11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Last updated 31 outubro 2024

The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.
Why Cloudflare was protected against the SMS phishing attack that
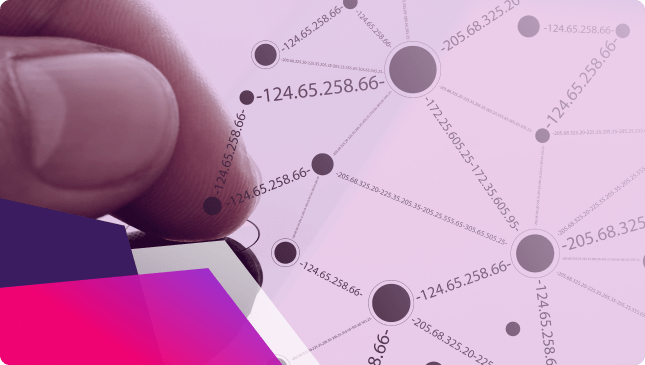
What is IP Spoofing?

Cyber Attacks: Tips for Protecting Your Organisation

6 Common Phishing Attacks and How to Protect Against Them

Sensors, Free Full-Text

10 top anti-phishing tools and services

Attack Methods and Solutions [11].

Spoofing Attacks, Spoofing Vs Phishing

How do Phishing and Spoofing Attacks Impact Businesses?

What Is Spoofing? - Cisco

6 Common Phishing Attacks and How to Protect Against Them

What is Spoofing Attack?

Types of Cyber Security and Cyber Security Threats
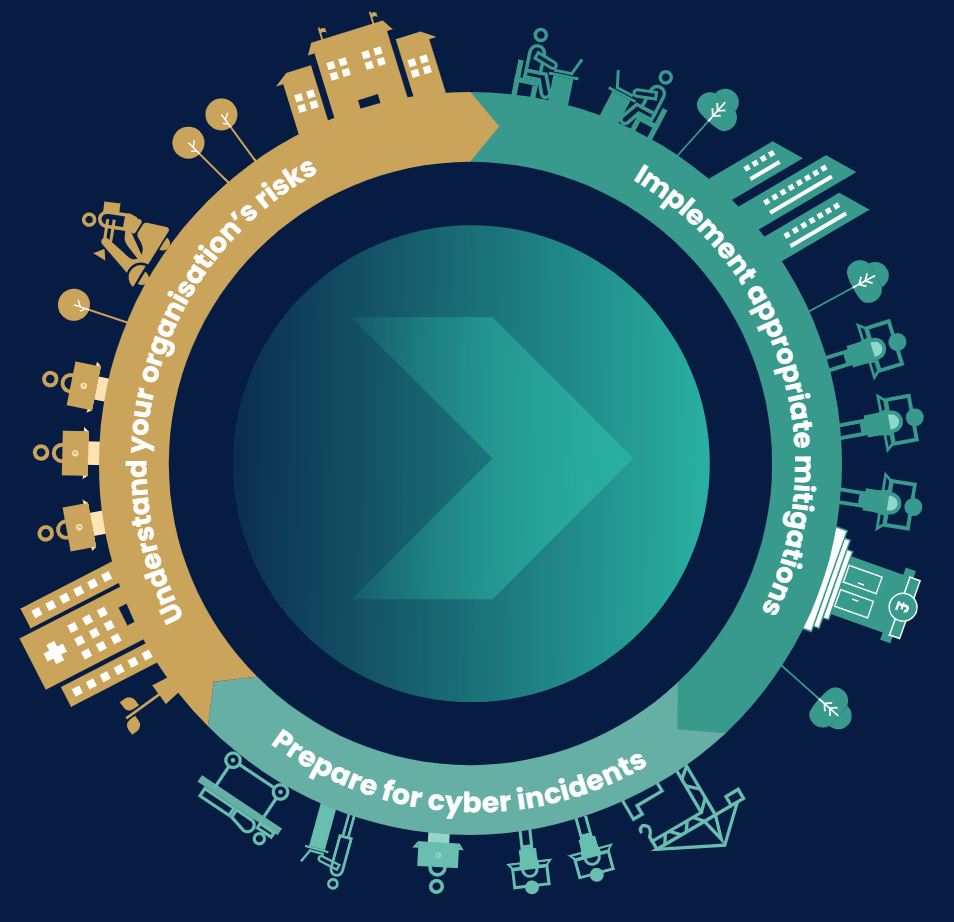
10 Steps to Cyber Security

