SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 28 maio 2024

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

hacking news, Breaking Cybersecurity News

Lynx-CERT

Endpoint Protection - Symantec Enterprise
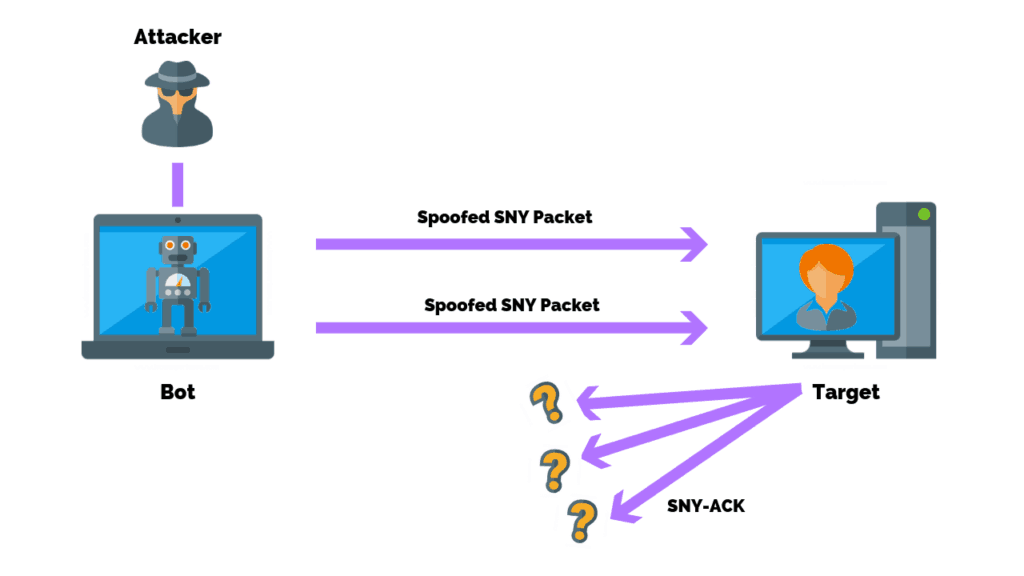
How To Prevent Network Attacks

Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection

MALWARE DETECTION : EVASION TECHNIQUES - CYFIRMA

Chinese Hackers Use New Cryptojacking Tactics to Evade Detection

How Hackers Are “Blending In” to Evade Detection

Microsoft Warns of Stealthy Outlook Vulnerability Exploited by Russian Hackers : r/RedPacketSecurity

Chinese and Russian Hackers Using SILKLOADER Malware to Evade Detection

Black Arrow Cyber Consulting — Black Arrow Cyber Threat Briefing 17 March 2023

Exaramel Malware Links Industroyer ICS malware and NotPetya wiper

Cobalt Strike malware campaign targets job seekers

How Hackers Are “Blending In” to Evade Detection

Companies on alert after apparent hack of cloud-based security camera service
Recomendado para você
-
 When byte code bites: Who checks the contents of compiled Python28 maio 2024
When byte code bites: Who checks the contents of compiled Python28 maio 2024 -
 Evade Script Auto Farm & Esp Gui - Updated Pastebin Script28 maio 2024
Evade Script Auto Farm & Esp Gui - Updated Pastebin Script28 maio 2024 -
![Evade [AutoRespawn, Esp] Scripts](https://rbxscript.com/images/-KAgv5dirUs-image.jpg) Evade [AutoRespawn, Esp] Scripts28 maio 2024
Evade [AutoRespawn, Esp] Scripts28 maio 2024 -
 Evade Script/GUI Review28 maio 2024
Evade Script/GUI Review28 maio 2024 -
Snippet of Server-side script generated by ChatGPT to evade28 maio 2024
-
 2 Late 2 Evade by Script Idea28 maio 2024
2 Late 2 Evade by Script Idea28 maio 2024 -
 How Egyptians are using an ancient Arabic script to evade censors28 maio 2024
How Egyptians are using an ancient Arabic script to evade censors28 maio 2024 -
![Lol Hack] Script De Graça - Evade/Skillshot/Autofarm + - League Of](https://cdn.dfg.com.br/itemimages/935620138-lol-hack-script-de-graca-evade-skillshot-autofarm-TRH2.webp) Lol Hack] Script De Graça - Evade/Skillshot/Autofarm + - League Of28 maio 2024
Lol Hack] Script De Graça - Evade/Skillshot/Autofarm + - League Of28 maio 2024 -
 Reference attack model: an attacker embeds a malicious script into28 maio 2024
Reference attack model: an attacker embeds a malicious script into28 maio 2024 -
Solved How could an adversary obtain remote screen access to28 maio 2024
você pode gostar
-
 One Piece Film Gold The Straw Hat Pirates Luffy Zoro Nami Usopp28 maio 2024
One Piece Film Gold The Straw Hat Pirates Luffy Zoro Nami Usopp28 maio 2024 -
 Juliet Starling of Lollipop Chainsaw cosplay by Jessica Ni…28 maio 2024
Juliet Starling of Lollipop Chainsaw cosplay by Jessica Ni…28 maio 2024 -
 The Play Report: Experts discuss their favorite apps and games28 maio 2024
The Play Report: Experts discuss their favorite apps and games28 maio 2024 -
![Surfer SEO Review [2023]: Pricing & Demo (+3 Case Studies)](https://www.freedomboundbusiness.com/wp-content/uploads/2020/03/SurferSEO-Content-Editor-Screen.jpg) Surfer SEO Review [2023]: Pricing & Demo (+3 Case Studies)28 maio 2024
Surfer SEO Review [2023]: Pricing & Demo (+3 Case Studies)28 maio 2024 -
 ⚫🔴 paiN com mudança TOTAL! Piorou ou apostou a longo prazo28 maio 2024
⚫🔴 paiN com mudança TOTAL! Piorou ou apostou a longo prazo28 maio 2024 -
 Zack Snyder Reveals Rebel Moon's Explosive First Trailer and Part 2 Release Date - IGN28 maio 2024
Zack Snyder Reveals Rebel Moon's Explosive First Trailer and Part 2 Release Date - IGN28 maio 2024 -
 Libertadores 2023 terá clubes tradicionais, estreantes e um retorno; Veja os classificados - Fluminense: Últimas notícias, vídeos, onde assistir e próximos jogos28 maio 2024
Libertadores 2023 terá clubes tradicionais, estreantes e um retorno; Veja os classificados - Fluminense: Últimas notícias, vídeos, onde assistir e próximos jogos28 maio 2024 -
 WARZONE MOBILE - MODO CLASH NO MAPA VERDANSK28 maio 2024
WARZONE MOBILE - MODO CLASH NO MAPA VERDANSK28 maio 2024 -
Mark Hamill interpreta Arthur Pym, na minissérie A Queda da Casa28 maio 2024
-
 Kanan Jarrus, my favorite Jedi personally, by Hugin-Munin : r/StarWarsBattlefront28 maio 2024
Kanan Jarrus, my favorite Jedi personally, by Hugin-Munin : r/StarWarsBattlefront28 maio 2024