Open Files: How Do You Exploit them?
Por um escritor misterioso
Last updated 31 outubro 2024

It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…
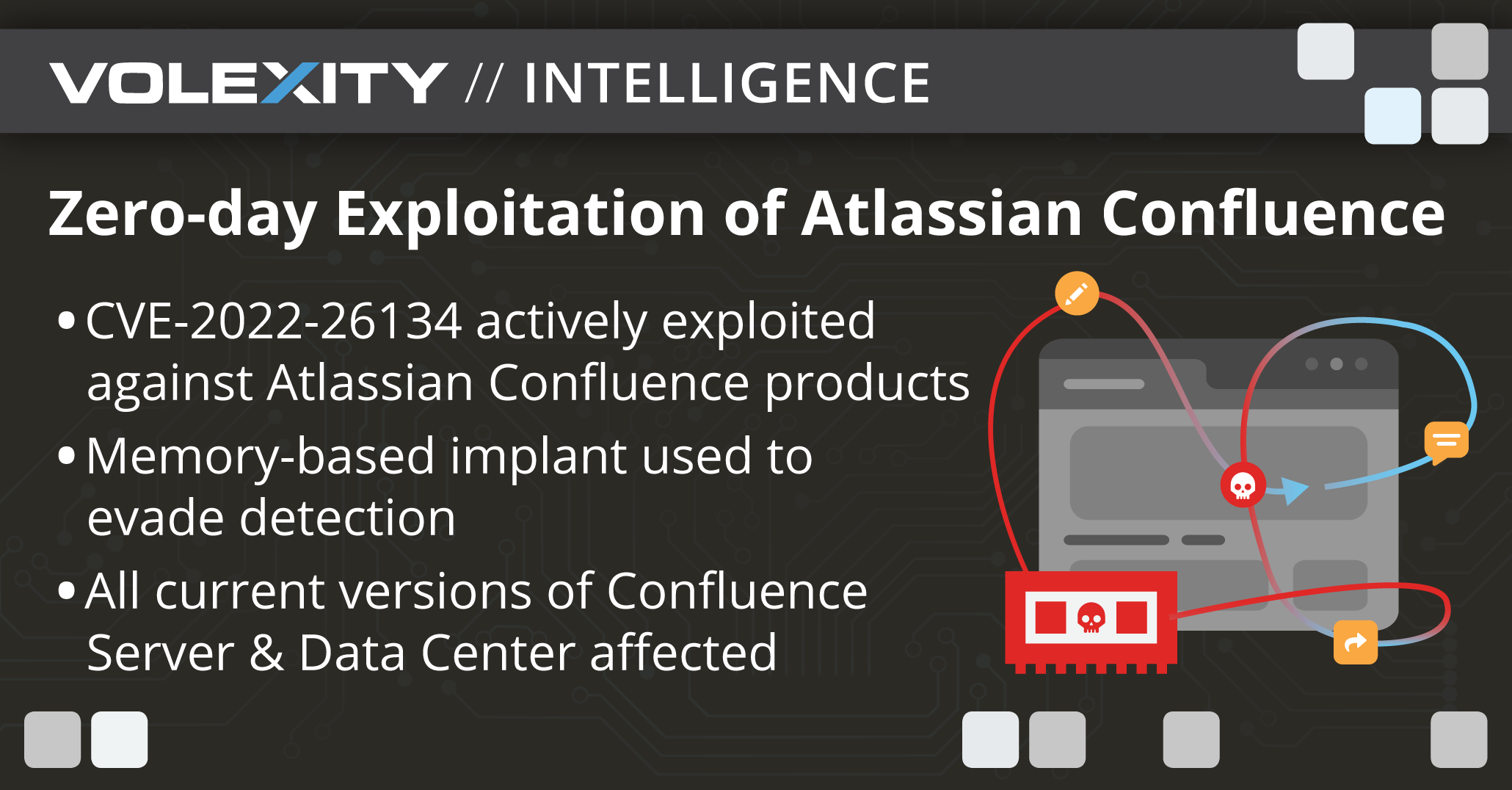
Zero-Day Exploitation of Atlassian Confluence
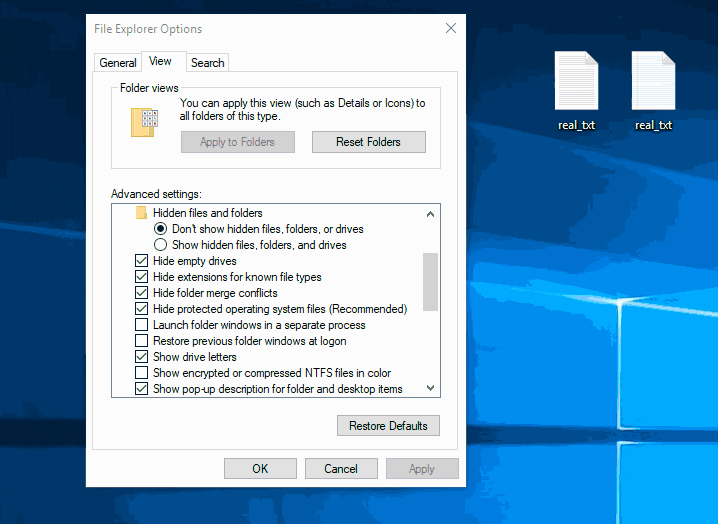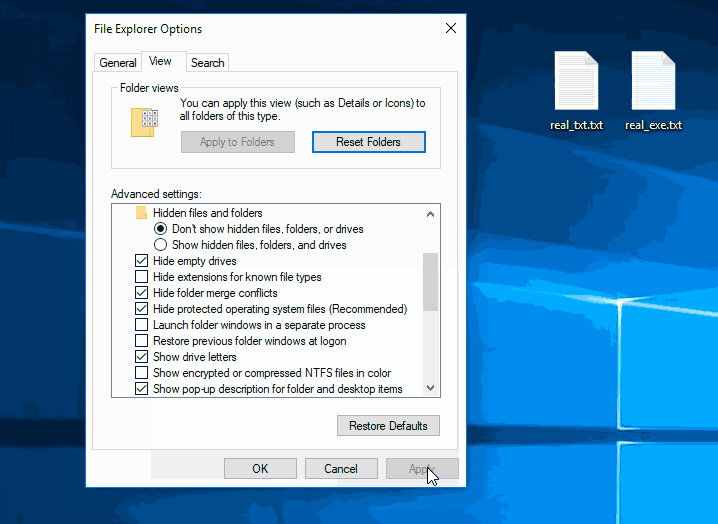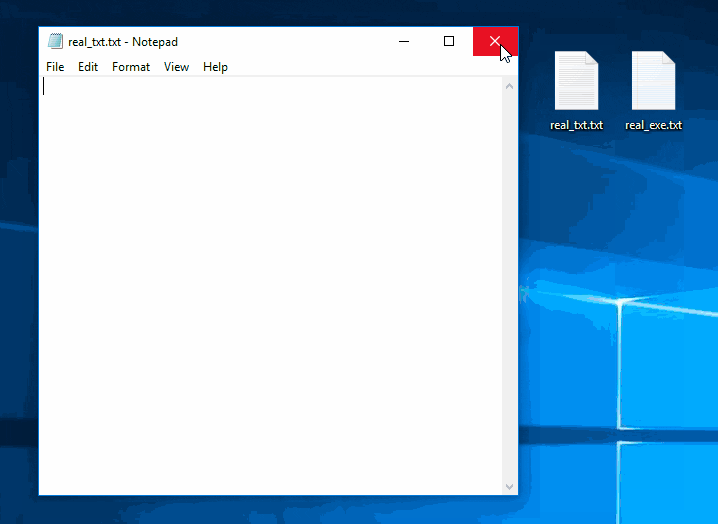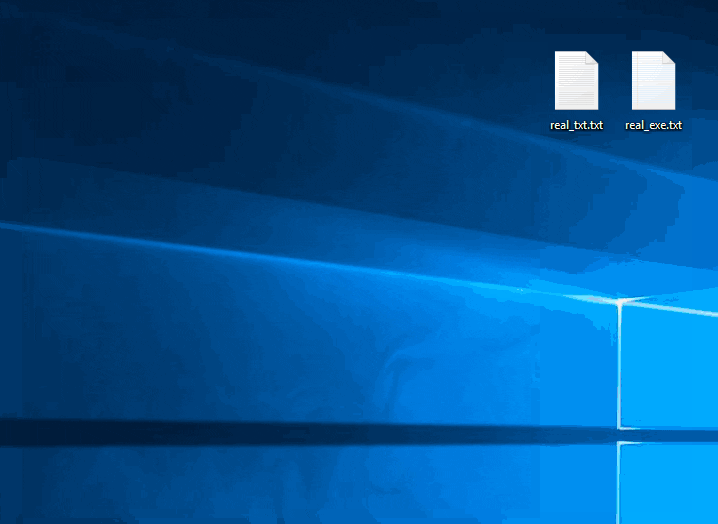
Hacking Windows 10: How to Create an Undetectable Payload, Part 2 (Concealing the Payload) « Null Byte :: WonderHowTo
Zero-day in Microsoft Windows used in Nokoyawa ransomware attacks
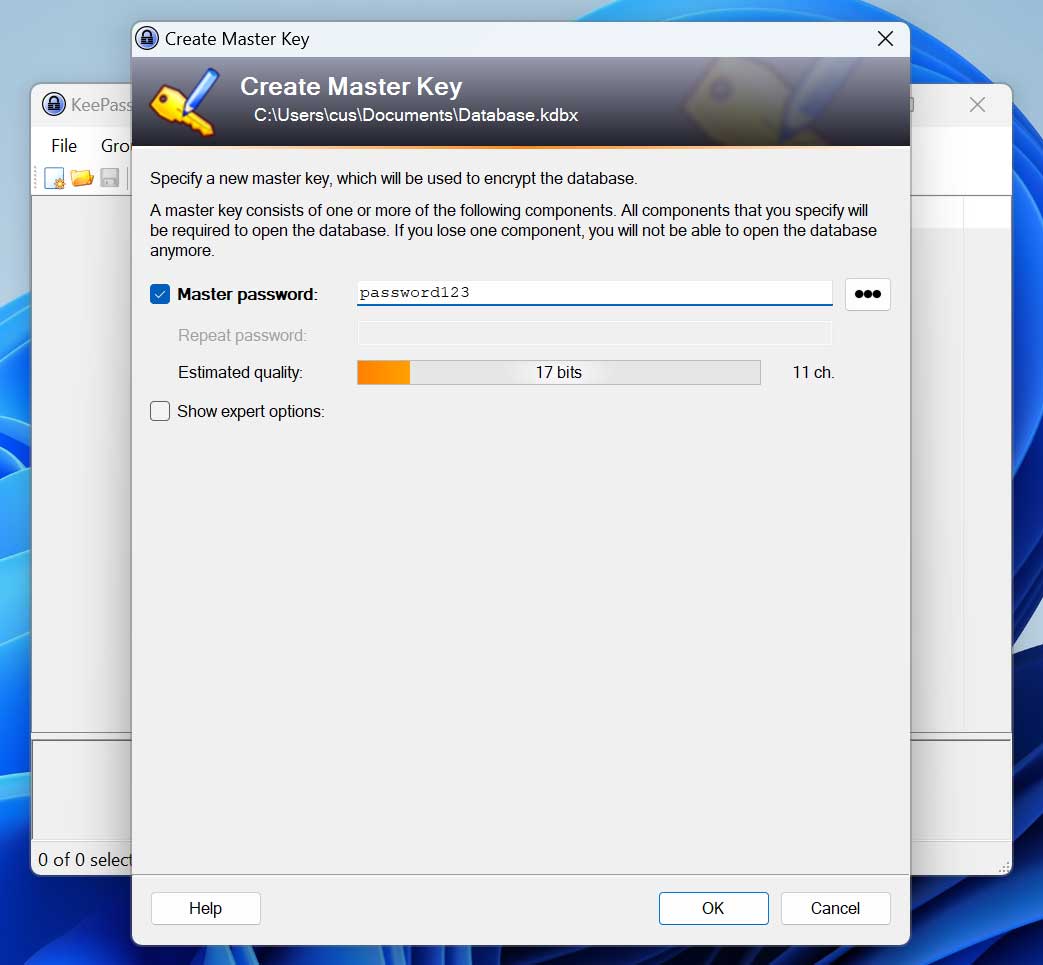
KeePass exploit helps retrieve cleartext master password, fix coming soon

Embedding backdoor into PDF files, by David Artykov, Purple Team

Hex Editor - Exploit Pack - Documentation
Hack The Box — Starting Point “Responder” Solution, by Carla Ferreira, Rakulee
