Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Last updated 05 junho 2024
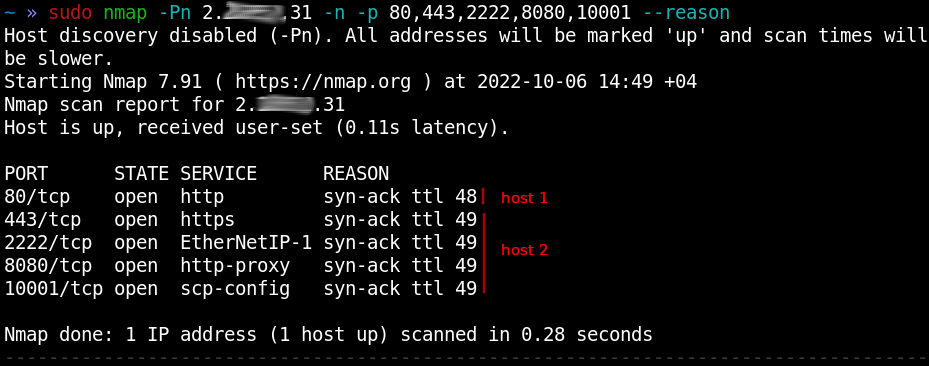
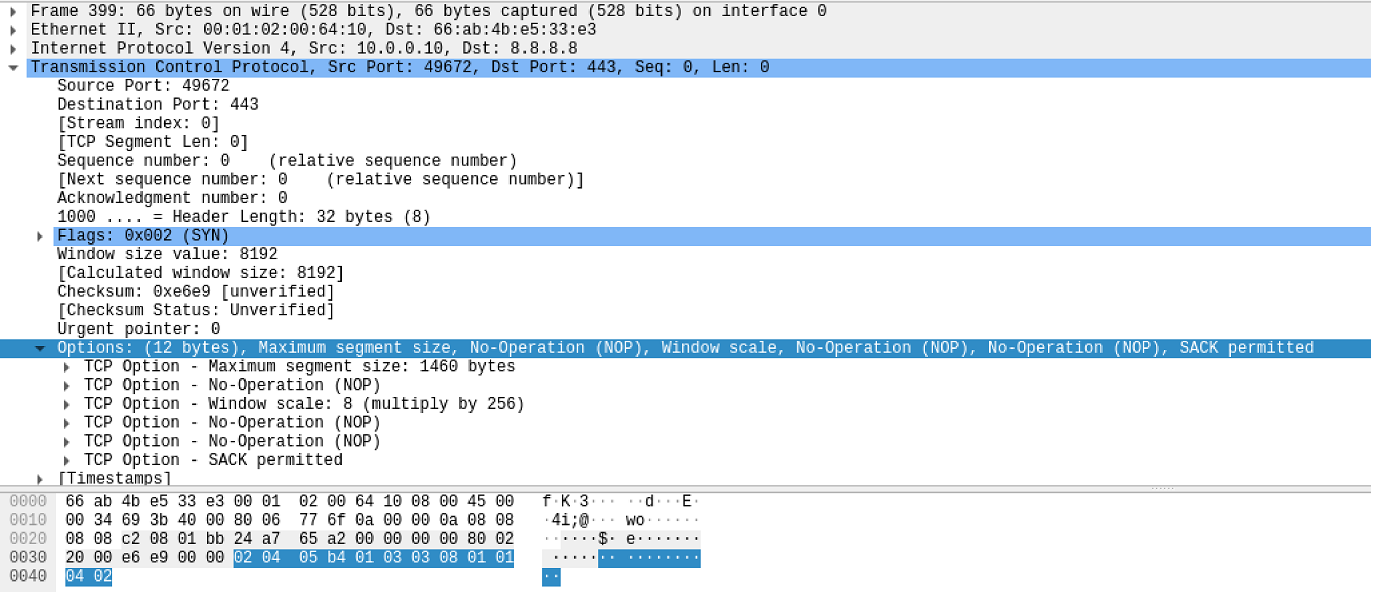
Kung fu enumeration. Data collection in attacked systems – HackMag
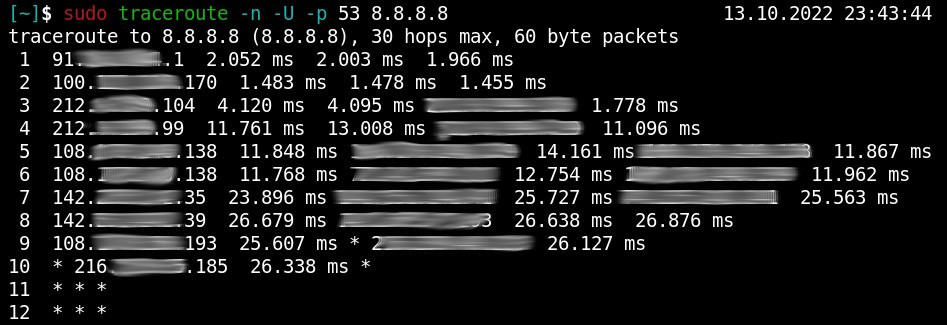
Kung fu enumeration. Data collection in attacked systems – HackMag
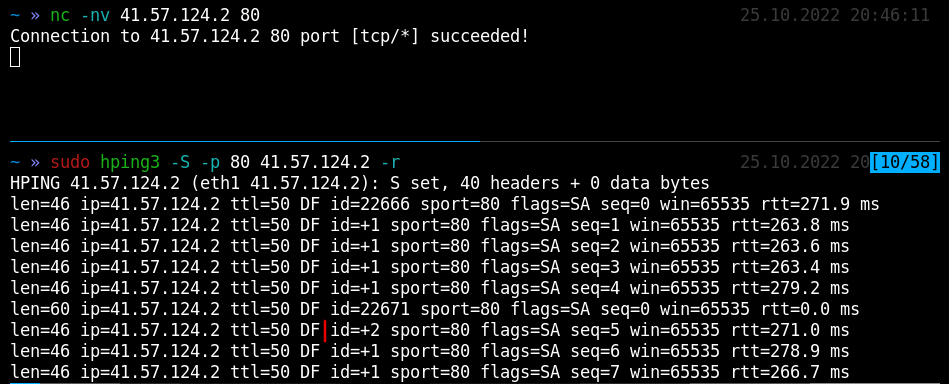
Kung fu enumeration. Data collection in attacked systems – HackMag

