Inside ImageTragick: The Real Payloads Being Used to Hack Websites
Por um escritor misterioso
Last updated 30 junho 2024

Get the latest news on how products at Cloudflare are built, technologies used, and join the teams helping to build a better Internet.
ImageMagickの脆弱性(CVE-2016-3714他)についてまとめてみた - piyolog
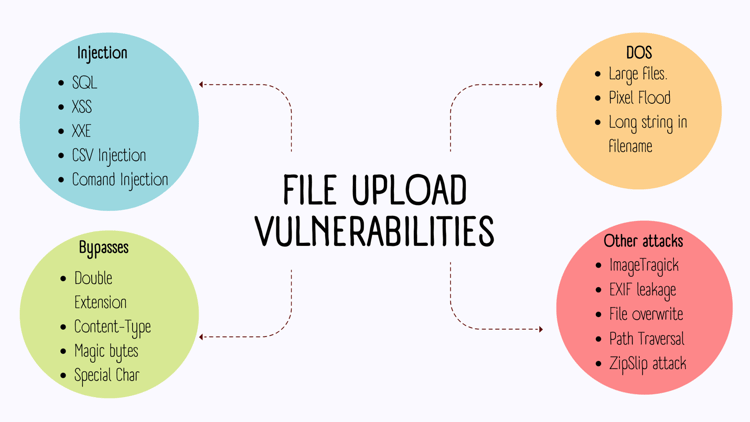
File Upload Vulnerabilities

Warning — Widely Popular ImageMagick Tool Vulnerable to Remo - vulnerability database

Bug Bytes #125 - Nuclei for mobile, ImageTragick like it's 2016 & Intro to HTTP/2 and HTTP/3 - Intigriti

Inside ImageTragick: The Real Payloads Being Used to Hack Websites

Hack The Box — Ariekei Write-up. Ariekei is a Linux machine on Hack The…, by Gabriel Pirjolescu