Kernel Exploits Part 2 – Windows Privilege Escalation
How to Exploit Remote File Inclusion to Get a Shell « Null Byte :: WonderHowTo
Recomendado para você
-
Rules of Chess: Pawns FAQ31 outubro 2024
-
 Chess Pieces 101: Names, Moves, and Value - The School Of Rook31 outubro 2024
Chess Pieces 101: Names, Moves, and Value - The School Of Rook31 outubro 2024 -
 Piece Positioning: Rooks31 outubro 2024
Piece Positioning: Rooks31 outubro 2024 -
:max_bytes(150000):strip_icc()/castling-promotion-and-en-passant-611548FINAL-00d1403bfff445c3baac34820121803b.jpg) Special Chess Moves: Castling, Promotion, and En Passant31 outubro 2024
Special Chess Moves: Castling, Promotion, and En Passant31 outubro 2024 -
Chess Rooks Problem - Apps on Google Play31 outubro 2024
-
 Rules of Chess31 outubro 2024
Rules of Chess31 outubro 2024 -
 chess - Students, Britannica Kids31 outubro 2024
chess - Students, Britannica Kids31 outubro 2024 -
 Pin on Chess Worksheets31 outubro 2024
Pin on Chess Worksheets31 outubro 2024 -
 8 Awkwardly placed hanging rooks and 7 queening pawns cannot stop31 outubro 2024
8 Awkwardly placed hanging rooks and 7 queening pawns cannot stop31 outubro 2024 -
 Rook's graph - Wikipedia31 outubro 2024
Rook's graph - Wikipedia31 outubro 2024
você pode gostar
-
 My Little Pony the Movie31 outubro 2024
My Little Pony the Movie31 outubro 2024 -
 Hacks - Sonic & Johnny31 outubro 2024
Hacks - Sonic & Johnny31 outubro 2024 -
 Pheromosa, Pokémon Wiki31 outubro 2024
Pheromosa, Pokémon Wiki31 outubro 2024 -
 thepirat.asia - Download music, movies, games, - The Pirate Bay31 outubro 2024
thepirat.asia - Download music, movies, games, - The Pirate Bay31 outubro 2024 -