Must Know Phishing Statistics In 2023 - Attacks And Breaches
Recomendado para você
-
Raj Echambadi on LinkedIn: Illinois Tech's CARNATIONS Receives $1031 outubro 2024
-
 James the Red Engine, Movie Spoof Films Wikia31 outubro 2024
James the Red Engine, Movie Spoof Films Wikia31 outubro 2024 -
 Nobody's Fool: Spoofing Detection in a High-Precision Receiver31 outubro 2024
Nobody's Fool: Spoofing Detection in a High-Precision Receiver31 outubro 2024 -
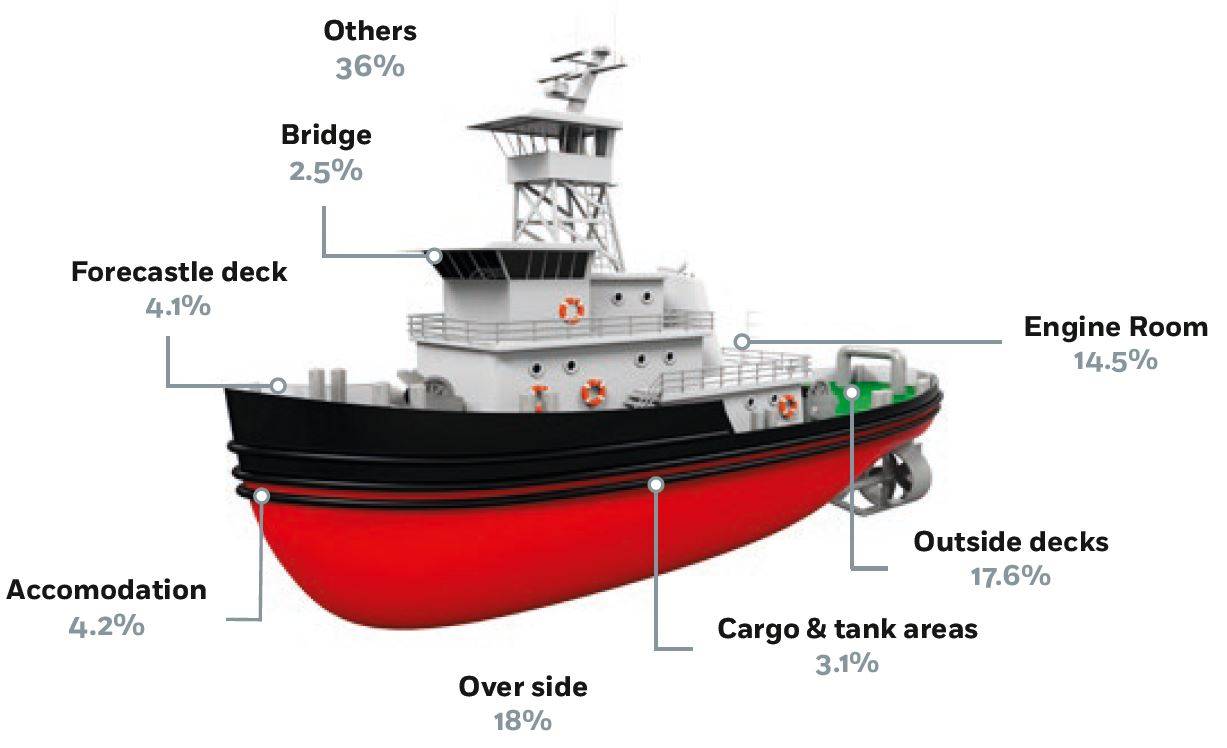 Autonomous Shipping – Cyber Hazards Ahead31 outubro 2024
Autonomous Shipping – Cyber Hazards Ahead31 outubro 2024 -
 Location Spoofing, Detect Fake GPS Location31 outubro 2024
Location Spoofing, Detect Fake GPS Location31 outubro 2024 -
 How Do MAC Spoofing Attacks Work?31 outubro 2024
How Do MAC Spoofing Attacks Work?31 outubro 2024 -
HookSpoofer: The Modified Open Source Stealer Bundlers Making the Rounds31 outubro 2024
-
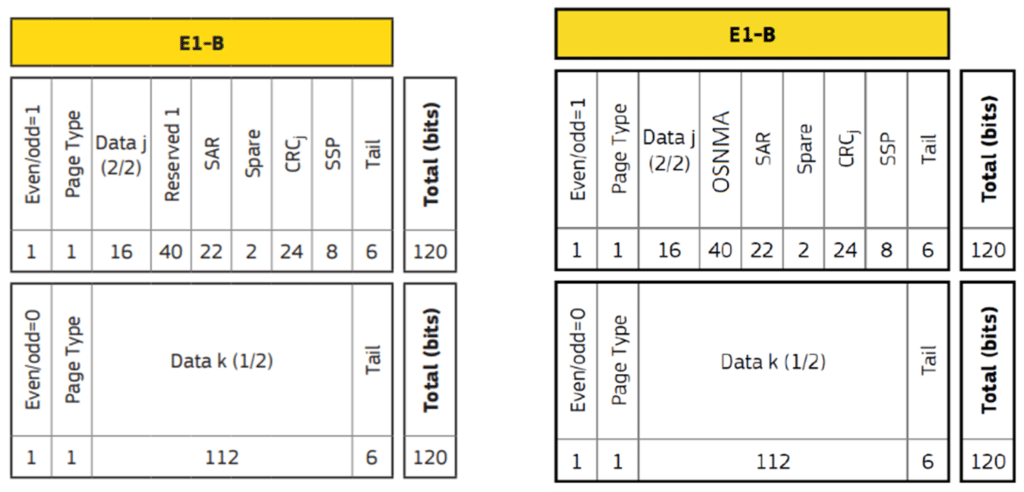 Testing a Receiver's Galileo OS-NMA Capability Using Skydel31 outubro 2024
Testing a Receiver's Galileo OS-NMA Capability Using Skydel31 outubro 2024 -
 Autonomous aerial robotics for package delivery: A technical31 outubro 2024
Autonomous aerial robotics for package delivery: A technical31 outubro 2024 -
 Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum31 outubro 2024
Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum31 outubro 2024
você pode gostar
-
 SHORT LIFE - Jogue Grátis Online!31 outubro 2024
SHORT LIFE - Jogue Grátis Online!31 outubro 2024 -
 Chef Dan Galhardo on X: Cheetos bola com Ketchup. Passa ou Amassa31 outubro 2024
Chef Dan Galhardo on X: Cheetos bola com Ketchup. Passa ou Amassa31 outubro 2024 -
 How to download GTA 5 Mobile with all Features - TechBullion31 outubro 2024
How to download GTA 5 Mobile with all Features - TechBullion31 outubro 2024 -
