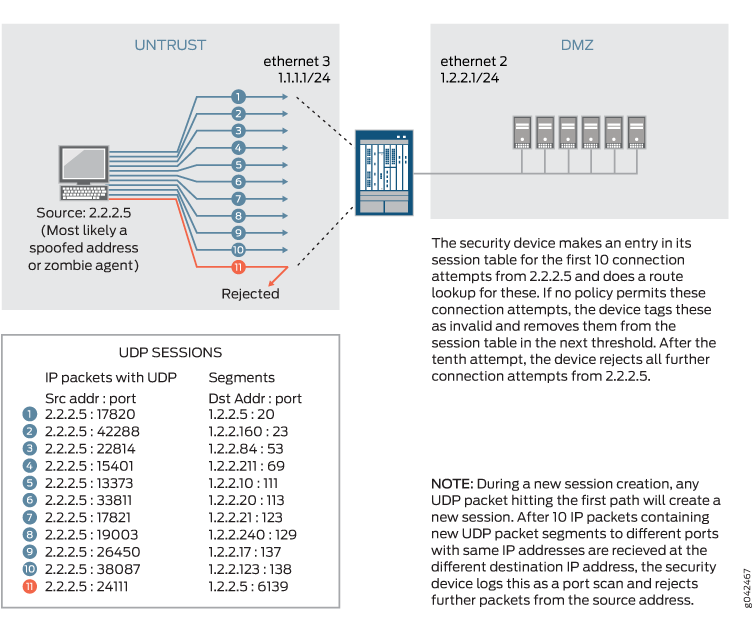 IP Address Sweep and Port Scan, Junos OS04 junho 2024
IP Address Sweep and Port Scan, Junos OS04 junho 2024 -
 Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager04 junho 2024
Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager04 junho 2024 -
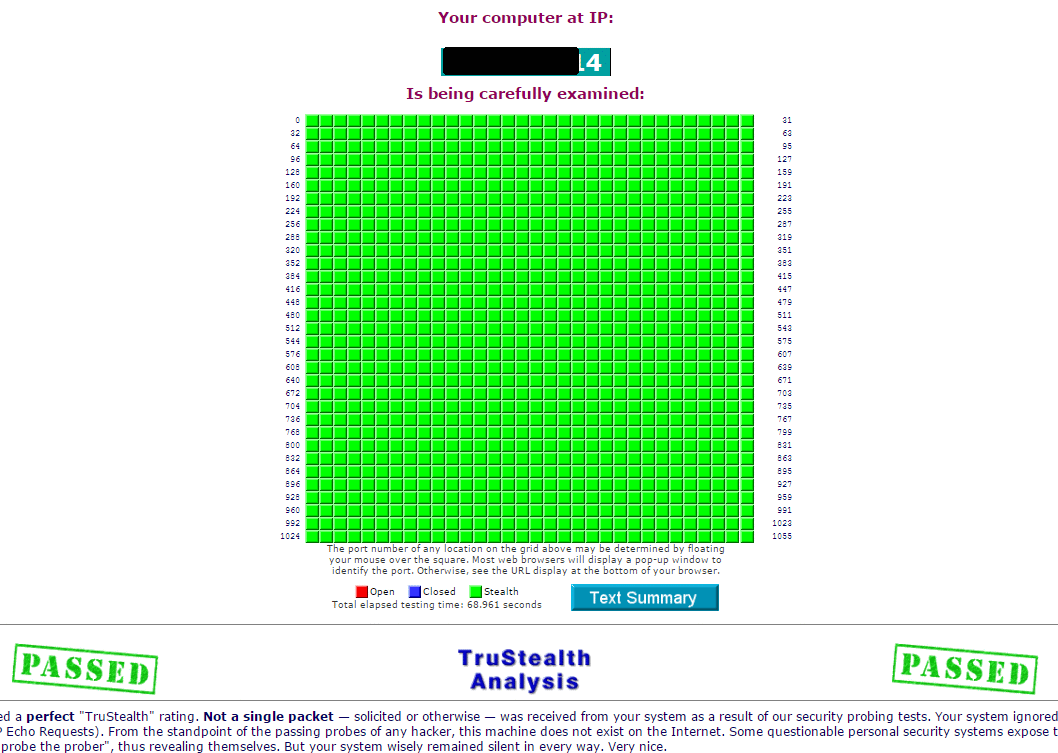 Test Your Router04 junho 2024
Test Your Router04 junho 2024 -
Wireshark: Port-Scanning Download Scientific Diagram04 junho 2024
você pode gostar
-
 My Furry Protogen 🐾04 junho 2024
My Furry Protogen 🐾04 junho 2024 -
 NIER REPLICANT -10+1 YEARS- / KAINÉ04 junho 2024
NIER REPLICANT -10+1 YEARS- / KAINÉ04 junho 2024 -
 Jumbo Atacadista - Curitiba, PR04 junho 2024
Jumbo Atacadista - Curitiba, PR04 junho 2024 -
 Starfield Best Mods for Nexus and PC - GameWith04 junho 2024
Starfield Best Mods for Nexus and PC - GameWith04 junho 2024 -
 The Originals 3x16: finalmente foi revelado quem está traindo os Mikaelson04 junho 2024
The Originals 3x16: finalmente foi revelado quem está traindo os Mikaelson04 junho 2024 -
 𝐇𝐚𝐠𝐚𝐧𝐞𝐳𝐮𝐤𝐚 𝐇𝐨𝐭𝐚𝐫𝐮 (@SWRDSMITH) / X04 junho 2024
𝐇𝐚𝐠𝐚𝐧𝐞𝐳𝐮𝐤𝐚 𝐇𝐨𝐭𝐚𝐫𝐮 (@SWRDSMITH) / X04 junho 2024 -
 Speed Machines Worksheet Answer Key - Fill and Sign Printable Template Online04 junho 2024
Speed Machines Worksheet Answer Key - Fill and Sign Printable Template Online04 junho 2024 -
 15 ideias de Homem Aranha para Colorir homem aranha, colorir, homem aranha desenho04 junho 2024
15 ideias de Homem Aranha para Colorir homem aranha, colorir, homem aranha desenho04 junho 2024 -
 Cómo conseguir a Shaymin forma Cielo en Pokémon GO - Movistar eSports04 junho 2024
Cómo conseguir a Shaymin forma Cielo en Pokémon GO - Movistar eSports04 junho 2024 -
 Xit Free Fire 🍓🏆 - DFG04 junho 2024
Xit Free Fire 🍓🏆 - DFG04 junho 2024