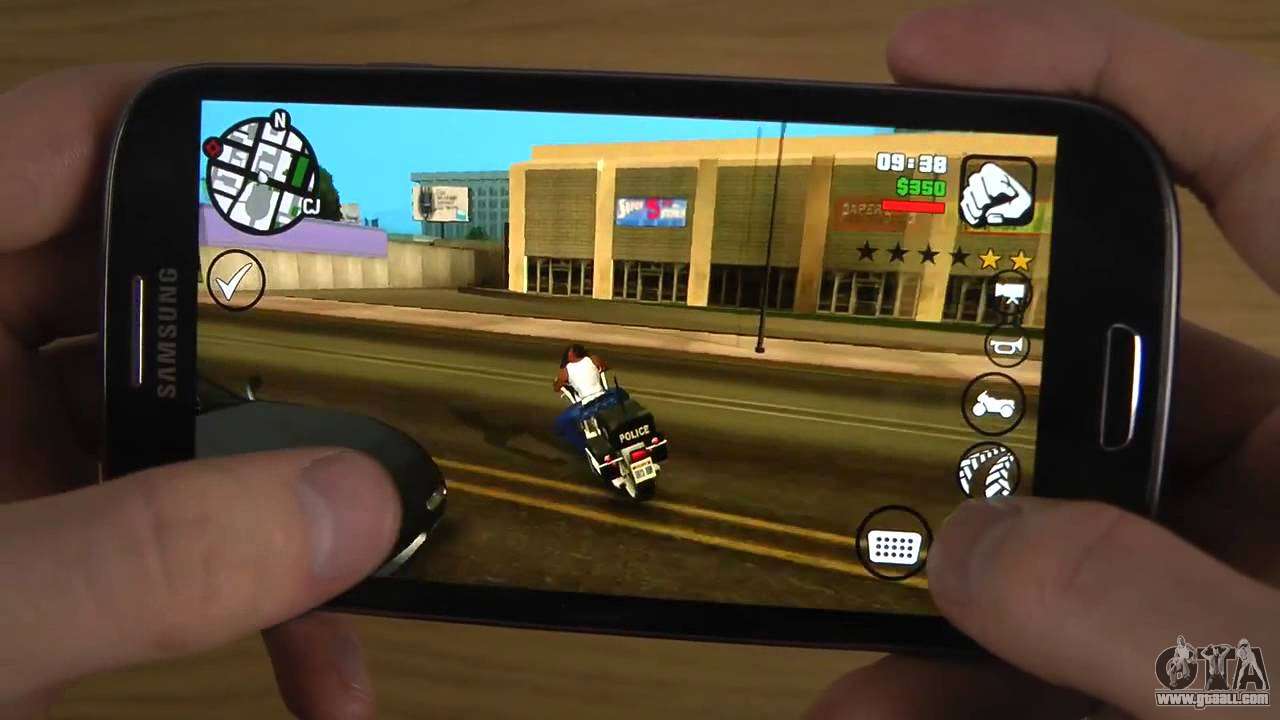 All about GTA San Andreas Android. Codes, cheats and mods for the game GTA San Andreas only with us!31 outubro 2024
All about GTA San Andreas Android. Codes, cheats and mods for the game GTA San Andreas only with us!31 outubro 2024 -
 Arapongas adere ao Concurso “Entre Caminhos do Paraná” promovido31 outubro 2024
Arapongas adere ao Concurso “Entre Caminhos do Paraná” promovido31 outubro 2024 -
 How to Draw Naruto Uzumaki, Face, Naruto31 outubro 2024
How to Draw Naruto Uzumaki, Face, Naruto31 outubro 2024 -
 Norway Chess 2021 - Alireza Firouzja VS Sergey Karjakin (Round 331 outubro 2024
Norway Chess 2021 - Alireza Firouzja VS Sergey Karjakin (Round 331 outubro 2024 -
 CrepProtect31 outubro 2024
CrepProtect31 outubro 2024 -
buch7-Kulturbahnhof gemeinnützige GmbH31 outubro 2024
