GitHub - tide-foundation/Tide-h4x-for-Privacy: A complete environment utilizing the Tide Protocol used for public audit and hacking bounty
Por um escritor misterioso
Last updated 05 junho 2024
A complete environment utilizing the Tide Protocol used for public audit and hacking bounty - GitHub - tide-foundation/Tide-h4x-for-Privacy: A complete environment utilizing the Tide Protocol used for public audit and hacking bounty
Here's how we protect your private parts - Tide Foundation
How to Brute-Force Email Using a Simple Bash Script (Ft. THC Hydra
Linux Security Exploitation: Attacking HTTP Authentication with

Sensitive information using Github - Bug Hunter Handbook
Tridium Niagara Framework - One Sightsolutions Ltd
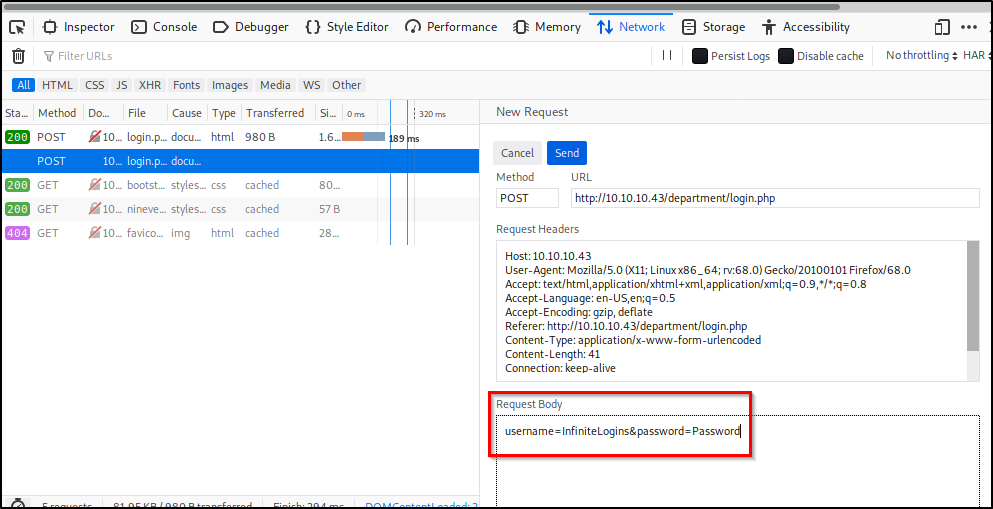
How to Brute Force Websites & Online Forms Using Hydra

New Variant of QakBot Being Spread by HTML File Attached to

Comprehensive Guide on Hydra – A Brute Forcing Tool – đối tác đào
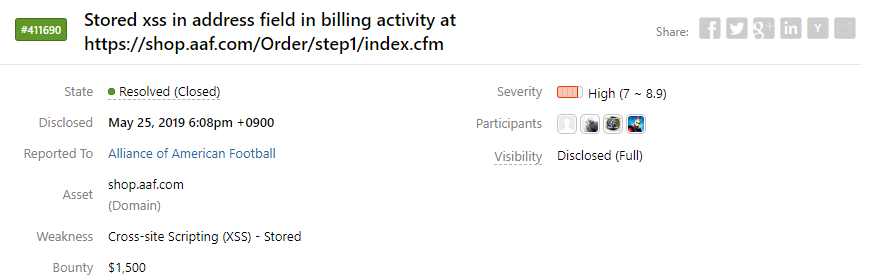
버그바운티(Bug Bounty) Write-up / Stored XSS [AAF] — 보안과 개발을
Tide Foundation · GitHub
GitHub - nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters: A
GitHub - blackhatethicalhacking/Bug_Bounty_Tools_and_Methodology

Configure a Firewall Policy for TDR Traffic
Recomendado para você
-
 H4x by WoodyDotNet on DeviantArt05 junho 2024
H4x by WoodyDotNet on DeviantArt05 junho 2024 -
 FFH4X CRACKED MOD MENU for Android - Download05 junho 2024
FFH4X CRACKED MOD MENU for Android - Download05 junho 2024 -
 FFH4X Regedit APK (Latest Version) v120 Free Download05 junho 2024
FFH4X Regedit APK (Latest Version) v120 Free Download05 junho 2024 -
 FFH4X Injector APK OB38 Download - Latest Version for Android05 junho 2024
FFH4X Injector APK OB38 Download - Latest Version for Android05 junho 2024 -
Silencio H4X - New Update! TR H4X 1.1 Has been Released, subscribe, join to the gruop like to the FB page and, -, 4PP'/, -, 4, <1, \05 junho 2024
-
 GTA V PC Online 1.44.1 H4X Mod Menu - PAID H4X HACK Detected05 junho 2024
GTA V PC Online 1.44.1 H4X Mod Menu - PAID H4X HACK Detected05 junho 2024 -
 FFH4X Mod Menu Fire Hack FFH4 APK Download 2023 - Free - 9Apps05 junho 2024
FFH4X Mod Menu Fire Hack FFH4 APK Download 2023 - Free - 9Apps05 junho 2024 -
 H4X' Men's Premium T-Shirt05 junho 2024
H4X' Men's Premium T-Shirt05 junho 2024 -
App ps team mod menu apk Android app 202205 junho 2024
-
 Garena banned over 2.9 million Free Fire accounts for hacking in the past two weeks05 junho 2024
Garena banned over 2.9 million Free Fire accounts for hacking in the past two weeks05 junho 2024
você pode gostar
-
 Rossmann & Lala - Dibrës - Tirana Health Store - HappyCow05 junho 2024
Rossmann & Lala - Dibrës - Tirana Health Store - HappyCow05 junho 2024 -
 30cm Anime Pokemon Onix Steelix Kawaii Plush Doll Stuffed Toys For Children Gifts - AliExpress05 junho 2024
30cm Anime Pokemon Onix Steelix Kawaii Plush Doll Stuffed Toys For Children Gifts - AliExpress05 junho 2024 -
 Japanese Music Lyrics 205 junho 2024
Japanese Music Lyrics 205 junho 2024 -
 SeriesFlix : Series TV Gratis APK - Baixar app grátis para Android05 junho 2024
SeriesFlix : Series TV Gratis APK - Baixar app grátis para Android05 junho 2024 -
So you think I've gone soft? Love After World Domination English05 junho 2024
-
 Pin de Santray Bartley em Anime & manga references05 junho 2024
Pin de Santray Bartley em Anime & manga references05 junho 2024 -
Ergo Proxy (Clip Promocional) on Vimeo05 junho 2024
-
 Jojo Closeup Of Dio Brando With Black Background HD Anime Wallpapers, HD Wallpapers05 junho 2024
Jojo Closeup Of Dio Brando With Black Background HD Anime Wallpapers, HD Wallpapers05 junho 2024 -
 Oshi no Ko – Dança do Pieyon ganha versão real com a dubladora da Ruby - AnimeNew05 junho 2024
Oshi no Ko – Dança do Pieyon ganha versão real com a dubladora da Ruby - AnimeNew05 junho 2024 -
 mumei (koutetsujou no kabaneri) drawn by qwel_0805 junho 2024
mumei (koutetsujou no kabaneri) drawn by qwel_0805 junho 2024