 Jogo PS5 The Persistence Enhanced Mídia Física Novo Lacrado - THQ - Jogos PS5 - Magazine Luiza31 outubro 2024
Jogo PS5 The Persistence Enhanced Mídia Física Novo Lacrado - THQ - Jogos PS5 - Magazine Luiza31 outubro 2024 -
![Epic Wubbox? [Ephex the Wubbox] by Axoli on DeviantArt](https://images-wixmp-ed30a86b8c4ca887773594c2.wixmp.com/f/873b0062-7cb0-4f7d-80f9-47288dec522a/dedhfl2-f0a5cd9e-1476-462e-94bd-dad2adc44384.png?token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1cm46YXBwOjdlMGQxODg5ODIyNjQzNzNhNWYwZDQxNWVhMGQyNmUwIiwiaXNzIjoidXJuOmFwcDo3ZTBkMTg4OTgyMjY0MzczYTVmMGQ0MTVlYTBkMjZlMCIsIm9iaiI6W1t7InBhdGgiOiJcL2ZcLzg3M2IwMDYyLTdjYjAtNGY3ZC04MGY5LTQ3Mjg4ZGVjNTIyYVwvZGVkaGZsMi1mMGE1Y2Q5ZS0xNDc2LTQ2MmUtOTRiZC1kYWQyYWRjNDQzODQucG5nIn1dXSwiYXVkIjpbInVybjpzZXJ2aWNlOmZpbGUuZG93bmxvYWQiXX0.TMDYB3KyhJMrH4rIwSeD-H40N76eU34WxQK4q5M4Yc0) Epic Wubbox? [Ephex the Wubbox] by Axoli on DeviantArt31 outubro 2024
Epic Wubbox? [Ephex the Wubbox] by Axoli on DeviantArt31 outubro 2024 -
 Como fazer roupas para barbie com meia31 outubro 2024
Como fazer roupas para barbie com meia31 outubro 2024 -
 Fototapete Hexagon Muster 3D Effekt Grau Beige 3,50 m x 2,55 m FSC31 outubro 2024
Fototapete Hexagon Muster 3D Effekt Grau Beige 3,50 m x 2,55 m FSC31 outubro 2024 -
 Steve Harvey gets meme'd into IPs like JoJo's Bizarre Adventure and Dragon Ball Z as internet loses it over his new wardrobe31 outubro 2024
Steve Harvey gets meme'd into IPs like JoJo's Bizarre Adventure and Dragon Ball Z as internet loses it over his new wardrobe31 outubro 2024 -
Garment Textile Machinery, Allied Products & Accessories Trade Show under name & style GTMAT Bangladesh-2016.(31 outubro 2024
-
 Xeque-mate: campeonato de xadrez acontece dia 17 no Tubão, em Ubatuba – Tamoios News31 outubro 2024
Xeque-mate: campeonato de xadrez acontece dia 17 no Tubão, em Ubatuba – Tamoios News31 outubro 2024

