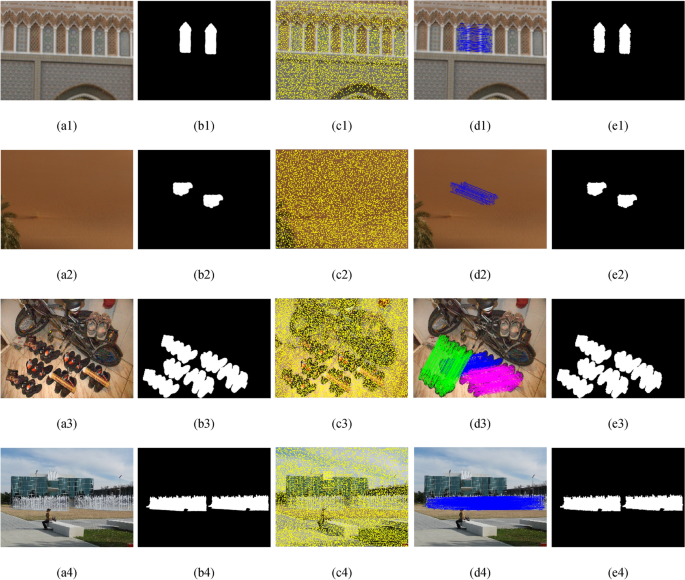
a1), {(b1)-(c1)}, (d1), (e1), and {(f1)-(g1)} shows copy-move forged
Por um escritor misterioso
Last updated 30 maio 2024

GitHub - niyishakapatrick/Copy-move-forgery-detection-using-image-blobs-BRISK-features.: One of the most frequently used types of digital image forgery is copying one area in the image and pasting it into another area of the same image. This

PDF] Copy-Move Forgery Detection Utilizing Local Binary Patterns

lightning web components - Error ssl reason: write EPROTO and wrong version number - Salesforce Stack Exchange
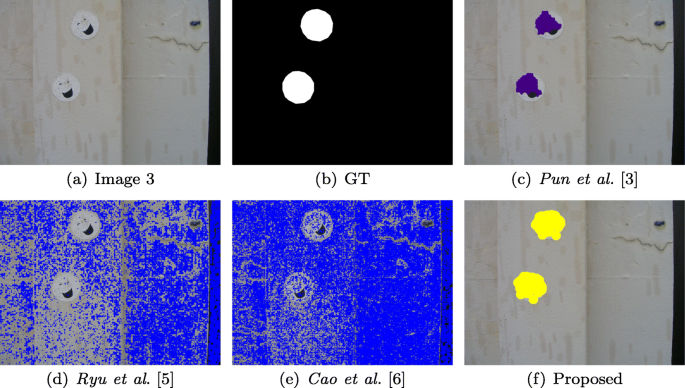
The first five examples for Copy-Move forgery detection: original