HACKMAGEDDON – Information Security Timelines and Statistics

HACKMAGEDDON – Information Security Timelines and Statistics

Hammond - Unit 17 Homework - GoodSecurity Penetration Test Report

Counter Hack Reloaded: A Step-by-Step Guide to Computer Attacks
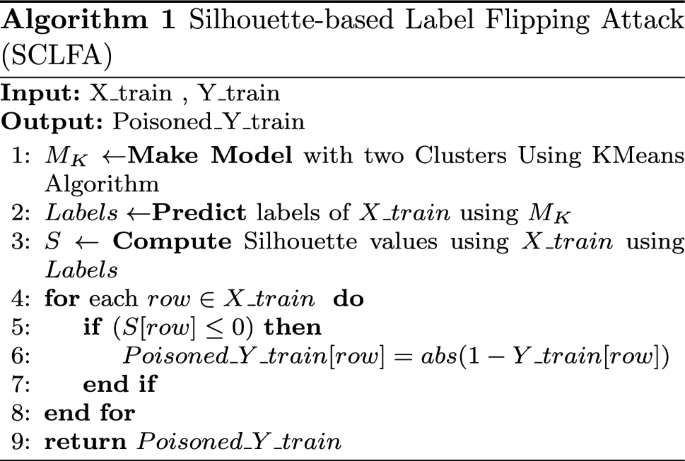
On defending against label flipping attacks on malware detection