Cybersecurity: Hacking Windows with Image file Kali Linux

OS Command Injection, Learn AppSec

How I was hacking docker containers by exploiting ImageMagick vulnerabilities
Recomendado para você
-
 ShellShock Live on Steam30 junho 2024
ShellShock Live on Steam30 junho 2024 -
Shellshock.IO Aimbot & ESP30 junho 2024
-
 Shellshock Security Flaw - What is it and how it affects everyone - My Blog30 junho 2024
Shellshock Security Flaw - What is it and how it affects everyone - My Blog30 junho 2024 -
 Hackers exploram bug 'Shellshock' em ataques30 junho 2024
Hackers exploram bug 'Shellshock' em ataques30 junho 2024 -
Buy ShellShock Live - Microsoft Store en-SA30 junho 2024
-
 Latest Shellshock Attack Uses Bashlite to Target Devices Running BusyBox30 junho 2024
Latest Shellshock Attack Uses Bashlite to Target Devices Running BusyBox30 junho 2024 -
 Attacks against Shellshock continue as updated patches hit the Web30 junho 2024
Attacks against Shellshock continue as updated patches hit the Web30 junho 2024 -
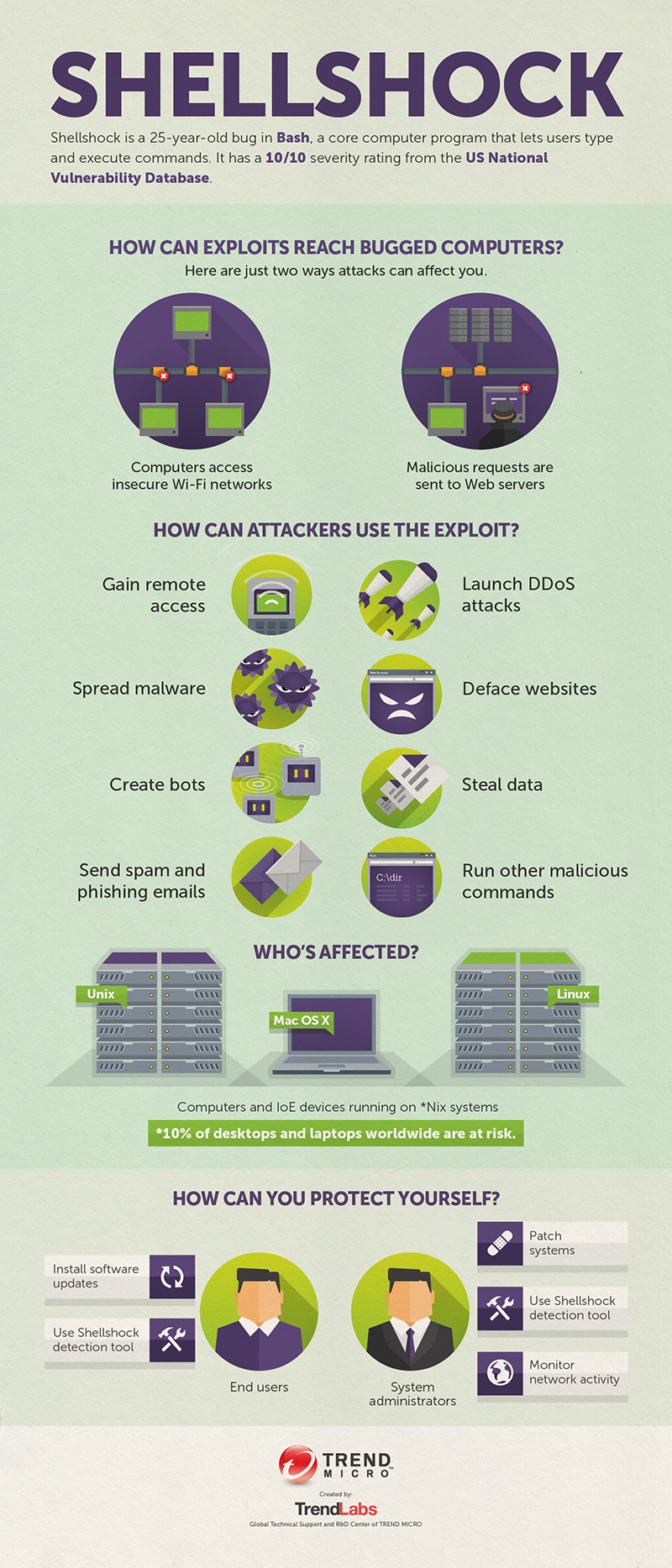 About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Security News30 junho 2024
About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Security News30 junho 2024 -
 Why Shellshock is bad news for the Internet of things - The Washington Post30 junho 2024
Why Shellshock is bad news for the Internet of things - The Washington Post30 junho 2024 -
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/m/v/Q0cd1AQvKA9cNeleW85g/2014-09-29-shellshock2.png) Shellshock: entenda a falha no Bash e saiba como proteger Mac OS e30 junho 2024
Shellshock: entenda a falha no Bash e saiba como proteger Mac OS e30 junho 2024
você pode gostar
-
Saudi Arabia – Team Melli30 junho 2024
-
 Todos os Códigos All Star Tower Defense 30 de junho de 2022 Gemas30 junho 2024
Todos os Códigos All Star Tower Defense 30 de junho de 2022 Gemas30 junho 2024 -
 The GTA 6 trailer countdown has begun., Grand Theft Auto VI / GTA 630 junho 2024
The GTA 6 trailer countdown has begun., Grand Theft Auto VI / GTA 630 junho 2024 -
 so long, good night : ZANGIEF STREET FIGHTER 6 Gameplay Trailer — for30 junho 2024
so long, good night : ZANGIEF STREET FIGHTER 6 Gameplay Trailer — for30 junho 2024 -
 is the italian opening still viable from beginner level to gm? : r/chess30 junho 2024
is the italian opening still viable from beginner level to gm? : r/chess30 junho 2024 -
![KENJA NO MAGO: Quem é Sizilien Von Claude, Noiva de Shin Wolford [Magos Supremos]](https://i.ytimg.com/vi/D2hQNIqH_gQ/maxresdefault.jpg) KENJA NO MAGO: Quem é Sizilien Von Claude, Noiva de Shin Wolford [Magos Supremos]30 junho 2024
KENJA NO MAGO: Quem é Sizilien Von Claude, Noiva de Shin Wolford [Magos Supremos]30 junho 2024 -
:max_bytes(150000):strip_icc()/GettyImages-962142748-5c4bd5bd46e0fb0001ddde78.jpg) The History of Facebook and How It Was Invented30 junho 2024
The History of Facebook and How It Was Invented30 junho 2024 -
 Danny, Evil Dead Rise Sticker for Sale by baitisgreat30 junho 2024
Danny, Evil Dead Rise Sticker for Sale by baitisgreat30 junho 2024 -
Sorry for no posting I had to edit for my other accounts and I30 junho 2024
-
 Chained Echoes Class Emblems guide - all locations - Video Games on Sports Illustrated30 junho 2024
Chained Echoes Class Emblems guide - all locations - Video Games on Sports Illustrated30 junho 2024