PDF] Copy-Move Forgery Detection Utilizing Local Binary Patterns
FAST, BRIEF and SIFT based image copy-move forgery detection technique
Robust and effective multiple copy-move forgeries detection and localization
Solved Which one of the following formulas will work if
Copy-Move Forgery Detection Based on Discrete and SURF Transforms
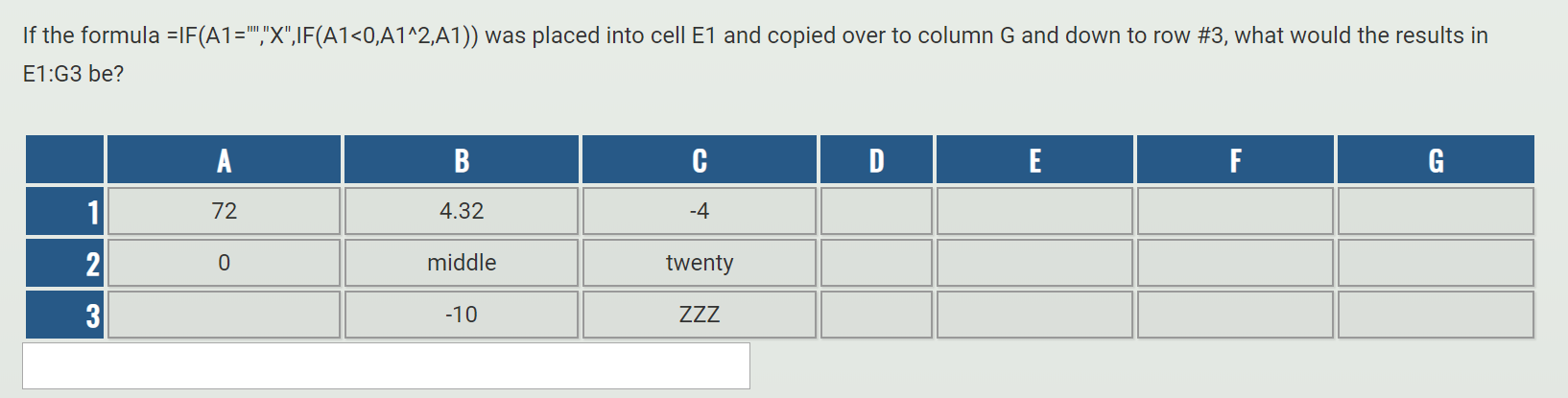
Solved If the formula =IF(A1=,X,IF(A1<0,01^2,A1)) was
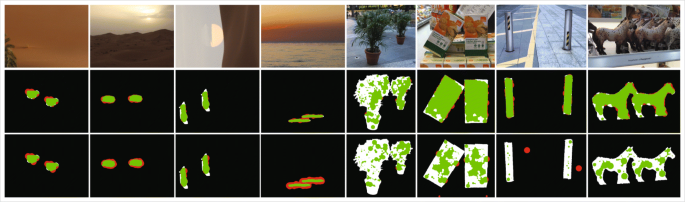
Copy-move image forgery detection based on evolving circular domains coverage
Recomendado para você
-
 Slapdash Powermaster - 1988 Vintage G1 Transformers Formula-1 Action Figure - Wheeljack's Lab30 maio 2024
Slapdash Powermaster - 1988 Vintage G1 Transformers Formula-1 Action Figure - Wheeljack's Lab30 maio 2024 -
 Powerdashers F1 Dasher (Transformers, G1, Autobot)30 maio 2024
Powerdashers F1 Dasher (Transformers, G1, Autobot)30 maio 2024 -
 Made a G1 mirage livery for the RB14 f1 car : r/transformers30 maio 2024
Made a G1 mirage livery for the RB14 f1 car : r/transformers30 maio 2024 -
 XRT136 Replacement Remote Control fit for VIZIO Smart TV 2019 LCD LED HDTV D24h-G9 D24hn-g9 D32h-G9 D40f-g9 D50x-g9 PQ65-F1 PQ75-F1 PX65-G1 PX75-G130 maio 2024
XRT136 Replacement Remote Control fit for VIZIO Smart TV 2019 LCD LED HDTV D24h-G9 D24hn-g9 D32h-G9 D40f-g9 D50x-g9 PQ65-F1 PQ75-F1 PX65-G1 PX75-G130 maio 2024 -
 Transformers G1 POWERDASHER F1 car (mail away), This guy is…, OpTILLmus30 maio 2024
Transformers G1 POWERDASHER F1 car (mail away), This guy is…, OpTILLmus30 maio 2024 -
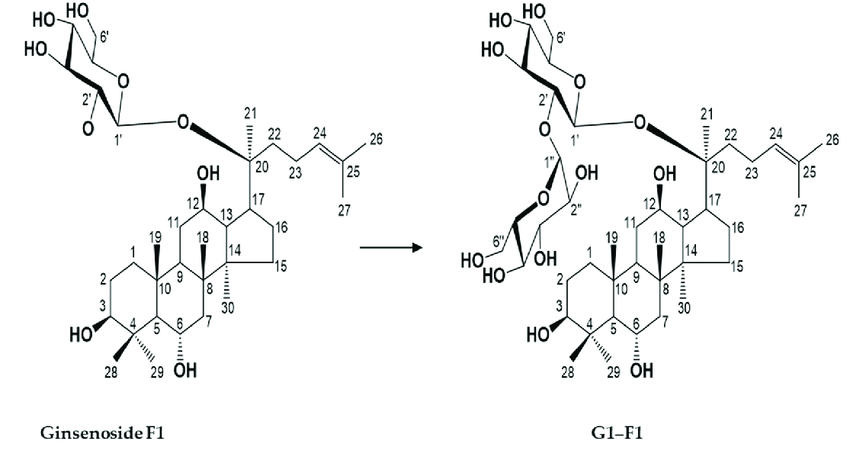 Chemical structures of ginsenoside F1 and its α-glycosylated F1(G1-F1).30 maio 2024
Chemical structures of ginsenoside F1 and its α-glycosylated F1(G1-F1).30 maio 2024 -
 Transformation G1 Element TE03 TE-03 Version 2.0 MP F1 Mirage Action Figure In Stock With Box Sticker IN STOCK30 maio 2024
Transformation G1 Element TE03 TE-03 Version 2.0 MP F1 Mirage Action Figure In Stock With Box Sticker IN STOCK30 maio 2024 -
 Agarose gel electrophoresis of crude DNA (F1 & G1) and universal PCR30 maio 2024
Agarose gel electrophoresis of crude DNA (F1 & G1) and universal PCR30 maio 2024 -
 Griiip strikes first broadcast deal for disruptive race car series30 maio 2024
Griiip strikes first broadcast deal for disruptive race car series30 maio 2024 -
 F-Classic G1 M130 maio 2024
F-Classic G1 M130 maio 2024
você pode gostar
-
 What's On Steam - 3D Aim Trainer30 maio 2024
What's On Steam - 3D Aim Trainer30 maio 2024 -
 Wizard of Legend 2 Announced; 3D with Full Multiplayer Support - MP1st30 maio 2024
Wizard of Legend 2 Announced; 3D with Full Multiplayer Support - MP1st30 maio 2024 -
 A Fake Chess Photograph (Edward Winter)30 maio 2024
A Fake Chess Photograph (Edward Winter)30 maio 2024 -
 FROZEN 3 (2025) Latest Updates!30 maio 2024
FROZEN 3 (2025) Latest Updates!30 maio 2024 -
Hello Kitty Cafe Las Vegas - Our new blueberry lemonade is so30 maio 2024
-
 Betty Bowen Award Archives - SAMBlog30 maio 2024
Betty Bowen Award Archives - SAMBlog30 maio 2024 -
 xadrez online multiplayer·telegram:@ehseo6·ⓔ⅜㊮•enry - Search - EasyEDA30 maio 2024
xadrez online multiplayer·telegram:@ehseo6·ⓔ⅜㊮•enry - Search - EasyEDA30 maio 2024 -
 Pin de Rafaela Arlequina em itachi uchiha30 maio 2024
Pin de Rafaela Arlequina em itachi uchiha30 maio 2024 -
Teoria bizarra por trás de subway surfers 😳 insta: mayuminkuramoto #30 maio 2024
-
 Japan Game Awards:201630 maio 2024
Japan Game Awards:201630 maio 2024