Chinese Stole Anthem Data For HUMINT; Should Raise US 'Hackles
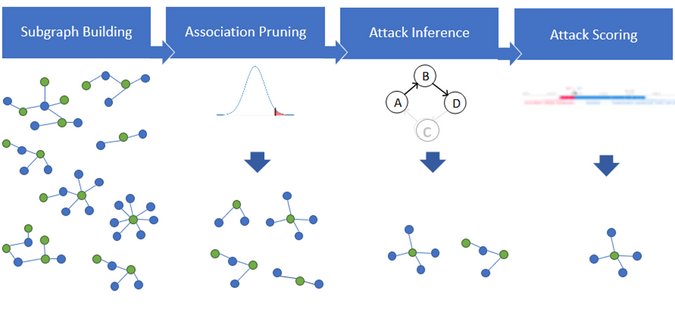
Behind the Scenes: The ML Approach for Detecting Advanced
AppSec Ezines Url ( from
Recomendado para você
-
1. SCP-10001俺のせいだ(自作), 全1話 (作者:大鳥)の連載小説05 junho 2024
-
 Church of Maxwellism SCP Foundation | Art Board Print05 junho 2024
Church of Maxwellism SCP Foundation | Art Board Print05 junho 2024 -
 SCP-5772 - SCP Foundation05 junho 2024
SCP-5772 - SCP Foundation05 junho 2024 -
Mummy Ana!! Yay for spooky season 😭🍂! #overwatchfanart05 junho 2024
-
 171790-001 / ASSY,I/O ADDR 2 / SCP SERVICES05 junho 2024
171790-001 / ASSY,I/O ADDR 2 / SCP SERVICES05 junho 2024 -
Talisman Books & Gallery05 junho 2024
-
 CyberCrime - 500+ Patches for Omnisphere - SampleHero - Virtual Instruments05 junho 2024
CyberCrime - 500+ Patches for Omnisphere - SampleHero - Virtual Instruments05 junho 2024 -
 Meltec SCP-1200 Fully Automatic Pulse Charger, Electronics Parts05 junho 2024
Meltec SCP-1200 Fully Automatic Pulse Charger, Electronics Parts05 junho 2024 -
 Game Jolt - Share your creations05 junho 2024
Game Jolt - Share your creations05 junho 2024 -
 Pixel Art — Shrinking. Painting a small image pixel by pixel…, by Joana Borges Late05 junho 2024
Pixel Art — Shrinking. Painting a small image pixel by pixel…, by Joana Borges Late05 junho 2024
você pode gostar
-
FREE steam games to play when bored ig #tech #pc #techtok #setup #gami05 junho 2024
-
 Tricoline estampado bolos fundo xadrez rosa - Renatta Tecidos05 junho 2024
Tricoline estampado bolos fundo xadrez rosa - Renatta Tecidos05 junho 2024 -
 RoPro - Enhance Your Roblox Experience para Google Chrome05 junho 2024
RoPro - Enhance Your Roblox Experience para Google Chrome05 junho 2024 -
 Marvel's Spider-Man 2 VGM56 Spider-Man (Black Suit) 1/6th Scale05 junho 2024
Marvel's Spider-Man 2 VGM56 Spider-Man (Black Suit) 1/6th Scale05 junho 2024 -
:max_bytes(150000):strip_icc():focal(1259x415:1261x417)/biggie-smalls-2000-4643da829b024ed1a4307cccf0736374.jpg) Watch the Notorious B.I.G. Documentary Trailer05 junho 2024
Watch the Notorious B.I.G. Documentary Trailer05 junho 2024 -
 Roblox Man Face T-Shirts for Sale05 junho 2024
Roblox Man Face T-Shirts for Sale05 junho 2024 -
 153,100 Pic Of A Dragon Stock Photos, High-Res Pictures, and05 junho 2024
153,100 Pic Of A Dragon Stock Photos, High-Res Pictures, and05 junho 2024 -
 Biofaces - Bring Nature Closer05 junho 2024
Biofaces - Bring Nature Closer05 junho 2024 -
 2023 garten de banban brinquedos de pelúcia jumbo josh anime monstro capitão fiddles animais de pelúcia05 junho 2024
2023 garten de banban brinquedos de pelúcia jumbo josh anime monstro capitão fiddles animais de pelúcia05 junho 2024 -
Infinite transcendence>#fypシ #foryou #anime #animethings #fiction05 junho 2024



